How to pass 70-342 exam easily? Are you struggling for the 70-342 exam? Good news, GreatExam Microsoft technical experts have collected all the questions and answers which are updated to cover the knowledge points and enhance candidates’ abilities. We offer the latest 70-342 PDF and VCE dumps with new version VCE player for free download, and the new 70-342 practice test ensures your 70-342 exam 100% pass.
QUESTION 106
Your company has an Exchange Server 2013 organization named Contoso.
A partner company has an Exchange Server 2013 organization named Fabrikam.
Neither company has any trusts between their forests.
Users from both organizations access their mailbox from the Internet by using Outlook Anywhere.
You need to ensure that the users from both organizations can share free/busy information.
Which two cmdlets should you run? (Each correct answer presents part of the solution. Choose two.)
A. New-AcceptedDomain
B. Add-AvailabilttyAddressSpace
C. Set-AvailabilityConfig
D. New-SharingPolicy
E. Add-ADPermission
Answer: BD
Explanation
B: Use the Add-AvailabilityAddressSpace cmdlet to define the access method and associated credentials used to exchange free/busy data across forests.
D: Use the New-SharingPolicy cmdlet to create a sharing policy to regulate how users inside your organization can share calendar and contact information with users outside the organization.
Users can only share this information after federation has been configured in Exchange.
http://technet.microsoft.com/en-us/library/bb124122%28v=exchg.150%29.aspx
http://technet.microsoft.com/en-us/library/dd298186%28v=exchg.150%29.aspx
QUESTION 107
A company named Contoso, Ltd., has an Exchange Server 2013 organization.
The primary SMTP suffix for all users is contoso.com.
A company named Fabrikam, Inc., has an Exchange Server 2010 organization.
The primary SMTP suffix for all users is fabrikam.com.
The users in both organizations access their email by using Microsoft Outlook 2010 and Outlook Anywhere. All of the users work from domain-joined client computers that connect to the internal network.
Contoso acquires Fabrikam.
You establish a cross-forest trust between the Contoso forest and the Fabrikam forest.
In fabrikam.com, you create a user named User1.
In contoso.com, you create a linked mailbox for User1 and you set the primary SMTP address to [email protected].
User1 reports that Outlook 2010 fails to configure his mail profile automatically.
User1 can manually configure his profile and connect to his mailbox.
You need to ensure that users in fabrikam.com can find their mailboxes automatically.
What should you do in contoso.com?
A. Create a DNS record named autodiscover.fabrikam.com.
Point the record to the virtual IP address of the Client Access servers.
B. Modify the ExternalURL of the Autodiscover virtual directory on the Exchange Servers 2013 servers.
C. Modify the Autodiscover Service Connection Point (SCP).
D. Run the Export-AutoDiscoverConfig cmdlet on an Exchange Server 2013 server.
Answer: D
Explanation:
You can configure Microsoft Exchange services, such as the Availability service, for the Autodiscover service on a Microsoft Exchange Server 2010 Client Access server.
When you enable Outlook Anywhere, you must also configure external client access to Microsoft Exchange services for the Autodiscover service. Other external URLS you must configure include the URLs for the Availability service, Exchange Web Services, Unified Messaging (UM), and the offline address book.
QUESTION 108
You have an Exchange Server 2013 organization that contains 10 servers.
You have a federation trust to the Microsoft Federation Gateway.
The certificate in the trust relationship expires soon.
You need to replace the certificate. The solution must minimize downtime.
You purchase a new certificate.
What should you do next?
A. On all of the Exchange servers, import the certificate, and then run the New- FederationTrust cmdlet.
B. On all of the Exchange servers, import the certificate, and then run the Set- OrganizationRelationship cmdlet.
C. On one of the Exchange servers, import the certificate, and then run the Set- FederationTmst cmdlet.
D. On one of the Exchange servers, import the certificate, and then run the Set- FederatedOrganizationldentifier cmdlet.
Answer: C
Explanation:
You can use the Set-FederationTrust cmdlet to manage the certificates used for the federation trust. You can also use the Set-FederationTrust cmdlet to refresh the metadata document from the Microsoft Federation Gateway and download its certificate.
http://technet.microsoft.com/en-us/library/dd876922%28v=exchg.141%29.aspx
QUESTION 109
Drag and Drop Question
You work for a financial services company that has an Exchange Server 2013 organization.
Mailbox audit logging is enabled for all mailboxes.
The company identifies the following requirements for the sales department:
– The manager of the sales department must be able to search for email messages that contain specific key words in the mailboxes of the users in the sales department.
– The manager of the human resources department must receive a report that contains a list of all the sales users’ mailboxes that were searched by the sales manager.
You need to identify which tasks must be performed to meet the requirements.
Which tasks should you identify? To answer, drag the appropriate task to the correct requirement in the answer area. Each task may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.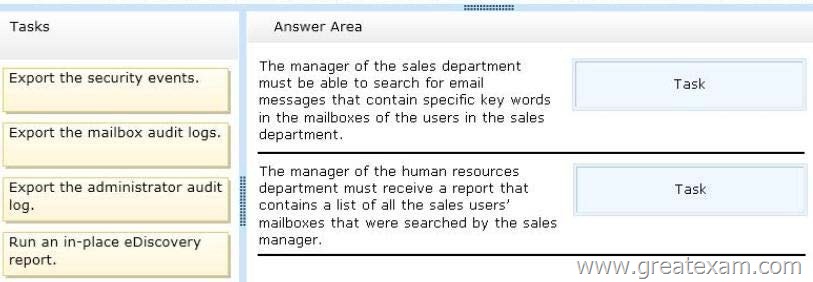
Answer: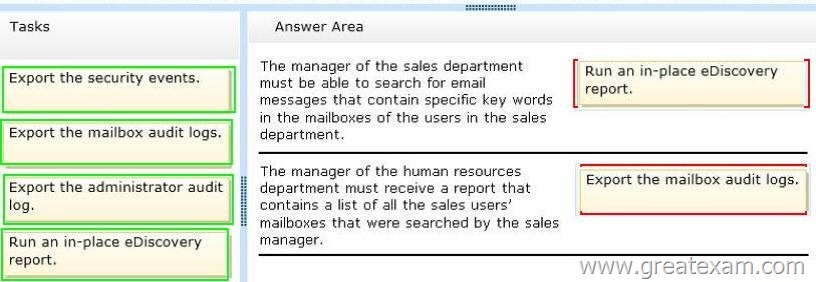
QUESTION 110
You have an Exchange Server 2013 organization that contains one office in Los Angeles and one office in New York. All servers have the Mailbox server role and the Client Access server role installed and are members of a data availability group (DAG) named DAG1.
The servers and databases are shown in the exhibit. (Click the Exhibit button.)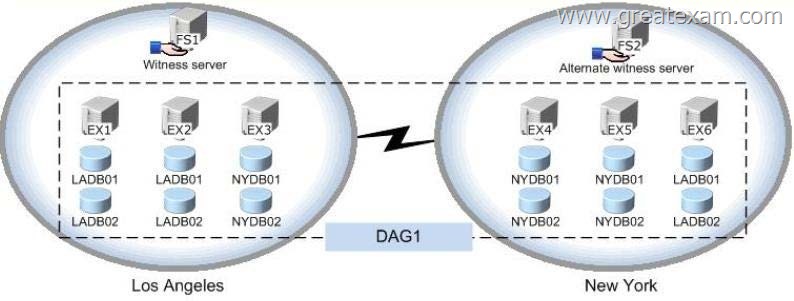
You need to ensure that if the active copy of LADB01 fails, a server in the same site will attempt to activate a copy of the database before a server in another site does. The solution must not influence the activation of other database copies.
Which command should you run?
A. Set-databaseavailabilitygroupserver -identity dagl-alternatewitnessserverfs2
B. Set-mailboxserver-identity ex6 autodatabasemountdial bestavailability
C. Suspend-mailboxdatabasecopy-identity Iadb01\ex6 -activationonly
D. Set-mailboxdatabasecopy -identity Iadb01\ex2-activationpreferencel
Answer: D
Explanation:
Use the Set-MailboxDatabaseCopy cmdlet to configure the properties of a database copy.
With this cmdlet, you can configure the replay lag time, truncation lag time, and activation
preference value for a mailbox database copy.
/ activationpreference
The ActivationPreference parameter value is used as part of Active Manager’s best copy selection process and to redistribute active mailbox databases throughout the database availability group (DAG) when using the RedistributeActiveDatabases.ps1 script.
The value for the ActivationPreference parameter is a number equal to or greater than 1, where 1 is at the top of the preference order. The position number can’t be larger than the number of database copies of the mailbox database.
Incorrect:
Not C: Use the Suspend-MailboxDatabaseCopy cmdlet to block replication and replay activities (log copying and replay) or activation for a database configured with two or more database copies.
/ Identity
The Identity parameter specifies the name of the database copy being suspended.
/ ActivationOnly
The ActivationOnly switch specifies whether to suspend only activation for the mailbox database copy.
QUESTION 111
Your company has offices in Montreal, New York, and Toronto.
Each office is configured as an Active Directory site. The Montreal office has a site link to the New York office. The New York office has a site link to the Toronto office.
You have an Exchange Server 2013 organization that contains five Mailbox servers.
The organization is configured as shown in the exhibit. (Click the Exhibit button.)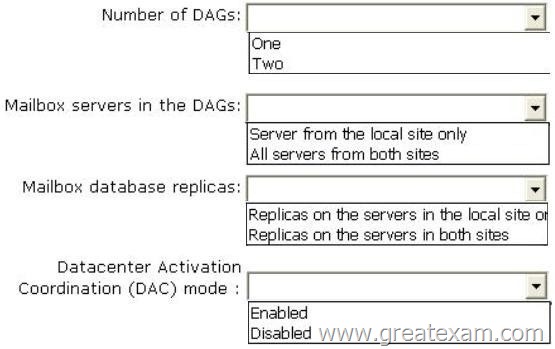
The servers in the Montreal and Toronto offices are members of a database availability group (DAG) named DAG01. DAG01 contains two databases name TOMBX and MTLMBX. MTLMBX is active on EX1 and contains all of the mailboxes of the users in the Montreal office. TOMBX is active on EX3 and contains all of the mailboxes of the users in the Toronto office.
You need to ensure that all email messages transmitted between the Montreal users and the Toronto users are routed through EX5.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Run the Set-MailboxTransportService cmdlet on EX5.
B. Make EX5 the source server for all of the Send connectors.
C. Create a separate DAG for each of the Montreal and Toronto offices.
D. Add EXS to DAG01.
E. Configure the New York office as a hub site.
Answer: CE
Explanation:
As the respective location’s mailboxes are on the primary mailboxserver in each location, you can make a DAG just for that location. Other location’s users don’t need to be able to reach the other location in order to ‘see’ their mailboxes.
Configuring a hub-site routes all messages through this site.
http://technet.microsoft.com/en-us/library/jj916681%28v=exchg.150%29.aspx#HubSites
QUESTION 112
You are a network administrator for a company named Contoso, Ltd.
You install the Active Directory Rights Management Services server role on a server. The Active Directory Rights Management Services (AD RMS) server uses an internal certification authority (CA) for all certificates.
You plan to provide users with the ability to use AD RMS to protect all of the email messages sent to a partner company named A.Datum Corporation. A.Datum does not have AD RMS deployed. You need to identify which components from the Contoso network must be accessible to A.Datum to ensure that the users at A.Datum can open protected messages.
Which two components should you identify? (Each correct answer presents part of the solution. Choose two.)
A. The Active Directory domain controllers
B. The Client Access servers
C. The certificate revocation list (CRL)
D. The Mailbox servers
Answer: AC
Explanation:
A: Active Directory Rights Management Services (AD RMS) requires at least one Active Directory domain controller.
C: As a local CA is used we need access to the CRL.
QUESTION 113
You hire a junior administrator named Admin5.
Admin5 is a member of the Recipient Management management role group.
You discover that Admin5 created two new mailbox-enabled users by using the New-Mailbox command.
You need to identify which management role provides Admin5 with the permissions to create new mailbox-enabled users.
Which cmdlets should you run?
A. Get-ManagementRoleEntry and Get-RoleAssignmentPolicy
B. Get-Rolegroup and Get-ManagementRoleAssignment
C. Get-ManagementRoleEntry a-d Get-ManagementRoleAssignment
D. Get-RolegroupMember and Get-ManagementRoleAssignment
Answer: C
Explanation:
* Use the Get-ManagementRoleEntry cmdlet to retrieve management role entries that have been configured on management roles.
* Use the Get-ManagementRoleAssignment cmdlet to retrieve management role assignments.
QUESTION 114
You have an Exchange Server 2013 organization that contains one Client Access server named EX1 and one Mailbox server named EX2.
You have a perimeter network and an internal network. The perimeter network contains an Edge Transport server named EX3 that has Exchange Server 2010 installed.
You need to ensure that all of the email messages sent to and received from the Internet are routed through the EX3.
Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. Allow SMTP traffic between EX3 and EX2.
B. Create an Edge Subscription.
C. Allow traffic over TCP 50636 from EX1 to EX3.
D. Allow SMTP traffic between EX3 and EX1.
E. Allow traffic over TCP 50636 from EX2 to EX3.
F. Modify the default Receive connector on EX2.
Answer: ABE
Explanation:
To establish Internet mail through an Edge Transport server, subscribe the Edge Transport server to an Active Directory site. This automatically creates the two Send connectors required for Internet mail flow:
A Send connector configured to send outbound email to all Internet domains.
A Send connector configured to send inbound email from the Edge Transport server to an Exchange 2013 Mailbox server.
SMTP traffic and ports TCP 50636 must be allowed between the mailbox server (routing service) and the Edge server.
http://technet.microsoft.com/en-us/library/jj150569%28v=exchg.150%29.aspx
QUESTION 115
You are an administrator for a company named Contoso, Ltd. Contoso has an Exchange Server 2013 organization. Contoso has a partnership agreement with a company named A.Datum
Corporation. A.Datum has an Exchange server 2013 organization.
Both organizations have a federation trust to the Microsoft Federation Gateway.
Users at Contoso plan to share their free/busy information with users at A.Datum.
You need to recommend which tasks must be performed to ensure that the A.Datum users can see the free/busy information of the Contoso users.
Which two actions should you recommend?
(Each correct answer presents part of the solution. Choose two.)
A. In the Exchange Server organization of Contoso, configure directory synchronization.
B. In the Exchange Server organization of A. Datum, create a sharing policy.
C. In the Exchange Server organization of A. Datum, configure directory synchronization.
D. In the Exchange Server organization of Contoso, create an organization relationship.
E. In the Exchange Server organization of Contoso, create a sharing policy.
F. In the Exchange Server organization of A. Datum, create an organization relationship.
Answer: DE
Explanation:
Configure Federated Sharing
Step 1: Create and configure a federation trust
(this has already been done here)
Step 2 (D): Create an organization relationship
An organization relationship enables users in your Exchange organization to share calendar free/busy information as part of federated sharing with other federated Exchange organizations.
Step 3 (E): Create a sharing policy
Sharing policies enable user-established, people-to-people sharing of both calendar and contact information with different types of external users. They support the sharing of calendar and contact information with external federated organizations, external non- federated organizations, and individuals with Internet access. If you don’t need to configure people-to-people or contact sharing (organization-level sharing only), you don’t need to configure a sharing policy.
Step 4: Configure an Autodiscover public DNS record
Note:
With federated sharing, users in your on-premises Exchange organization can share free/busy calendar information with recipients in other Exchange organizations that are also configured for federated sharing. Free/busy sharing can be enabled between two organizations running Exchange 2013 and also between organizations with a mixed Exchange deployment.
QUESTION 116
Drag and Drop Question
You have a server that has Exchange Server 2013 installed.
You plan to deploy Unified Messaging (UM) to all users.
You have two UM IP gateways named GW1 and GW2.
You create, and then associate a new UM dial plan for each IP gateway.
The IP gateways are configured as shown in the following table.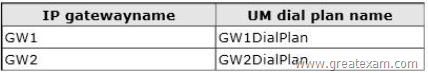
You need to recommend a solution that meets the following security requirements:
– All voice traffic received by GW1 must be encrypted.
– All voice traffic received by GW2 must be unencrypted.
– All signaling traffic to GW1 and GW2 must be encrypted.
Which security settings should you recommend configuring for each dial plan? To answer, drag the appropriate security setting to the correct UM dial plan in the answer area. Each security setting may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
Answer: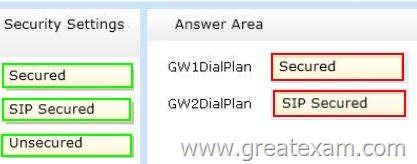
QUESTION 117
You have an Exchange Server 2013 organization that contains multiple Hub Transport servers.
You need to recommend a message hygiene solution to meet the following requirements:
– Block servers that are known to send spam
– Minimize administrative effort
What should you recommend?
A. an IP Block list
B. IP Block list providers
C. recipient filtering
D. sender filtering
Answer: B
QUESTION 118
You have an Exchange Server 2010 organization named adatum.com.
All public folders are stored on a server named EX5.
You deploy a new server named EX6. EX6 has Exchange Server 2013 installed.
You move all mailboxes to EX6.
You need to move the public folders to EX6.
The solution must ensure that users can access the public folders after EX5 is decommissioned.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. On EX6, create a public folder mailbox.
B. On EX6, run the New-PublicFolderMigrationRequest cmdlet.
C. On EX5, modify the replication partners for all of the public folders.
D. On EX6, run the New-SiteMailboxProvisioningPolicy cmdlet.
E. On EX5, assign the FolderOwner permission to the Public Folder Management management role group for all of the public folders.
F. On EX6, run the MoveAllReplicas.ps1 script.
Answer: AB
Explanation:
B: Use the New-PublicFolderMigrationRequest cmdlet to begin the process of migrating public folders from Microsoft Exchange Server 2007 or Exchange Server 2010 to Exchange Server 2013.
Note: See step 4 and 5 below.
Step 1: Download the migration scripts
Step 2: Prepare for the migration
Step 3: Generate the .csv files
Step 4: Create the public folder mailboxes on the Exchange 2013 server
Step 5: Start the migration request
Example:
New-PublicFolderMigrationRequest -SourceDatabase (Get-PublicFolderDatabase –Server
<Source server name>) -CSVData (Get-Content <Folder to mailbox map path> -Encoding
Byte) -BadItemLimit $BadItemLimitCount
Step 6: Lock down the public folders on the legacy Exchange server for final migration (downtime required)
Step 7: Finalize the public folder migration (downtime required)
Step 8: Test and unlock the public folder migration
QUESTION 119
Your company has a main office and a branch office.
An Active Directory site exits for each office.
The offices are connected by a WAN link.
You plan to deploy Exchange Server 2013 in each site.
You need to identify the number of Exchange servers required to meet the following requirements:
– Maintain user access to mailboxes if a single server fails
– Use the minimize account of Exchange servers in each site
How many servers should you deploy in each site?
A. 1
B. 2
C. 3
D. 4
Answer: B
QUESTION 120
You have an Exchange Server 2010 organization.
A user named User1 connects to his mailbox using Microsoft Office Outlook. User1 reports that he is unable to send encrypted email messages to an external recipient named User2.
You verify that User1 and User2 have email encryption certificates.
You need to ensure that User1 can send encrypted email messages to User2.
What should you do first?
A. Instruct User2 to add a delegate.
B. Instruct User2 to send a signed email message to User1.
C. Instruct User1 to send a signed email message to User2.
D. Instruct User1 to modify the sensitivity settings of the email message.
Answer: B
QUESTION 121
Your company has an Exchange Server 2010 organization.
The network contains an internal root certification authority (CA).
You plan to add a disclaimer to all email messages sent by users in the company.
You need to ensure that the disclaimer can be added to encrypted email messages.
What should you do?
A. Instruct users to encrypt email messages by using IRM only.
B. Instruct users to encrypt email messages by using S/MIME only.
C. Enable the Content Filter agent on all of the Hub Transport servers.
D. Modify the priority of the Transport Rule agent on all of the Hub Transport servers.
Answer: A
QUESTION 122
You have an Exchange Server 2010 organization.
You need to ensure that users in the organization are notified before they send email messages to external recipients.
Which cmdlet should you run?
A. Set-Mailbox.
B. Set-OrganizationConfig.
C. Set-TransportAgent.
D. Set-TransportConfig.
Answer: B
QUESTION 123
Your company acquires a new internet domain name.
You need to ensure that all users can receive email messages sent to the new domain name.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two).
A. Modify the email address policy.
B. Create an Authoritative accepted domain.
C. Create an External Relay accepted domain.
D. Modify the properties of the default Receive connector.
E. Generate a new Exchange certificate that contains the new domain name.
Answer: AB
QUESTION 124
Your company is investigating a user named User1.
You need to prevent User1 from permanently deleting items from his mailbox.
What should you run?
A. Set-Mailbox User1 LitigationHoldEnabled $true.
B. Set-Mailbox User1 ModerationEnabled $true.
C. Set-Mailbox User1 RetainDeletedItemsUntilBackup $true.
D. Set-Mailbox User1 RetentionHoldEnabled $true.
Answer: A
QUESTION 125
You are an Administrator for an International Finance Company.
You plan to deploy an Exchange Server 2013 Organization.
The company’s Compliance Policy requires that all users be prevented from sending email
messages that contain more than one Bank Account number to external recipients.
You need to meet the compliance policy requirement.
What should you create?
A. A Data Loss Prevention (DLP) Policy and a DLP Policy Rule.
B. A Retention Policy, a Retention Tag, and a Policy Tip.
C. A Throttling Policy and a Throttling Policy Association
D. A Transport Rule and a Moderated Mailbox
Answer: A
Explanation:
Sensitive Information Types in DLP Policies
When you create DLP policies, you can include rules that include checks for sensitive information. The conditions that you establish within a policy, such as how many times something has to be found before an action is taken or exactly what that action is can be customized within your new custom policies in order to meet your business requirements.
Sensitive information rules are integrated with the transport rules framework by introduction of a condition that you can customize:
If the message contains…Sensitive Information.
This condition can be configured with one or more sensitive information types that are contained within the messages.
GreatExam Microsoft 70-342 exam dumps are audited by our certified subject matter experts and published authors for development. GreatExam Microsoft 70-342 exam dumps are one of the highest quality Microsoft 70-342 Q&As in the world. It covers nearly 96% real questions and answers, including the entire testing scope. GreatExam guarantees you pass Microsoft 70-342 exam at first attempt.