The Microsoft 70-412 PDF, 70-412 practice test and 70-412 questions and answers at GreatExam are written and prepared by Microsoft affiliated trainers and lecturers with decades of experience in the IT field. This ensures that you are equipped with the latest and most current information to give you a better chance of passing the Microsoft 70-412 exam.
QUESTION 181
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 has the Active Directory Certificate Services server role installed and configured.
For all users, you are deploying smart cards for logon.
You are using an enrollment agent to enroll the smart card certificates for the users.
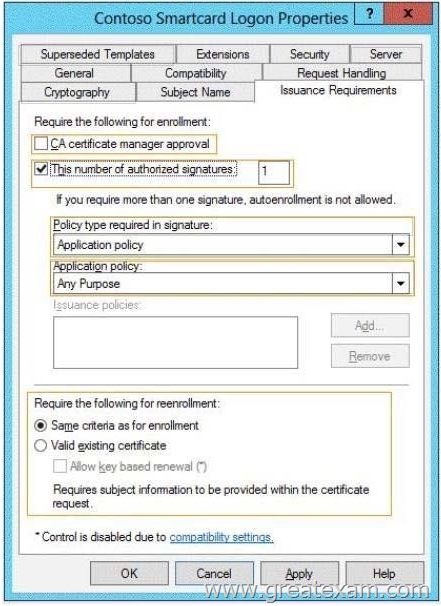
You need to configure the Contoso Smartcard Logon certificate template to support the use of the enrollment agent.
Which setting should you modify? To answer, select the appropriate setting in the answer area.
Answer: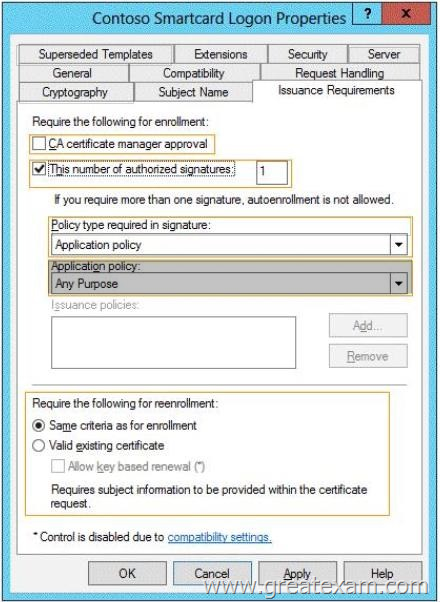
Explanation:
http://social.technet.microsoft.com/Forums/en-US/winserversecurity/thread/162e1108-bd46-4b2b-9ea0-4fff8949a810
http://technet.microsoft.com/en-us/library/cc725621(v=WS.10).aspx
QUESTION 182
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
The domain contains the two servers.The servers are configured as shown in the following table.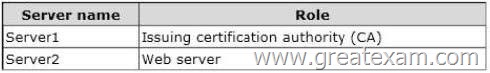
You investigate a report about the potential compromise of a private key for a certificate issued to Server2.
You need to revoke the certificate issued to Server2.
The solution must ensure that the revocation can be reverted.
Which reason code should you select? To answer, select the appropriate reason code in the answer area.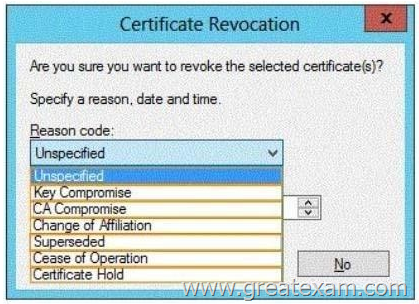
Answer: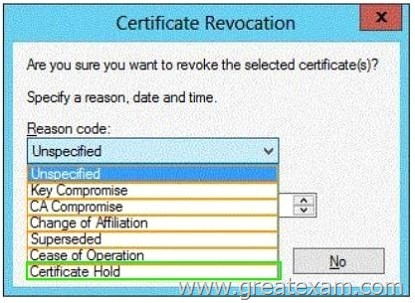
Explanation:
http://technet.microsoft.com/en-us/library/cc753724(v=WS.10).aspx
If you specify “Certificate Hold” as the reason for revoking the certificate, it typically means that you may want to unrevoke the certificate at a future time. Only certificates that have been revoked with the reason of “Certificate Hold” can be unrevoked.
QUESTION 183
Drag and Drop Question
Your network contains two Active Directory forests named contoso.com and adatum.com.
All domain controllers run Windows Server 2012 R2. A federated trust exists between adatum.com and contoso.com. The trust provides adatum.com users with access to contoso.com resources.
You need to configure Active Directory Federation Services (AD FS) claim rules for the federated trust. The solution must meet the following requirements:
– In contoso.com, replace an incoming claim type named Group with an outgoing claim type named Role.
– In adatum.com, allow users to receive their tokens for the relying party by using their Active Directory group membership as the claim type.
The AD FS claim rules must use predefined templates.
Which rule types should you configure on each side of the federated trust? To answer, drag the appropriate rule types to the correct location or locations. Each rule type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.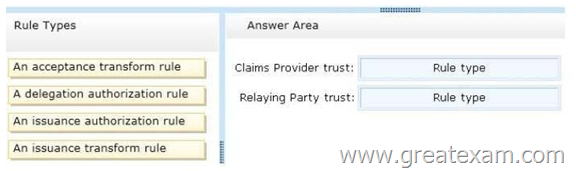
Answer: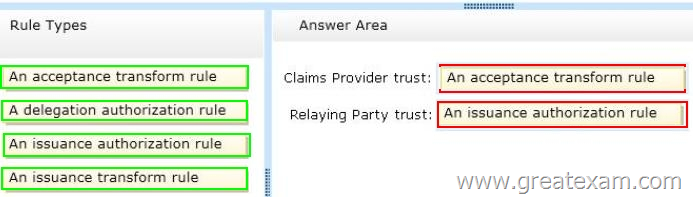
Explanation:
http://technet.microsoft.com/zh-cn/library/ee913586(v=WS.10).aspx
QUESTION 184
Drag and Drop Question
Your network contains four servers that run Windows Server 2012 R2.
Each server has the Failover Clustering feature installed.
Each server has three network adapters installed.
An iSCSI SAN is available on the network.
You create a failover cluster named Cluster1.
You add the servers to the cluster.
You plan to configure the network settings of each server node as shown in the following table.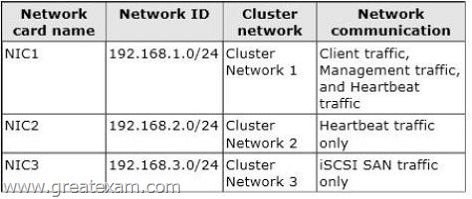
You need to configure the network settings for Cluster1.
What should you do? To answer, drag the appropriate network communication setting to the correct cluster network. Each network communication setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.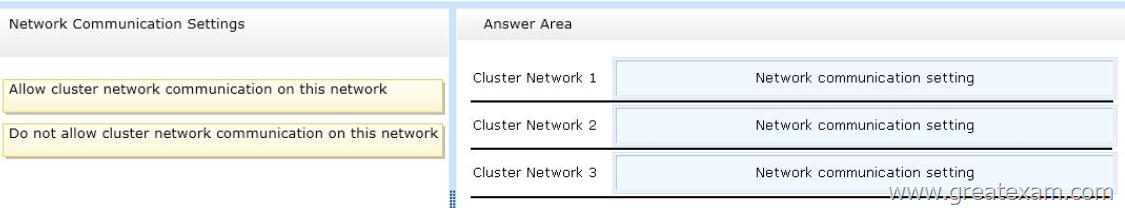
Answer:
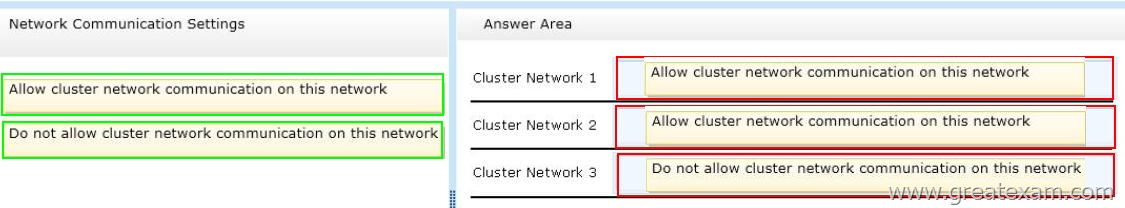
Explanation:
http://technet.microsoft.com/en-us/library/cc787135(v=WS.10).aspx
QUESTION 185
Hotspot Question
You have a server named Server1 that runs Windows Server 2012 R2.
The volumes on Server1 are configured as shown in the following table.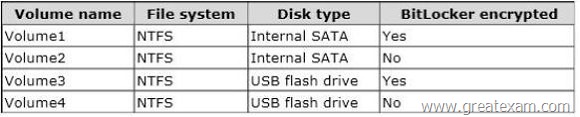
A new corporate policy states that backups must use Windows Azure Online Backup whenever possible.
You need to identify which backup methods you must use to back up Server1.
The solution must use Windows Azure Online Backup whenever possible.
Which backup type should you identify for each volume? To answer, select the appropriate backup type for each volume in the answer area.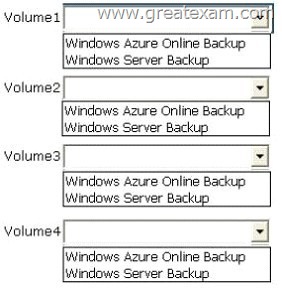
Answer: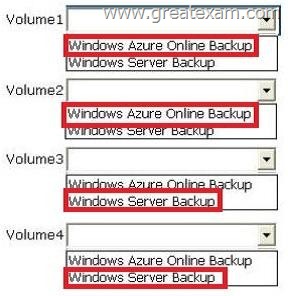
Explanation:
Why should Vol1 be Windows Server Backup?
http://msdn.microsoft.com/en-us/library/azure/jj573031.aspx
Drive description: Azure Backup supported:
BitLocker-protected volume Yes, but the volume must be unlocked before the backup can occur.
http://technet.microsoft.com/en-us/library/jj614621.aspx
http://technet.microsoft.com/zh-cn/library/hh831419.aspx
QUESTION 186
Drag and Drop Question
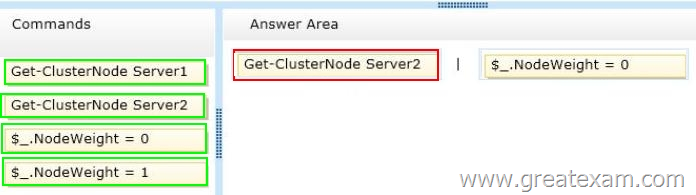
Your network contains an Active Directory domain named contoso.com. The domain contains four member servers named Server1, Server2, Servers, and Server4. All servers run Windows Server 2012 R2. Server1 and Server2 are located in a site named Site1. Server3 and Server4 are located in a site named Site2. The servers are configured as nodes in a failover cluster named Cluster1. Cluster1 is configured to use the Node Majority quorum configuration.
You need to ensure that Server1 is the only server in Site1 that can vote to maintain quorum.
What should you run from Windows PowerShell? To answer, drag the appropriate commands to the correct location. Each command may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.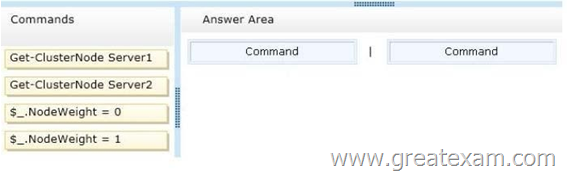
Answer:
QUESTION 187
Your network contains an Active Directory forest named contoso.com.
The forest contains a single domain. The domain contains three domain controllers.
The domain controllers are configured as shown in the following table.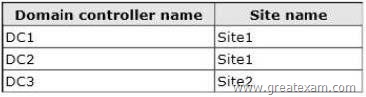
You plan to test an application on a server named Server1.
Server1 is currently located in Site1. After the test, Server1 will be moved to Site2.
You need to ensure that Server1 attempts to authenticate to DC3 first, while you test the application. What should you do?
A. Create a new site and associate the site to an existing site link object.
B. Modify the priority of site-specific service location (SRV) DNS records for Site2.
C. Create a new subnet object and associate the subnet object to an existing site.
D. Modify the weight of site-specific service location (SRV) DNS records Site1.
Answer: B
Explanation:
Service Location (SRV) Resource Record
Priority A number between 0 and 65535 that indicates the priority or level of preference given for this record to the host that is specified in Host offering this service.
Priority indicates this host’s priority with respect to the other hosts in this domain that offer the same service and are specified by different service location (SRV) resource records.
Incorrect:
Not D:
Weight: A number between 1 and 65535 to be used as a load-balancing mechanism. When you select among more than one target SRV host for the type of service (specified in Service) that use the same Priority number, you can use this field to weight preference toward specific hosts. Where several hosts share equal priority, SRV-specified hosts with higher weight values that are entered here should be returned first to resolver clients in SRV query results. Reference: Service Location (SRV) Resource Record Dialog Box
QUESTION 188
Your network contains an Active Directory domain named contoso.com.
The domain contains a file server named Server1.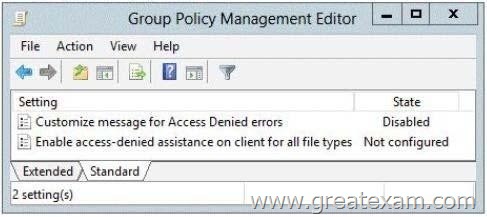
The File Server Resource Manager role service is installed on Server1. All servers run Windows Server 2012 R2. A Group Policy object (GPO) named GPO1 is linked to the organizational unit (OU) that contains Server1. The following graphic shows the configured settings in GPO1.
Server1 contains a folder named Folder1. Folder1 is shared as Share1.
You attempt to configure access-denied assistance on Server1, but the Enable access-denied assistance option cannot be selected from File Server Resource Manager.
You need to ensure that you can configure access-denied assistance on Server1 manually by using File Server Resource Manager.
Which two actions should you perform?
A. Set the Enable access-denied assistance on client for all file types policy setting to Disabled for GPO1.
B. Set the Customize message for Access Denied errors policy setting to Not Configured for GPO1.
C. Set the Enable access-denied assistance on client for all file types policy setting to Enabled for GPO1.
D. Set the Customize message for Access Denied errors policy setting to Enabled for GPO1.
Answer: BC
Explanation:
B: Having the ‘Customize messages for Access Denied errors’ set to Disabled as the exhibit shows is what is causing the option to be grayed out in FSRM. By setting this to Not Configured, you would then have the ability to MANUALLY ENABLE it in FSRM, like the question is stating you should do.
C: ‘Enable access-denied assistance…’ needs to be set to Enabled, as it is outlined in the technet article for configuring this feature. If you only do the first step and not this, access-denied assistance will still not work.
QUESTION 189
Your company has a main office and a remote office. The remote office is used for disaster recovery.
The network contains an Active Directory domain named contoso.com.
The domain contains member servers named Server1, Server2, Server3, and Server4.
All servers run Windows Server 2012 R2. Server1 and Server2 are located in the main office.
Server3 and Server4 are located in the remote office.
All servers have the Failover Clustering feature installed. The servers are configured as nodes in a failover cluster named Cluster1. Storage is replicated between the main office and the remote site. You need to ensure that Cluster1 is available if two nodes in the same office fail.
What are two possible quorum configurations that achieve the goal? (Each correct answer presents a complete solution. Choose two.)
A. Node Majority
B. No Majority: Disk Only
C. Node and File Share Majority
D. Node and Disk Majority
Answer: CD
Explanation:
To prevent a 2 site cluster from entering what is known as a split brain cluster when one site fails, ensure that you have File Share Majority or Disk Majority located in remote site.
QUESTION 190
Drag and Drop Question
Your network contains an Active Directory domain named adatum.com.
The domain contains three servers. The servers are configured as shown in the following table.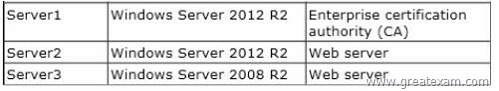
Server1 is configured as shown in the exhibit. (Click the Exhibit button.)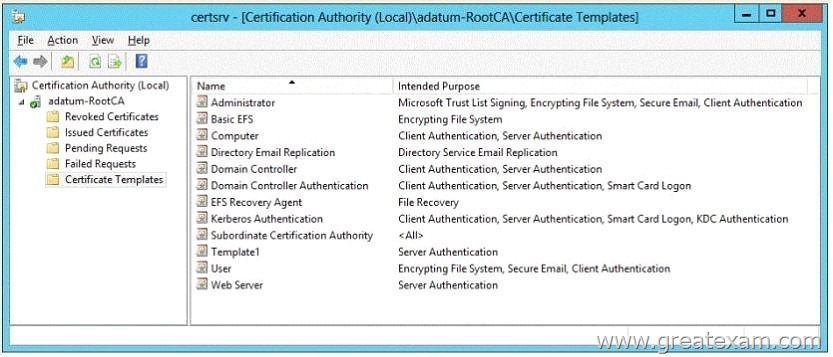
Template1 contains custom cryptography settings that are required by the corporate security team.
On Server2, an administrator successfully installs a certificate based on Template1.
The administrator reports that Template1 is not listed in the Certificate Enrollment wizard on Server3, even after selecting the Show all templates check box.
You need to ensure that you can install a server authentication certificate on Server3.
The certificate must comply with the cryptography requirements.
Which three actions should you perform in sequence? To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.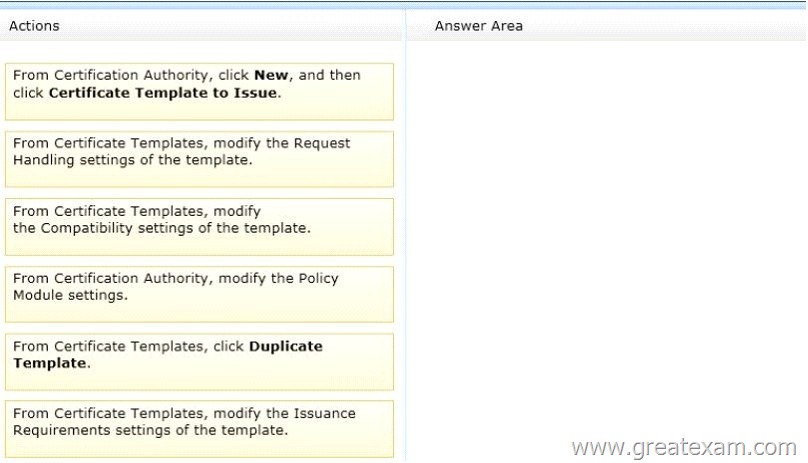
Answer: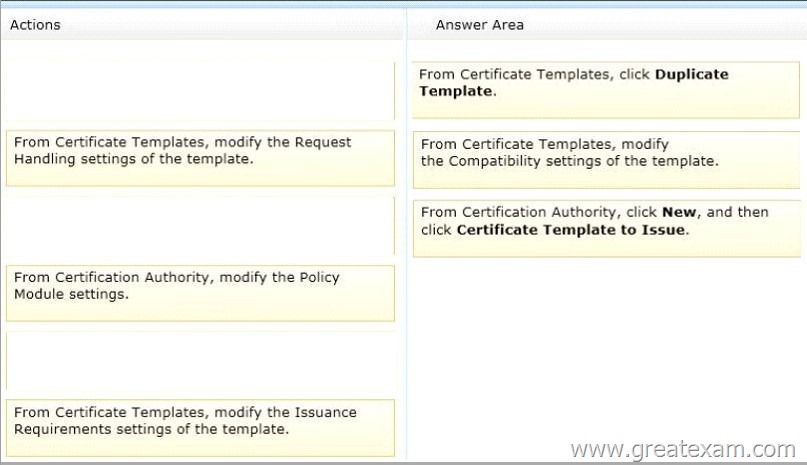
Explanation:
http://social.technet.microsoft.com/wiki/contents/articles/15897.certificate-templates-not-available-for-windows-7-and-windows-server-2008-r2-certificate-recipients-using-certificate-enrollment-web-services.aspx
.
QUESTION 191
Your company has two offices. The offices are located in Seattle and Montreal.
The network contains an Active Directory domain named contoso.com. The domain contains two DHCP servers named Server1 and Server2. Server1 is located in the Seattle office.
Server2 is located in the Montreal office. All servers run Windows Server 2012 R2.
You need to create a DHCP scope for video conferencing in the Montreal office.
The scope must be configured as shown in the following table.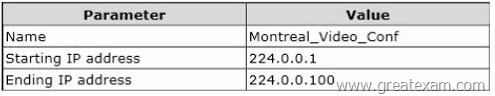
Which Windows PowerShell cmdlet should you run?
A. Add-DchpServerv4SuperScope
B. Add-DchpServerv4MulticastScope
C. Add-DHCPServerv4Policy
D. Add-DchpServerv4Scope
Answer: B
Explanation:
Add-DhcpServerv4MulticastScope: Adds a multicast scope on the DHCP server.
QUESTION 192
You have a server named Server1 that runs Windows Server 2012 R2.
The storage on Server1 is configured as shown in the following table.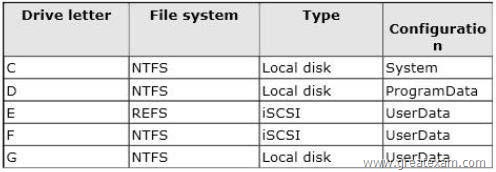
You plan to implement Data Deduplication on Server1.
You need to identify on which drives you can enable Data Deduplication.
Which three drives should you identify? (Each correct answer presents part of the solution. Choose three.)
A. C
B. D
C. E
D. F
E. G
Answer: BDE
Explanation:
Volumes that are candidates for deduplication must conform to the following requirements:
* (not A) Must not be a system or boot volume. Deduplication is not supported on operating system volumes.
* Can be partitioned as a master boot record (MBR) or a GUID Partition Table (GPT), and must be formatted using the NTFS file system.
* Can reside on shared storage, such as storage that uses a Fibre Channel or an SAS array, or when an iSCSI SAN and Windows Failover Clustering is fully supported.
* Do not rely on Cluster Shared Volumes (CSVs).
You can access data if a deduplicationenabled volume is converted to a CSV, but you cannot continue to process files for deduplication.
* (not C) Do not rely on the Microsoft Resilient File System (ReFS).
* Must be exposed to the operating system as non-removable drives.
Remotely-mapped drives are not supported.
http://technet.microsoft.com/en-us/library/hh831700.aspx
QUESTION 193
You have 20 servers that run Windows Server 2012 R2.
You need to create a Windows PowerShell script that registers each server in Windows Azure Online Backup and sets an encryption passphrase.
Which two PowerShell cmdlets should you run in the script? (Each correct answer presents part of the solution. Choose two.)
A. New-OBPolicy
B. New-OBRetentionPolicy
C. Add-OBFileSpec
D. Start-OBRegistration
E. Set OBMachineSetting
Answer: DE
Explanation:
D: Start-OBRegistration
Registers the current computer with Windows Azure Online Backup using the credentials
(username and password) created during enrollment.
E: The Set-OBMachineSetting cmdlet sets a OBMachineSetting object for the server that includes proxy server settings for accessing the internet, network bandwidth throttling settings, and the encryption passphrase that is required to decrypt the files during recovery to another server.
Incorrect:
Not C: The Add-OBFileSpec cmdlet adds the OBFileSpec object, which specifies the items to include or exclude from a backup, to the backup policy (OBPolicy object).
The OBFileSpec object can include or exclude multiple files, folders, or volumes.
http://technet.microsoft.com/en-us/library/hh770416(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/hh770425(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/hh770424.aspx
http://technet.microsoft.com/en-us/library/hh770398.aspx
http://technet.microsoft.com/en-us/library/hh770409.aspx
QUESTION 194
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
You need to ensure that a WIM file that is located on a network share is used as the installation source when installing server roles and features on Server1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Run the dism.exe command and specify the /remove-package parameter.
B. Run the Remove-WindowsFeature cmdlet.
C. Enable and configure the Specify settings for optional component installation and component repair
policy setting by using a Group Policy object (GPO).
D. Enable the Enforce upgrade component rules policy setting by using a Group Policy object (GPO).
E. Run the Remove-WindowsPackage cmdlet.
Answer: CD
QUESTION 195
Your network contains an Active Directory forest. The forest contains two domains named contoso.com and fabrikam.com. The functional level of the forest is Windows Server 2003.
You have a domain outside the forest named litwareinc.com.
You need to configure an access solution to meet the following requirements:
– Users in litwareinc.com must be able to access resources on a server named Server1 in contoso.com.
– Users in the contoso.com forest must be prevented from accessing any resources in litwareinc.com.
– Users in litwareinc.com must be prevented from accessing any other resources in the contoso.com forest.
Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. Configure SID filtering on the trust.
B. Configure forest-wide authentication on the trust.
C. Create a one-way forest trust.
D. Create a one-way external trust
E. Modify the permission on the Server1 object.
F. Configure selective authentication on the trust.
Answer: DEF
Explanation:
D (not C): litwareinc.com is outside the forest so we need an external trust (not a forest trust).
E: Must grant the required permissions on Server1.
F(not B): For external trust we must either select Domain-Wide or Selective Authentication (forst- wide authentication is not an option)
Note:
* You can create an external trust to form a one-way or two-way, nontransitive trust with domains that are outside your forest. External trusts are sometimes necessary when users need access to resources in a Windows NT 4.0 domain or in a domain that is located in a separate forest that is not joined by a forest trust.
/ To select the scope of authentication for users that are authenticating through a forest trust, click the forest trust that you want to administer, and then click Properties .
On the Authentication tab, click either Forest-wide authentication or Selective authentication .
/ To select the scope of authentication for users that are authenticating through an external trust, click the external trust that you want to administer, and then click Properties .
On the Authentication tab, click either Domain-wide authentication or Selective authentication .
* The forest-wide authentication setting permits unrestricted access by any users in the trusted forest to all available shared resources in any of the domains in the trusting forest.
* Forest-wide authentication is generally recommended for users within the same organization.
http://technet.microsoft.com/en-us/library/cc776245(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc755844(v=ws.10).aspx
QUESTION 196
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1 that runs Windows Server 2012 R2. All client computers run Windows 8. You need to configure a custom Access Denied message that will be displayed to users when they are denied access to folders or files on Server1.
What should you configure?
A. A classification property
B. The File Server Resource Manager Options
C. A file management task
D. A file screen template
Answer: B
Explanation:
File Server Resource Manager is a suite of tools that allows administrators to understand, control, and manage the quantity and type of data stored on their servers. By using File Server Resource Manager, administrators can place quotas on folders and volumes, actively screen files, and generate comprehensive storage reports.
This set of advanced instruments not only helps the administrator to efficiently monitor existing storage resources but it also aids in the planning and implementation of future policy changes.
http://technet.microsoft.com/en-us/library/cc755603%28v=ws.10%29.aspx
QUESTION 197
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. The forest contains three Active Directory sites named SiteA, SiteB, and SiteC.
The sites contain four domain controllers.
The domain controllers are configured as shown in the following table.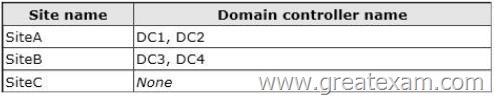
You discover that the users in SiteC are authenticated by the domain controllers in SiteA and SiteB. You need to ensure that the SiteC users are authenticated by the domain controllers in SiteB, unless all of the domain controllers in SiteB are unavailable.
What should you do?
A. Create additional connection objects for DC3 and DC4.
B. Decrease the cost of the site link between SiteB and SiteC.
C. Create a site link bridge.
D. Disable site link bridging.
Answer: B
Explanation:
By decreasing the cost between SiteB and SiteC, the SiteC users will be authenticated by SiteB domain controllers.
Note:
* A site link bridge connects two or more site links and enables transitivity between site links. Each site link in a bridge must have a site in common with another site link in the bridge.
* By default, all site links are transitive.
QUESTION 198
Your network contains an Active Directory domain named contoso.com.
The domain contains a. DC2 has the DHCP Server server role installed.
DHCP is configured as shown in the exhibit. (Click the Exhibit button.)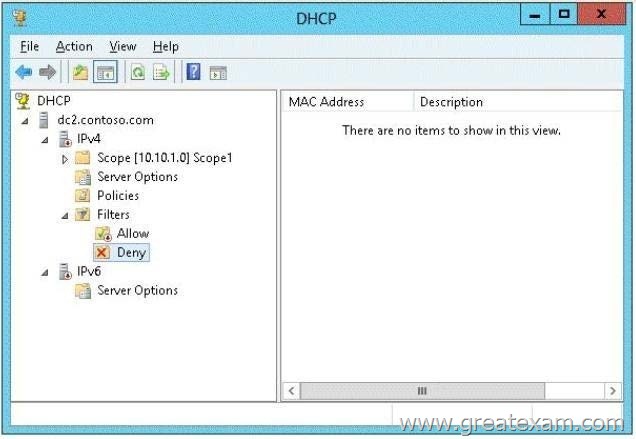
You discover that client computers cannot obtain IPv4 addresses from DC2.
You need to ensure that the client computers can obtain IPv4 addresses from DC2.
What should you do?
A. Disable the Deny filters.
B. Enable the Allow filters.
C. Authorize DC2.
D. Restart the DHCP Server service
Answer: C
Explanation:
From the exhibit we see a red marker on the IPv4 server icon. The DHCP server is not authorized.
Authorize DHCP Server
The final step is to authorize the server.
Right-click your FQDN and select Authorize.
Refresh the view by right-clicking your FQDN and selecting Refresh.
You should now see green check mark next to IPv4.
QUESTION 199
Your network contains an Active Directory forest named adatum.com.
All servers run Windows Server 2012 R2. The domain contains four servers.
The servers are configured as shown in the following table.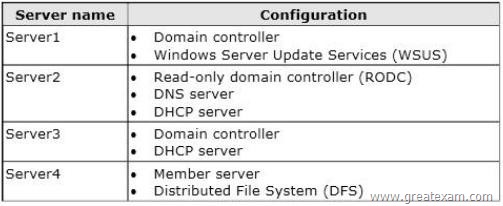
You need to deploy IP Address Management (IPAM) to manage DNS and DHCP.
On which server should you install IPAM?
A. Server1
B. Server2
C. Server3
D. Server4
Answer: D
Explanation:
D. IPAM cannot be installed on Domain Controllers. All other servers have the DC role
http://technet.microsoft.com/en-us/library/hh831353.aspx
QUESTION 200
Hotspot Question
Your network contains one Active Directory forest named contoso.com and one Active Directory forest named adatum.com. Each forest contains a single domain.
You have the domain controllers configured as shown in the following table.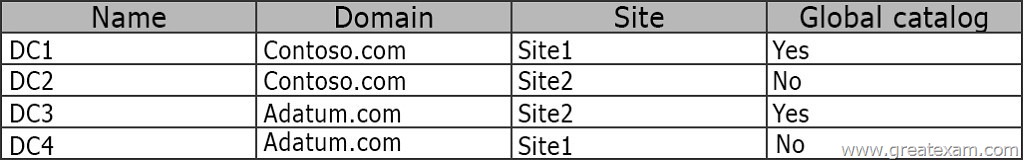
You perform the following three actions:
– Create a user named User1 on DC3.
– Create a file named File1.txt in the SYSVOL folder on DC1.
– Create a Group Policy object (GPO) named GPO1 on DC1 and link GPO1 to Site2.
You need to identify on which domain controller or controllers each object is stored.
What should you identify? To answer, select the appropriate options in the answer area.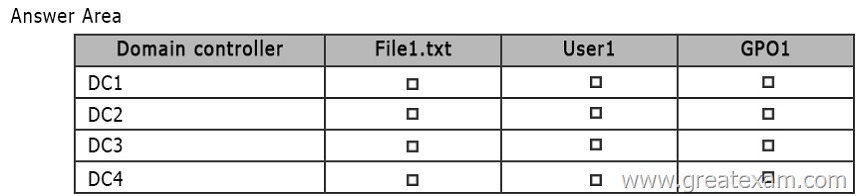
Answer: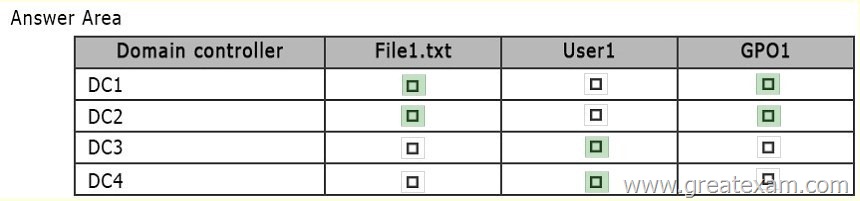
Explanation:
Sysvol replicates to all DCs in contoso, so this includes the file created in sysvol, and the GPO1 template stored in sysvol.
User account replicates to all DCs in Adatum, a seperate forest to Contoso, so therefore will not replicate to any DCs in contoso.
GreatExam guarantees your 70-412 exam success with our exam resources. Our 70-412 braindumps are the latest and developed by experienced IT certification professionals working in today’s prospering companies and data centers. All our 70-412 braindumps include 70-412 real exam questions which guarantee your 100% success of 70-412 exam in your first try.