Our PDF dumps of 70-417 exam is designed to ensure everything which you need to pass your exam successfully. At GreatExam, we have a completely customer oriented policy. We invite the professionals who have rich experience and expert knowledge of the IT certification industry to guarantee the PDF details precisely and logically. Our customers’ time is a precious concern for us. This requires us to provide you the products that can be utilized most efficiently.
QUESTION 121
You have 30 servers that run Windows Server 2012 R2.
All of the servers are backed up daily by using Windows Azure Online Backup.
You need to perform an immediate backup of all the servers to Windows Azure Online Backup. Which Windows PowerShell cmdlets should you run on each server?
A. Start-OBRegistration | Start-OBBackup
B. Get-OBPolicy | Start-OBBackup
C. Get-WBBackupTarget | Start-WBBackup
D. Get-WBPolicy | Start-WBBackup
Answer: B
Explanation:
A. starts a backup job using a policy
B. Registers the current computer to Windows Azure Backup.
C. Not using Azure
D. Not using Azure
http://technet.microsoft.com/en-us/library/hh770406(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/hh770426.aspx
http://technet.microsoft.com/en-us/library/hh770398.aspx
QUESTION 122
You have 20 servers that run Windows Server 2012 R2.
You need to create a Windows PowerShell script that registers each server in Windows Azure Online Backup and sets an encryption passphrase.
Which two PowerShell cmdlets should you run in the script? (Each correct answer presents part of the solution. Choose two.)
A. New-OBPolicy
B. New-OBRetentionPolicy
C. Add-OBFileSpec
D. Start-OBRegistration
E. Set-OBMachineSetting
Answer: DE
Explanation:
D: Start-OBRegistration
Registers the current computer with Windows Azure Online Backup using the credentials (username and password) created during enrollment.
E: The Set-OBMachineSettingcmdlet sets aOBMachineSetting object for the server that includes proxy server settings for accessing the internet, network bandwidth throttling settings, and the encryption passphrase that is required to decrypt the files during recovery to another server. Incorrect:
Not C: TheAdd-OBFileSpeccmdlet adds theOBFileSpecobject, which specifies the items to include or exclude from a backup, to the backup policy (OBPolicyobject).
TheOBFileSpecobject can include or exclude multiple files, folders, or volumes. T
http://technet.microsoft.com/en-us/library/hh770416(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/hh770425(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/hh770424.aspx
http://technet.microsoft.com/en-us/library/hh770398.aspx
http://technet.microsoft.com/en-us/library/hh770409.aspx
QUESTION 123
Your network contains an Active Directory domain named adatum.com. All domain controllers run Windows Server 2008 R2. The domain contains a file server named Server6 that runs Windows Server 2012 R2. Server6 contains a folder named Folder1. Folder1 is shared as Share1. The NTFS permissions on Folder1 are shown in the exhibit. (Click the Exhibit button.)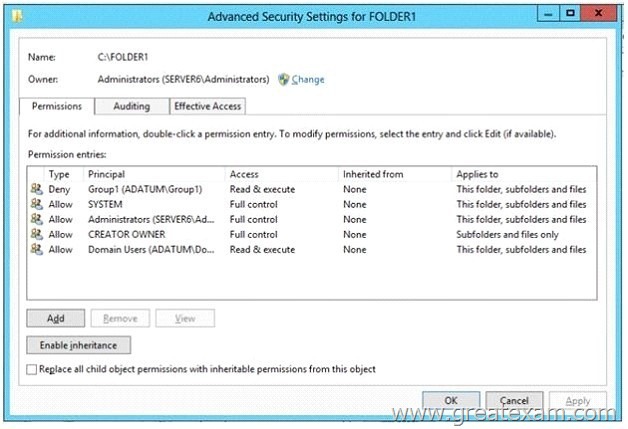
The domain contains two global groups named Group1 and Group2.
You need to ensure that only users who are members of both Group1 and Group2 are denied access to Folder1.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Remove the Deny permission for Group1 from Folder1.
B. Deny Group2 permission to Folder1.
C. Install a domain controller that runs Windows Server 2012 R2.
D. Create a conditional expression.
E. Deny Group2 permission to Share1.
F. Deny Group1 permission to Share1.
Answer: AD
Explanation:
* Conditional Expressions for Permission Entries Windows Server 2008 R2 and Windows 7 enhanced Windows security descriptors by introducing a conditional access permission entry. Windows Server 2012 R2 takes advantage of conditional access permission entries by inserting user claims, device claims, and resource properties, into conditional expressions. Windows Server 2012 R2 security evaluates these expressions and allows or denies access based on results of the evaluation. Securing access to resources through claims is known as claims-based access control. Claims-based access control works with traditional access control to provide an additional layer of authorization that is flexible to the varying needs of the enterprise environment.
http://social.technet.microsoft.com/wiki/contents/articles/14269.introducing-dynamicaccess-control-en-us.aspx
QUESTION 124
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1. The File Server Resource Manager role service is installed on Server1. All servers run Windows Server 2012 R2. A Group Policy object (GPO) named GPO1 is linked to the organizational unit (OU) that contains Server1.
The following graphic shows the configured settings in GPO1.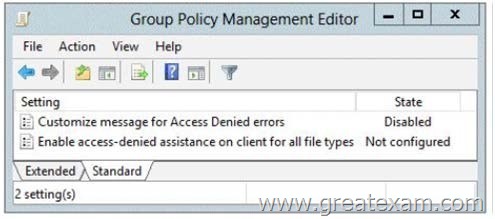
Server1 contains a folder named Folder1. Folder1 is shared as Share1.
You attempt to configure access-denied assistance on Server1, but the Enable accessdenied assistance option cannot be selected from File Server Resource Manager.
You need to ensure that you can configure access- denied assistance on Server1 manually by using File Server Resource Manager.
What should you do?
A. Set the Customize message for Access Denied errors policy setting to Enabled for GPO1.
B. Set the Enable access-denied assistance on client for all file types policy setting to Enabled for GPO1.
C. Set the Customize message for Access Denied errors policy setting to Not Configured for GPO1.
D. Set the Enable access-denied assistance on client for all file types policy setting to Disabled for GPO1.
Answer: C
Explanation:
Ensure that you can configure access-denied assistance
http://technet.microsoft.com/en-us/library/hh831402.aspx#BKMK_1
QUESTION 125
You have a server named FS1 that runs Windows Server 2012 R2.
You install the File and Storage Services server role on FS1.
From Windows Explorer, you view the properties of a shared folder named Share1 and you discover that the Classification tab is missing.
You need to ensure that you can assign classifications to Share1 from Windows Explorer manually.
What should you do?
A. From Folder Options, clear Use Sharing Wizard (Recommend).
B. Install the File Server Resource Manager role service.
C. From Folder Options, select Show hidden files, folders, and drives.
D. Install the Enhanced Storage feature.
Answer: B
QUESTION 126
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains two DHCP servers named DHCP1 and DHCP2 that run Windows Server 2012 R2.
You install the IP Address Management (IPAM) Server feature on a member server named Server1 and you run the Run Invoke-IpamGpoProvisioningcmdlet.
You need to manage the DHCP servers by using IPAM on Server1.
Which three actions should you perform? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.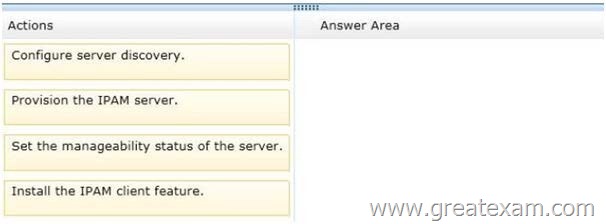
Answer: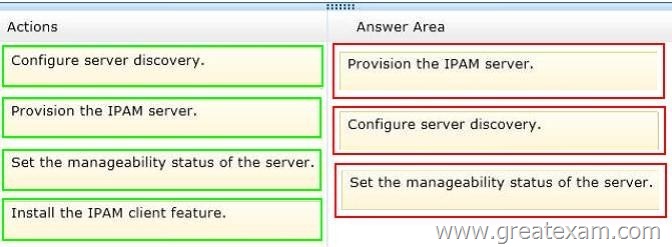
QUESTION 127
Your network contains an Active Directory forest named adatum.com.
All servers run Windows Server 2012 R2.
The domain contains four servers. The servers are configured as shown in the following table.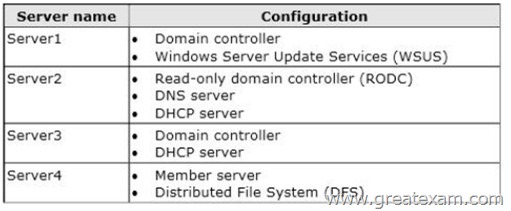
You need to deploy IP Address Management (IPAM) to manage DNS and DHCP.
On which server should you install IPAM?
A. Server1
B. Server2
C. Server3
D. Server4
Answer: D
Explanation:
IPAM can not be installed on a Domain Controller.
QUESTION 128
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the DHCP Server server role installed. An administrator installs the IP Address Management (IPAM) Server feature on a server named Server2. The administrator configures IPAM by using Group Policy based provisioning and starts server discovery.
You plan to create Group Policies for IPAM provisioning.
You need to identify which Group Policy object (GPO) name prefix must be used for IPAM Group Policies.
What should you do on Server2?
A. From Task Scheduler, review the IPAM tasks.
B. From Server Manager, review the IPAM overview.
C. Run the Get-IpamConfigurationcmdlet.
D. Run the ipamgc.exe tool.
Answer: C
Explanation:
https://technet.microsoft.com/en-us/library/jj590817.aspx
QUESTION 129
Your network contains an Active Directory domain named contoso.com.
All domain controllers run Windows Server 2012 R2.
The domain contains an Edge Server named Server 1.
Server1 is configured as a DirectAccess server.
Server1 has the followingsettings:
– Internal DNS name: Server1.contoso.com
– External DNS name: dal.contoso.com
– Internal IPv6 address: 2002:cla8:6a:3333::1
– External IPv4 address: 65.55.37.62
Your company uses split-brain DNS for the contoso.com zone.
You run the Remote Access Setup wizard as shown in the following exhibit. (Click the Exhibit button.)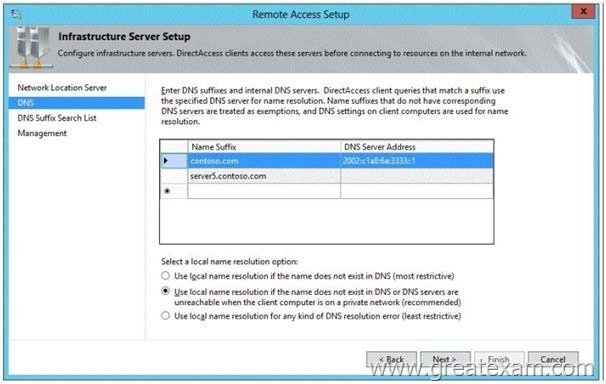
You need to ensure that client computers on the Internet can establish DirectAccess connections to Server1.
Which additional name suffix entry should you add from the Remote Access Setup wizard?
A. A Name Suffix value of server1.contoso.com and a blank DNS Server Address value
B. A Name Suffix value of dal.contoso.com and a DNS Server Address value of 65.55.37.62
C. A Name Suffix value of dal.contoso.com and a blank DNS Server Address value
D. A Name Suffix value of server1.contoso.com and a DNS Server Address value of 65.55.37.62
Answer: C
Explanation:
It says “on the internet” & the external DNS name is Dal.
QUESTION 130
Your company deploys a new Active Directory forest named contoso.com.
The first domain controller in the forest runs Windows Server 2012 R2. The forest contains a domain controller named DC10. On DC10; the disk that contains the SYSVOL folder fails.
You replace the failed disk.
You stop the Distributed File System (DFS) Replication service.
You restore the SYSVOL folder.
You need to perform a non-authoritative synchronization of SYSVOL on DC10.
Which tool should you use before you start the DFS Replication service on DC10?
A. Ldp
B. Active Directory Sites and Services
C. Dfsmgmt.msc
D. Frsutil
Answer: A
Explanation:
You need to change the msDFSR-Enabled value before syncing, so you would need to use ADSIEDIT or another tool such as Ldp.
QUESTION 131
Your network contains an Active Directory forest named contoso.com.
All servers run Windows Server 2012 R2.
You need to create a custom Active Directory Application partition.
Which tool should you use?
A. Netdom
B. Ntdsutil
C. Dsmod
D. Dsamain
Answer: B
Explanation:
* To create or delete an application directory partition Open Command Prompt.
Type:ntdsutil
At the ntdsutil command prompt, type:domain management
At the domain management command prompt, type:connection At the server connections command prompt, type:connect to server ServerName At the server connections command prompt, type:quit
At the domain management command prompt, do one of the following:
* partition management
Manages directory partitions for Active Directory Domain Services (AD DS) or Active Directory Lightweight Directory Services (AD LDS).
This is a subcommand of Ntdsutil and Dsmgmt. Ntdsutil and Dsmgmt are command-line tools that are built into Windows Server 2008 and Windows Server 2008 R2.
/ partition management create nc %s1 %s2
Creates the application directory partition with distinguished name %s1, on the Active Directory domain controller or AD LDS instance with full DNS name %s2. If you specify “NULL” for %s2, this command uses the currently connected Active Directory domain controller. Use this command only with AD DS. For AD LDS, use create nc %s1 %s2 %s3.
Note:
* An application directory partition is a directory partition that is replicated only to specific domain controllers. A domain controller that participates in the replication of a particular application directory partition hosts a replica of that partition.
QUESTION 132
Hotspot Question
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. The forest contains two Active Directory sites named Site1 and Site2.
You plan to deploy a read-only domain controller (RODC) named DC10 to Site2.
You precreate the DC10 domain controller account by using Active Directory Users and Computers.
You need to identify which domain controller will be used for initial replication during the promotion of the RODC.
Which tab should you use to identify the domain controller? To answer, select the appropriate tab in the answer area.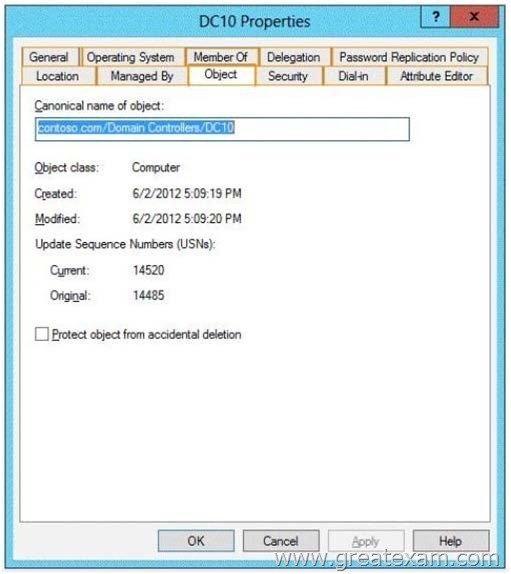
Answer:
QUESTION 133
Your network contains an Active Directory domain named contoso.com.
The domain contains a domain controller named DC1 that runs Windows Server 2012 R2.
You create an Active Directory snapshot of DC1 each day.
You need to view the contents of an Active Directory snapshot from two days ago.
What should you do first?
A. Stop the Active Directory Domain Services (AD DS) service.
B. Run the ntdsutil.exe command.
C. Run the dsamain.exe command.
D. Start the Volume Shadow Copy Service (VSS).
Answer: B
Explanation:
Mounting an Active Directory snapshot
Before connecting to the snapshot we need to mount it. By looking at the results of the List All command in step #8 above, identify the snapshot that you wish to mount, and note the number next to it.
In order to mount an Active Directory snapshot follow these steps:
Log on as a member of the Domain Admins group to one of your Windows Server 2008 Domain Controllers.
Open a Command Prompt window by clicking on the CMD shortcut in the Start menu, or by typing CMD and pressing Enter in the Run or Quick Search parts of the Start menu. Note: You must run NTDSUTIL from an elevated command prompt. To open an elevated command prompt, click Start, right-click Command Prompt, and then click Run as administrator.
In the CMD window, type the following command:
ntdsutil
In the CMD window, type the following command:
snapshot
To view all available snapshots, in the CMD window, type the following command:
list all The result should look like this:
snapshot: List All
1: 2008/10/25:03:14 {ec53ad62-8312-426f-8ad4-d47768351c9a}
2: C: {15c6f880-cc5c-483b-86cf-8dc2d3449348}
In this example we only have one snapshot available, one from 2008/10/25 at 03:14AM (yes, I write articles at this time…). We’ll mount this one.
In the CMD window, type the following command:
mount 2
The result should look like this:
snapshot: mount 2
Snapshot {15c6f880-cc5c-483b-86cf-8dc2d3449348} mounted as
C:’$SNAP_200810250314_VOLUMEC$’
Next, you can leave the NTDSUTIL running, or you can quit by typing quit 2 times. Note: Like the above command, the mounting process can also be run in one line.
However, note that
NTDSUTIL requires that the “list all” command be run in the same session that you mount the snapshot. So in order to mount the snapshot with a one-liner, you will need to run “list all” first.
ntdsutil snapshot “list all” “mount 2” quit quit
Note: You do not need to quit from the NTDSUTIL command, you can keep it open assuming that you’ll probably want to unmount the snapshot right after working with it.
QUESTION 134
You have a server named Server1 that runs Windows Server 2012 R2.
You need to configure Server1 to create an entry in an event log when the processor usage exceeds 60 percent.
Which type of data collector should you create?
A. an event trace data collector
B. a performance counter data collector
C. a performance counter alert
D. a configuration data collector
Answer: C
QUESTION 135
Your network contains an Active Directory domain named contoso.com. The domain contains two member servers named Server1 and Server2. All servers run Windows Server 2012 R2. Server1 and Server2 are nodes in a Hyper-V cluster named Cluster1. Cluster1 hosts 10 virtual machines. All of the virtual machines run Windows Server 2012 R2 and are members of the domain.
You need to ensure that the first time a service named Service1 fails on a virtual machine, the virtual machine is moved to a different node.
You configure Service1 to be monitored from Failover Cluster Manager.
What should you configure on the virtual machine?
A. From the Recovery settings of Service1, set the First failure recovery action to Restart the Service.
B. From the Recovery settings of Service1, set the First failure recovery action to Take No Action.
C. From the General settings, modify the Startup type.
D. From the General settings, modify the Service status.
Answer: B
Explanation:
Configure the virtual machine to take no action through Hyper-V if the physical computer shuts down by modifying the Automatic Stop Action setting to None.
Virtual machine state must be managed through the Failover Clustering feature.
http://technet.microsoft.com/en-us/library/cc742396.aspx
http://windowsitpro.com/windows-server-2012/enable-windows-server-2012-failover-cluster-hyper-v-vmmonitoring
QUESTION 136
Your network contains two servers named Server1 and Server2. Both servers run Windows Server 2012 R2, On Server1, you create a Data Collector Set (DCS) named Data1. You need to export Data1 to Server2. What should you do first?
A. Right-click Data1 and click Data Manager…
B. Right-click Data1 and click Save template…
C. Right-click Data1 and click Properties.
D. Right-click Data1 and click Export list…
Answer: B
Explanation:
To export a Data Collector Set you create as a template for use on other computers, open Windows Performance Monitor, expand Data Collector Sets, right-click the Data Collector Set you want to export, and click Save Template.
Select a directory in which to store the XML file and click Save .
http://technet.microsoft.com/en-us/library/cc766318.aspx
QUESTION 137
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
Server1 has the Remote Desktop Session Host role service installed.
The computer account of Server1 resides in an organizational unit (OU) named OU1.
You create and link a Group Policy object (GPO) named GPO1 to OU1.
GPO1 is configured as shown in the exhibit. (Click the Exhibit button.)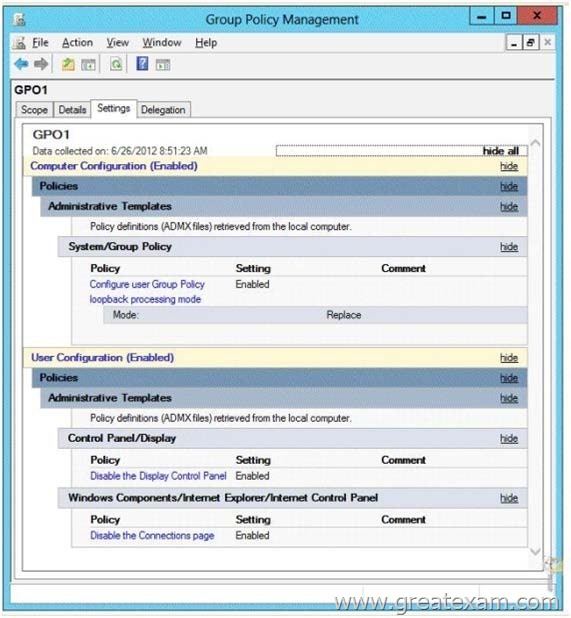
You need to prevent GPO1 from Applying to your user account when you log on to Server1. GPO1 must Apply to every other user who logs on to Server1.
What should you configure?
A. WMI Filtering
B. Item-level Targeting
C. Block Inheritance
D. Security Filtering
Answer: D
Explanation:
Security filtering is a way of refining which users and computers will receive and apply the settings in a Group Policy object (GPO). Using security filtering, you can specify that only certain security principals within a container where the GPO is linked apply the GPO. Security group filtering determines whether the GPO as a whole applies to groups, users, or computers; it cannot be used selectively on different settings within a GPO.
QUESTION 138
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com.
All client computers run Windows 8 Group Policy objects (GPOs) are linked to the domain as shown in the exhibit. (Click the Exhibit button.)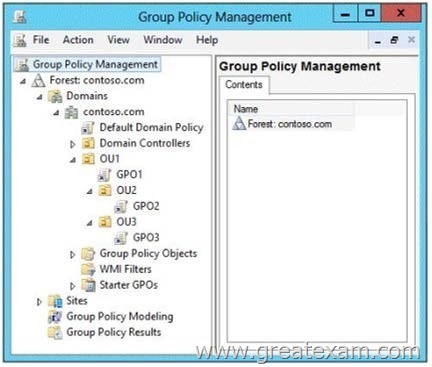
GPO2 contains computer configurations only and GPO3 contains user configurations only.
You need to configure the GPOs to meet the following requirements:
– Ensure that GPO2 only Applies to the computer accounts in OU2 that have more than one processor.
– Ensure that GPO3 only Applies to the user accounts in OU3 that are members of a security group named SecureUsers.
Which setting should you configure in each GPO? To answer, drag the appropriate setting to the correct GPO. Each setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.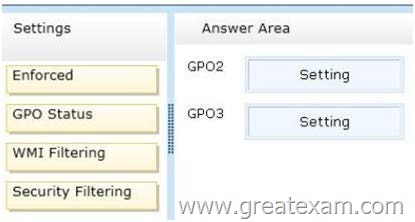
Answer: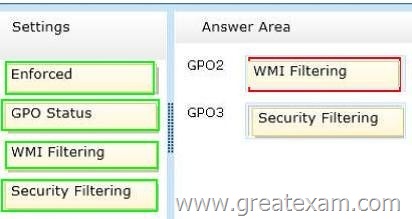
QUESTION 139
Your network contains an Active Directory domain named contoso.com.
All domain controllers run Windows Server 2012 R2. An organizational unit (OU) named OU1 contains 200 client computers that run Windows 8 Enterprise.
A Group Policy object (GPO) named GPO1 is linked to OU1.
You make a change to GPO1.
You need to force all of the computers in OU1 to refresh their Group Policy settings immediately. The solution must minimize administrative effort.
Which tool should you use?
A. The Set-AdComputercmdlet
B. Group Policy Object Editor
C. Active Directory Users and Computers
D. Group Policy Management Console (GPMC)
Answer: D
Explanation:
In the previous versions of Windows, this was accomplished by having the user run GPUpdate.exe on their computer.
Starting with Windows Server® 2012 and Windows® 8, you can now remotely refresh Group Policy settings for all computers in an OU from one central location through the Group Policy Management Console (GPMC). Or you can use the Invoke-GPUpdatecmdlet to refresh Group Policy for a set of computers, not limited to the OU structure, for example, if the computers are located in the default computers container.
http://technet.microsoft.com/en-us//library/jj134201.aspx
http://blogs.technet.com/b/grouppolicy/archive/2012/11/27/group-policy-in-windows-server-2012-using-remote-gpupdate.aspx
QUESTION 140
Your network contains an Active Directory domain named contoso.com. Network Access Protection (NAP) is deployed to the domain.
You need to create NAP event trace log files on a client computer.
What should you run?
A. Logman
B. Tracert
C. Register-EngineEvent
D. Register-ObjectEvent
Answer: A
Explanation:
Register-ObjectEvent: Monitor events generated from .Net Framework Object. Register-EngineEvent: Subscribes to events that are generated by the Windows PowerShell engine and by the New-Event cmdlet.
http://technet.microsoft.com/en-us/library/hh849967.aspx
tracert: Trace IP route
logman: Manages and schedules performance counter and event trace log collections on a local and remote systems.
http://technet.microsoft.com/en-us/library/bb490956.aspx
If you want to get more 70-417 exam preparation material, you can download the free 70-417 braindumps in PDF files on GreatExam. It would be great helpful for your exam. All the 70-417 dumps are updated and cover every aspect of the examination. Welcome to choose.