Are you worring about the 70-412 exam? GreatExam provides the latest 70-412 braindumps and guarantees you passing 70-412 exam beyond any doubt.
QUESTION 241
Your network contains an Active Directory forest named contoso.com.
The forest contains two domains named contoso.com and childl.contoso.com.
The domains contain three domain controllers.
The domain controllers are configured as shown in the following table.
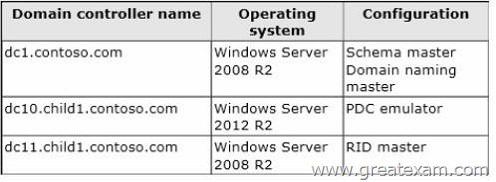
You need to ensure that the KDC support for claims, compound authentication, and kerberos armoring setting is enforced in both domains.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. Raise the domain functional level of contoso.com.
B. Raise the domain functional level of child1.contoso.com.
C. Raise the forest functional level of contoso.com.
D. Upgrade DC11 to Windows Server 2012 R2.
E. Upgrade DC1 to Windows Server 2012 R2.
Answer: AE
Explanation:
To use claims-based authorization, you need the following:
• Windows Server 2012 must be installed on the file server that hosts the resources that DAC protects.
• At least one Windows Server 2012 domain controller must be accessible by the requesting client.
• If you use claims across a forest, you must have a Windows Server 2012 domain controller in each domain.
• If you use device claims, clients must run Windows 8.
A question in the same book indicates:
Identify the minimum domain function level (2003, 2008, 2008 R2, or 2012) for the specified feature…
KDC support for claims – 2012
So the answer is A and E.
E because you must upgrade the domain controller to 2012 R2 to raise the functional level of the domain to the necessary level, and A because 2012 domain functional level is required for KDC support for claims.
Upgrading dc11.child1.contoso.com is not necessary because there is already a Server 2012 R2 server in the child domain (dc10).
QUESTION 242
Your network contains two servers named HV1 and HV2. Both servers run Windows Server 2012 R2 and have the Hyper-V server role installed. HV1 hosts 25 virtual machines.
The virtual machine configuration files and the virtual hard disks are stored in D:\VM.
You shut down all of the virtual machines on HV1.
You copy D:\VM to D:\VM on HV2.
You need to start all of the virtual machines on HV2.
You want to achieve this goal by using the minimum amount of administrative effort.
What should you do?
A. Run the Import-VMInitialReplication cmdlet.
B. From HV1, export all virtual machines to D:\VM.
Copy D:\VM to D:\VM on HV2 and overwrite the existing files.
On HV2, run the Import Virtual Machine wizard.
C. From HV1, export all virtual machines to D:\VM.
Copy D:\VM to D:\VM on HV2 and overwrite the existing files.
On HV2, run the New Virtual Machine wizard.
D. Run the Import-VM cmdlet.
Answer: D
QUESTION 243
Your company recently deployed a new Active Directory forest named contoso.com.
The first domain controller in the forest runs Windows Server 2012 R2.
You need to identify the t that lists any configuration issues on Host2 thN and SYSVOL shared folders.
Which tool should you use?
A. Ultrasound
B. Replmon
C. Dfsdiag
D. Frsutil
Answer: C
Explanation:
http://blogs.technet.com/b/josebda/archive/2009/07/15/five-ways-to-check-your-dfs-namespaces-dfs-n-configuration-with-the-dfsdiag-exe-tool.aspx
QUESTION 244
Your network contains three servers named Server1, Server2, and Server3.
All servers run Windows Server 2012 R2.
You need to ensure that Server1 can provide iSCSI storage for Server2 and Server3.
What should you do on Server1?
A. Start the Microsoft iSCSI Initiator Service and configure the iSCSI Initiator Properties.
B. Install the iSNS Server service feature and create a Discovery Domain.
C. Install the Multipath I/O (MPIO) feature and configure the MPIO Properties.
D. Install the iSCSI Target Server role service and configure iSCSI targets.
Answer: D
Explanation:
iSCSI: it is an industry standard protocol allow sharing block storage over the Ethernet. The server shares the storage is called iSCSI Target. The server (machine) consumes the storage is called iSCSI initiator. Typically, the iSCSI initiator is an application server.
For example, iSCSI Target provides storage to a SQL server, the SQL server will be the iSCSI initiator in this deployment.
Target: It is an object which allows the iSCSI initiator to make a connection.
The Target keeps track of the initiators which are allowed to be connected to it.
The Target also keeps track of the iSCSI virtual disks which are associated with it.
Once the initiator establishes the connection to the Target, all the iSCSI virtual disks associated with the Target will be accessible by the initiator.
iSCSI Target Server:
The server runs the iSCSI Target. It is also the iSCSI Target role name in Windows Server 2012.
http://blogs.technet.com/b/filecab/archive/2012/05/21/introduction-of-iscsi-target-in-windows-server-2012.aspx
QUESTION 245
Your network contains two servers that run Windows Server 2012 R2 named Server1 and Server2. Both servers have the File Server role service installed. On Server2, you create a share named Backups. From Windows Server Backup on Server1, you schedule a full backup to run every night. You set the backup destination to \\Server2 \Backups.
After several weeks, you discover that \\Server2\Backups only contains the last backup that completed on Server1.
You need to ensure that multiple backups of Server1 are maintained.
What should you do?
A. Modify the Volume Shadow Copy Service (VSS) settings.
B. Modify the properties of the Windows Store Service (WSService) service.
C. Change the backup destination.
D. Configure the permission of the Backups share.
Answer: C
QUESTION 246
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 has an enterprise root certification authority (CA) for contoso.com.
You deploy another member server named Server2 that runs Windows Server 2012 R2 and has the Web Server (IIS) server role installed.
You need to designate a website on Server1 as the certificate revocation list (CRL) distribution point for the CA. The solution must ensure that CRLs are published automatically to Server2.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Create an http:// CRL distribution point (CDP) entry.
B. Configure a CA exit module.
C. Create a file:// CRL distribution point (CDP) entry
D. Configure an enrollment agent.
E. Configure a CA policy module.
Answer: AE
Explanation:
A: To specify CRL distribution points in issued certificates Open the Certification Authority snap-in.
In the console tree, click the name of the CA.
On the Action menu, click Properties , and then click the Extensions tab. Confirm that Select extension is set to CRL Distribution Point (CDP) .
Do one or more of the following. (The list of CRL distribution points is in the Specify locations from which users can obtain a certificate revocation list (CRL) box.) / To indicate that you want to use a URL as a CRL distribution point Click the CRL distribution point, select the Include in the CDP extension of issued certificates check box, and then click OK .
Click Yes to stop and restart Active Directory Certificate Services (AD CS).
E: You can specify CRL Distribution Points (CDPs) in CAPolicy.inf. Note that any CDP in CAPolicy.inf will take precedence for certificate verifiers over the CDP’s specified in the CA policy module.
Note:
CRLDistributionPoint
You can specify CRL Distribution Points (CDPs) for a root CA certificate in the CAPolicy.inf. This section does not configure the CDP for the CA itself. After the CA has been installed you can configure the CDP URLs that the CA will include in each certificate that it issues. The URLs specified in this section of the CAPolicy.inf file are included in the root CA certificate itself.
Example:
[CRLDistributionPoint]
URL=http://pki.wingtiptoys.com/cdp/WingtipToysRootCA.crl
QUESTION 247
Your network contains an Active Directory domain named adatum.com.
You create a new Group Policy object (GPO) named GPO1.
You need to verify that GPO1 was replicated to all of the domain controllers.
Which tool should you use?
A. Gpupdate
B. Gpresult
C. Group Policy Management
D. Active Directory Sites and Services
Answer: C
Explanation:
In Windows Server 2012, the Group Policy Management Console (GPMC) was enhanced to provide a report for the overall health state of the Group Policy infrastructure for a domain, or to scope the health view to a single GPO.
http://technet.microsoft.com/en-us/library/jj134176.aspx
QUESTION 248
Your network contains an Active Directory domain named contoso.com.
The domain contains two domain controllers named DC1 and DC2.
You install Windows Server 2012 R2 on a new computer named DC3.
You need to manually configure DC3 as a domain controller.
Which tool should you use?
A. winrm.exe
B. Server Manager
C. dcpromo.exe
D. Active Directory Domains and Trusts
Answer: B
Explanation:
When you try to DCpromo a Server 2012, you get this message:
QUESTION 249
Your network contain an active directory domain named Contoso.com.
The domain contains two servers named server1 and server2 that run Windows Server 2012 R2.
You create a security template named template1 by using the security template snap-in.
You need to apply template1 to server2.
Which tool should you use?
A. Security Configuration and Analysis
B. Server Manager
C. Security Template
D. Computer management
Answer: A
QUESTION 250
Your network contains an Active Directory forest named contoso.com.
All servers run Windows Server 2012 R2.
You need to create a custom Active Directory Application partition.
Which tool should you use?
A. Netdom
B. Ntdsutil
C. Dsmod
D. Dsamain
Answer: B
Explanation:
* To create or delete an application directory partition Open Command Prompt.
Type:ntdsutil
At the ntdsutil command prompt, type:domain management
At the domain management command prompt, type:connection
At the server connections command prompt, type:connect to server ServerName
At the server connections command prompt, type:quit
At the domain management command prompt, do one of the following:
* partition management
Manages directory partitions for Active Directory Domain Services (AD DS) or Active Directory Lightweight Directory Services (AD LDS).
This is a subcommand of Ntdsutil and Dsmgmt. Ntdsutil and Dsmgmt are command-line tools that are built into Windows Server 2008 and Windows Server 2008 R2.
/ partition management create nc %s1 %s2
Creates the application directory partition with distinguished name %s1, on the Active Directory domain controller or AD LDS instance with full DNS name %s2. If you specify “NULL” for %s2, this command uses the currently connected Active Directory domain controller. Use this command only with AD DS. For AD LDS, use create nc %s1 %s2 %s3.
Note:
* An application directory partition is a directory partition that is replicated only to specific domain controllers.
A domain controller that participates in the replication of a particular application directory partition hosts a replica of that partition.
QUESTION 251
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named DC1 that runs Windows Server 2012 R2.
You create an Active Directory snapshot of DC1 each day.
You need to view the contents of an Active Directory snapshot from two days ago.
What should you do first?
A. Stop the Active Directory Domain Services (AD DS) service.
B. Run the ntdsutil.exe command.
C. Run the dsamain.exe command.
D. Start the Volume Shadow Copy Service (VSS).
Answer: B
QUESTION 252
You have a server named Server1 that runs Windows Server 2012 R2.
You need to configure Server1 to create an entry in an event log when the processor usage exceeds 60 percent.
Which type of data collector should you create?
A. an event trace data collector
B. a performance counter data collector
C. a performance counter alert
D. a configuration data collector
Answer: C
QUESTION 253
Your network contains two servers named Server1 and Server2.
Both servers run Windows Server 2012 R2, On Server1, you create a Data Collector Set (DCS) named Data1.
You need to export Data1 to Server2.
What should you do first?
A. Right-click Data1 and click Data Manager…
B. Right-click Data1 and click Save template…
C. Right-click Data1 and click Properties.
D. Right-click Data1 and click Export list…
Answer: B
Explanation:
http://technet.microsoft.com/en-us/library/cc766318.aspx
QUESTION 254
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. An organizational unit (OU) named OU1 contains 200 client computers that run Windows 8 Enterprise. A Group Policy object (GPO) named GPO1 is linked to OU1.
You make a change to GPO1.
You need to force all of the computers in OU1 to refresh their Group Policy settings immediately. The solution must minimize administrative effort.
Which tool should you use?
A. The Set-AdComputercmdlet
B. Group Policy Object Editor
C. Active Directory Users and Computers
D. Group Policy Management Console (GPMC)
Answer: D
Explanation:
In the previous versions of Windows, this was accomplished by having the user run GPUpdate.exe on their computer. Starting with Windows Server?2012 and Windows?8, you can now remotely refresh Group Policy settings for all computers in an OU from one central location through the Group Policy Management Console (GPMC). Or you can use the Invoke-GPUpdate cmdlet to refresh Group Policy for a set of computers, not limited to the OU structure, for example, if the computers are located in the default computers container.
Note: Group Policy Management Console (GPMC) is a scriptable Microsoft Management Console (MMC) snap-in, providing a single administrative tool for managing Group Policy across the enterprise. GPMC is the standard tool for managing Group Policy.
Incorrect:
Not B: Secedit configures and analyzes system security by comparing your current configuration to at least one template.
QUESTION 255
Your network contains an Active Directory domain named contoso.com. Network Access Protection (NAP) is deployed to the domain.
You need to create NAP event trace log files on a client computer.
What should you run?
A. Logman
B. Tracert
C. Register-EngineEvent
D. Register-ObjectEvent
Answer: A
QUESTION 256
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1. Server1 runs Windows Server 2012 R2.
You create a group Managed Service Account named gService1.
You need to configure a service named Service1 to run as the gService1 account.
How should you configure Service1?
A. From a command prompt, run sc.exe and specify the theconfig parameter.
B. From the Services console, configure the General settings.
C. From Windows PowerShell, run Set-Service and specify the -StartupType parameter.
D. From the Services console, configure the Log On settings.
Answer: D
Explanation:
Executing the sc.exe command with the config parameter will modify service configuration.
QUESTION 257
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has 2 dual-core processors and 16 GB of RAM.
You install the Hyper-V server role in Server1.
You plan to create two virtual machines on Server1.
You need to ensure that both virtual machines can use up to 8 GB of memory.
The solution must ensure that both virtual machines can be started simultaneously.
What should you configure on each virtual machine?
A. Dynamic Memory
B. NUMA topology
C. Memory weight
D. Ressource Control
Answer: A
QUESTION 258
You perform a Server Core Installation of Windows Server 2012 R2 on a server named Server1. You need to add a graphical user interface (GUI) to Server1.
Which tool should you use?
A. the dism.exe command
B. the ocsetup.exe command
C. the setup.exe command
D. the Install-Module cmdlet
Answer: A
Explanation:
The DISM command is called by the Add-WindowsFeature command. Here is the systax for DISM:
Dism /online /enable-feature /featurename:ServerCore-FullServer /featurename:ServerGui-Shell /featurename:Server-Gui-Mgmt
QUESTION 259
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. The domain contains two organizational units (OUs) named OU1 and OU2 in the root of the domain. Two Group Policy objects (GPOs) named GPO1 and GPO2 are created. GPO1 is linked to OU1. GPO2 is linked to OU2.
OU1 contains a client computer named Computer1. OU2 contains a user named User1.
You need to ensure that the GPOs Applied to Computer1 are Applied to User1 when User1 logs on.
What should you configure?
A. Item-level targeting
B. Block Inheritance
C. GPO links
D. The Enforced setting
Answer: A
Explanation:
https://msdn.microsoft.com/en-us/library/cc733022.aspx
GPO links is already happened, with item-level check Types of targeting items.
If this will allow for specifically targeting User1 and not apply to the entire OU2 and its objects.
QUESTION 260
Your network contains an Active Directory domain named contoso.com.
The domain contains client computers that run either Windows XP, Windows 7, or Windows 8.
Network Policy Server (NPS) is deployed to the domain.
You plan to create a system health validator (SHV).
You need to identify which policy settings can be Applied to all of the computers.
Which three policy settings should you identify? (Each correct answer presents part of the solution. Choose three.)
A. A firewall is enabled for all network connections.
B. An antispyware application is on.
C. Automatic updating is enabled.
D. Antivirus is up to date.
E. Antispyware is up to date.
Answer: ACD
Explanation:
* System health agent (SHA) is a NAP component.
* System health agent (SHA)
A component that checks the state of the client computer to determine whether the settings monitored by the SHA are up-to-date and configured correctly.
For example, the Windows Security Health Agent (WSHA) can monitor Windows Firewall, whether antivirus software is installed, enabled, and updated, whether antispyware software is installed, enabled, and updated, and whether Microsoft Update Services is enabled and the computer has the most recent security updates from Microsoft Update Services.
There might also be SHAs (and corresponding system health validators) available from other companies that provide different functionality.
GreatExam offers the latest 70-412 PDF and VCE dumps with new version VCE player for free download, and the new 70-412 practice test ensures your exam 100% pass.