The Microsoft 70-410 PDF, 70-410 practice test and 70-410 questions and answers at GreatExam are written and prepared by Microsoft affiliated trainers and lecturers with decades of experience in the IT field. This ensures that you are equipped with the latest and most current information to give you a better chance of passing the Microsoft 70-410 exam.
QUESTION 191
You have a new server named Server1 that runs Windows Server 2012 R2. Server1 has two dual-core processors and 32 GB of RAM.
You install the Hyper-V server role on Server1.
You create two virtual machines on Server1 that each have 8 GB of memory.
You need to minimize the amount of time it takes for both virtual machines to access memory.
What should you configure on each virtual machine?
A. Resource control
B. Dynamic Memory
C. NUMA topology
D. Memory weight
Answer: C
Explanation:
Windows Server 2012 introduced support for projecting a virtual NUMA topology into Hyper-V virtual machines. This capability can help improve the performance of workloads running on virtual machines that are configured with large amounts of memory.
QUESTION 192
Hotspot Question
Your network contains an Active Directory domain named contoso.com. Domain controllers run either Windows Server 2008 R2 or Windows Server 2012 R2. All client computers run Windows 8. All computer accounts are located in an organizational unit (OU) named OU1.
You create a Group Policy object (GPO) that contains several AppLocker rules.
You link the GPO to OU1.
You need to ensure that the AppLocker rules apply to all of the client computers.
What should you configure in the GPO? To answer, select the appropriate service in the answer area.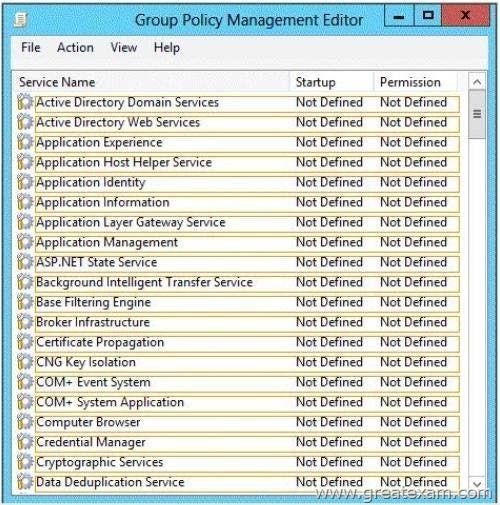
Answer: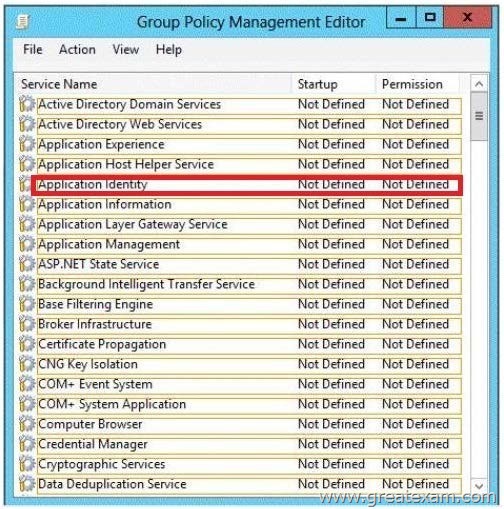
QUESTION 193
Hotspot Question
Your network contains an Active Directory domain named contoso.com. Technicians use Windows Deployment Services (WDS) to deploy Windows Server 2012 R2. The network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. You need to ensure that you can use WDS to deploy Windows Server 2012 R2 to a virtual machine named VM1.
Which settings should you configure?
To answer, select the appropriate settings in the answer area.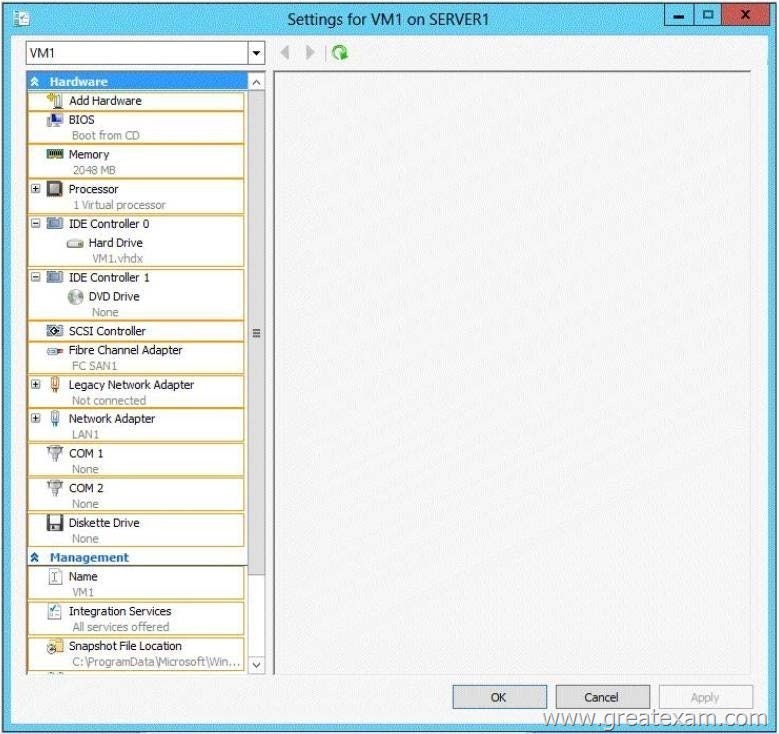
Answer: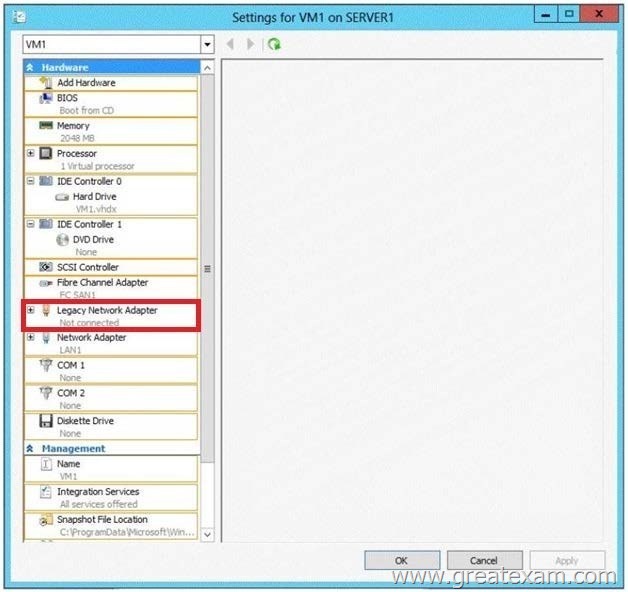
QUESTION 194
Hotspot Question
Your network contains an Active Directory domain named contoso.com.
The domain contains a member server named Hyperv1 and a domain controller named DC1.
Hyperv1 has the Hyper-V server role installed. DC1 is a virtual machine on Hyperv1.
Users report that the time on their client computer is incorrect.
You log on to DC1 and verify that the time services are configured correctly.
You need to prevent time conflicts between the time provided by DC1 and other potential time sources.
What should you configure? To answer, select the appropriate object in the answer area.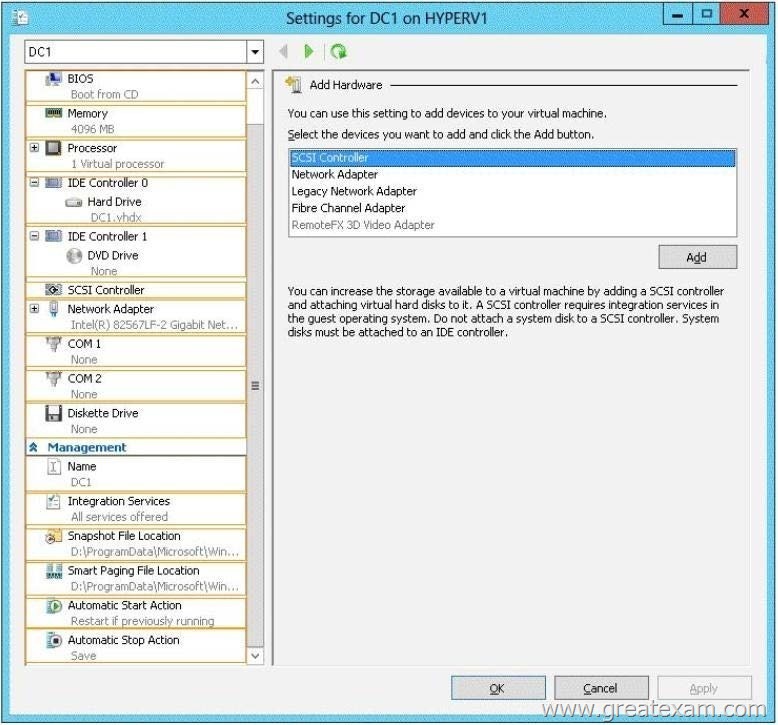
Answer: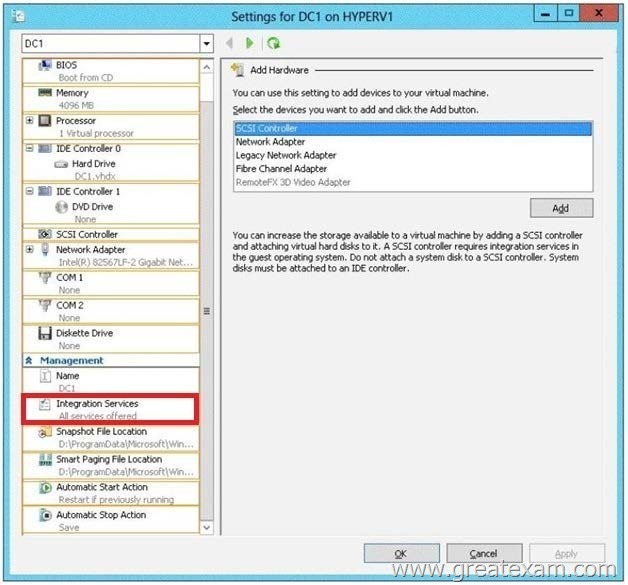
QUESTION 195
You perform a Server Core Installation of Windows Server 2012 R2 on a server named Server1.
You need to add a graphical user interface (GUI) to Server1.
Which tool should you use?
A. the dism.exe command
B. the Add-WindowsFeature cmdlet
C. the imagex.exe command
D. the setup.exe command
E. the ocsetup.exe command
F. the Add-WindowsPackage cmdlet
G. the Install-Module cmdlet
H. the Install-RoleService cmdlet
Answer: AB
Explanation:
Add-WindowsFeature -The Add-WindowsFeature cmdlet allows you to install specified roles, role services, and features on a computer that is running Windows Server 2008 R2.
Install-WindowsFeature -Installs one or more Windows Server roles, role services, or features on either the local or a specified remote server that is running Windows Server 2012 R2.
This cmdlet is equivalent to and replaces Add-WindowsFeature, the cmdlet that was used to install roles, role services, and features in Windows Server 2008 R2.
dism /online /get-features PS C:\> Install-WindowsFeature -Name Web-Server –
IncludeAllSubFeature -ComputerName Server1 -WhatIf
http://technet.microsoft.com/en-us/library/hh824822.aspx
http://technet.microsoft.com/en-us/library/dd744582(v=ws.10).aspx http://technet.microsoft.com/en-us/library/jj205467(v=wps.620).aspx
QUESTION 196
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has the Hyper-V server role installed.
You need to configure storage for a virtual machine to meet the following requirements:
– Support up to 3 TB of data on a single hard disk.
– Allocate disk space as needed.
– Use a portable storage format.
What should you configure?
A. A pass-through disk
B. A fixed-size VHD
C. A dynamically expanding VHD
D. A fixed-size VHDX
E. A dynamically expanding VHDX
Answer: E
Explanation:
http://technet.microsoft.com/en-us/library/hh831446.aspx
Support for virtual hard disk storage capacity of up to 64 TB.
vhd max is 2TB
QUESTION 197
Your network contains an Active Directory domain named contoso.com.
All user accounts are in an organizational unit (OU) named Employees.
You create a Group Policy object (GPO) named GP1.
You link GP1 to the Employees OU.
You need to ensure that GP1 does not apply to the members of a group named Managers.
What should you configure?
A. The Security settings of Employees
B. The WMI filter for GP1
C. The Block Inheritance option for Employees
D. The Security settings of GP1
Answer: D
Explanation:
A. Wrong Group
B. Windows Management Instrumentation (WMI) filters allow you to dynamically determine the scope of Group Policy objects (GPOs) based on attributes of the target computer.
C. Blocking inheritance prevents Group Policy objects (GPOs) that are linked to higher sites, domains, or organizational units from being automatically inherited by the child-level.
D. Set Managers to – Members of this security group are exempt from this Group Policy object.
Security settings.
You use the Security Settings extension to set security options for computers and users within the scope of a Group Policy object.
You can define local computer, domain, and network security settings.
Figure belows shows an example of the security settings that allow everyone to be affected by this GPO except the members of the Management group, who were explicitly denied permission to the GPO by setting the Apply Group Policy ACE to Deny. Note that if a member of the Management group were also a member of a group that had an explicit Allow setting for the Apply Group Policy ACE, the Deny would take precedence and the GPO would not affect the user.
http://technet.microsoft.com/en-us/library/bb742376.aspx
http://technet.microsoft.com/en-us/library/cc786636(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc731076.aspx
http://technet.microsoft.com/en-us/library/cc779036(v=ws.10).aspx
QUESTION 198
You have a virtual machine named VM1.
You install Windows Server 2012 R2 on VM1.
You plan to use VM1 as an image that will be distributed to sales users to demonstrate the features of a custom application. The custom application only requires the Web Server (IIS) server role to be installed.
You need to ensure that the VHD file for VM1 only contains the required Windows Server 2012 R2 source files.
Which tool should you use?
A. dism.exe
B. ocsetup.exe
C. imagex.exe
D. servermanagercmd.exe
Answer: A
Explanation:
http://technet.microsoft.com/en-us/magazine/dd490958.aspx
You can use DISM to:
Add, remove, and enumerate packages and drivers.
Enable or disable Windows features.
Apply changes based on the offline servicing section of an unattend.xml answer file.
Configure international settings.
Upgrade a Windows image to a different edition.
Prepare a Windows PE image.
Take advantage of better logging.
Service down-level operating systems like Windows Vista with SP1 and Windows Server 2008.
Service all platforms (32-bit, 64-bit, and Itanium).
Service a 32-bit image from a 64-bit host and service a 64-bit image from a 32-bit host.
Make use of old Package Manager scripts.
QUESTION 199
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 runs Windows Server 2012 R2 and has the Hyper-V server role installed. On Server1, you create and start a virtual machine named VM1. VM1 is configured as shown in the following table.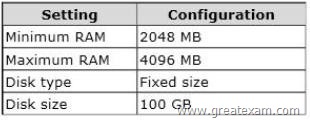
You plan to create a snapshot of VM1.
You need to recommend a solution to minimize the amount of disk space used for the snapshot of VM1.
What should you do before you create the snapshot?
A. Run the Stop-VM cmdlet.
B. Run the Convert-VHD cmdlet.
C. Decrease the Maximum RAM
D. Decrease the Minimum RAM.
Answer: A
Explanation:
What are virtual machine snapshots?
Virtual machine snapshots capture the state, data, and hardware configuration of a running virtual machine.
What are snapshots used for?
Snapshots provide a fast and easy way to revert the virtual machine to a previous state. For this reason, virtual machine snapshots are intended mainly for use in development and test environments. Having an easy way to revert a virtual machine can be very useful if you need to recreate a specific state or condition so that you can troubleshoot a problem.
There are certain circumstances in which it may make sense to use snapshots in a production environment. For example, you can use snapshots to provide a way to revert a potentially risky operation in a production environment, such as applying an update to the software running in the virtual machine.
How are snapshots stored?
Snapshot data files are stored as .avhd files. Taking multiple snapshots can quickly consume storage space. In the first release version of Hyper-V (KB950050) and in Hyper-V in Windows Server 2008 Service Pack 2, snapshot, snapshot data files usually are located in the same folder as the virtual machine by default. In Hyper-V in Windows Server 2008 R2, the files usually are located in the same folder as the virtual hard disk. The following exceptions affect the location of the snapshot data files: If the virtual machine was imported with snapshots, they are stored in their own folder. If the virtual machine has no snapshots and you configure the virtual machine snapshot setting, all snapshots you take afterwards will be stored in the folder you specify.
http://technet.microsoft.com/pt-pt/library/dd560637%28v=ws.10%29.aspx
Reducing the available RAM for the VM would reduce the size of the snapshot,what better than have the machine turn off, not using any memory 😉
QUESTION 200
Your network contains an Active Directory domain named contoso.com.
The domain contains a file server named Server1 that runs Windows Server 2012 R2.
Server1 contains a shared folder named Share1. Share1 contains the home folder of each user.
All users have the necessary permissions to access only their home folder.
The users report that when they access Share1, they can see the home folders of all the users.
You need to ensure that the users see only their home folder when they access Share1.
What should you do from Server1?
A. From Windows Explorer, modify the properties of the volume that contains Share1.
B. From Server Manager, modify the properties of the volume that contains Share1.
C. From Server Manager, modify the properties of Share1.
D. From Windows Explorer, modify the properties of Share1.
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/cc784710(v=ws.10).aspx
Access based enumeration needs to be enabled:
QUESTION 201
In an isolated test environment, you deploy a server named Server1 that runs a Server Core Installation of Windows Server 2012 R2.
The test environment does not have Active Directory Domain Services (AD DS) installed.
You install the Active Directory Domain Services server role on Server1.
You need to configure Server1 as a domain controller.
Which cmdlet should you run?
A. Install-ADDSDomainController
B. Install-ADDSDomatn
C. Install-ADDSForest
D. Install-WindowsFeature
Answer: C
Explanation:
Install-ADDSDomainController – Installs a domain controller in Active Directory.
Install-ADDSDomain – Installs a new Active Directory domain configuration.
Install-ADDSForest – Installs a new Active Directory forest configuration.
Install-WindowsFeature – Installs one or more Windows Server roles, role services, or features on either thelocal or a specified remote server that is running Windows Server 2012 R2.
This cmdlet is equivalent to andreplaces Add-WindowsFeature, the cmdlet that was used to install roles, role services, and features.
C:\PS>Install-ADDSForest -DomainName corp.contoso.com -CreateDNSDelegation DomainMode Win2008 – ForestMode Win 2008 R2 – DatabasePath “d:\NTDS” -SysvolPath “d:\SYSVOL” -LogPath “e:\Logs”
Installs a new forest named corp.contoso.com, creates a DNS delegation in the contoso.com domain, setsdomain functional level to Windows Server 2008 R2 and sets forest functional level to Windows Server 2008,installs the Active Directory database and SYSVOL on the D:\ drive, installs the log files on the E:\ drive andhas the server automatically restart after AD DS installation is complete and prompts the user to provide andconfirm the Directory Services Restore Mode (DSRM) password. http://technet.microsoft.com/en-us/library/hh974720%28v=wps.620%29.aspx
QUESTION 202
Your network contains an Active Directory domain named adatum.com.
You discover that when users join computers to the domain, the computer accounts are created in the Computers container.
You need to ensure that when users join computers to the domain, the computer accounts
are automatically created in an organizational unit (OU) named All_Computers.
What should you do?
A. From a command prompt, run the redircmp.exe command.
B. From Windows PowerShell, run the Move-ADObject cmdlet.
C. From Ldp, configure the properties of the Computers container.
D. From ADSI Edit, configure the properties of the OU1 object.
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/cc770619.aspx
Redirects the default container for newly created computers to a specified, target organizational unit (OU) so that newly created computer objects are created in the specific target OU instead of in CN=Computers.
QUESTION 203
Drag and Drop Question
You are configuring a test network. The test network contains a subnet named LAN1.
LAN1 uses the network ID of 10.10.1.0/27.
You plan to add a new subnet named LAN2 to the test network.
LAN1 and LAN2 will be connected by a router.
You need to identify a valid network ID for LAN2 that meets the following requirements:
– Ensures that hosts on LAN2 can communicate with hosts on LAN1.
– Supports at least 100 IPv4 hosts.
– Uses only private IP addresses.
Which network ID should you use? To answer, drag the appropriate network ID and subnet mask to the correct location in the answer area.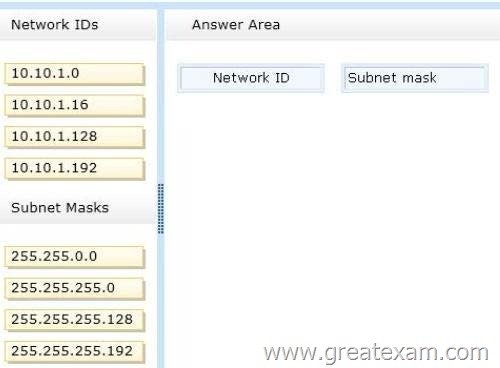
Answer: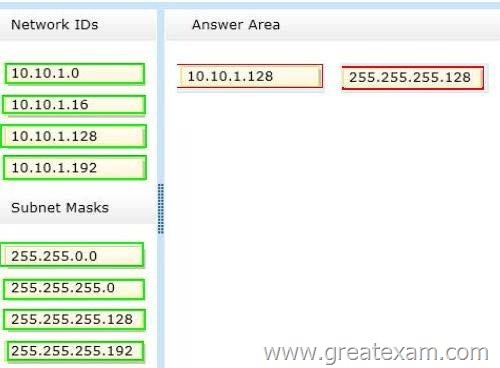
QUESTION 204
Hotspot Question
You have a Hyper-V host named HYPERV1. HYPERV1 hosts a virtual machine named DC1.
You need to prevent the clock on DC1 from synchronizing from the clock on HYPERV1.
What should you configure? To answer, select the appropriate object in the answer area.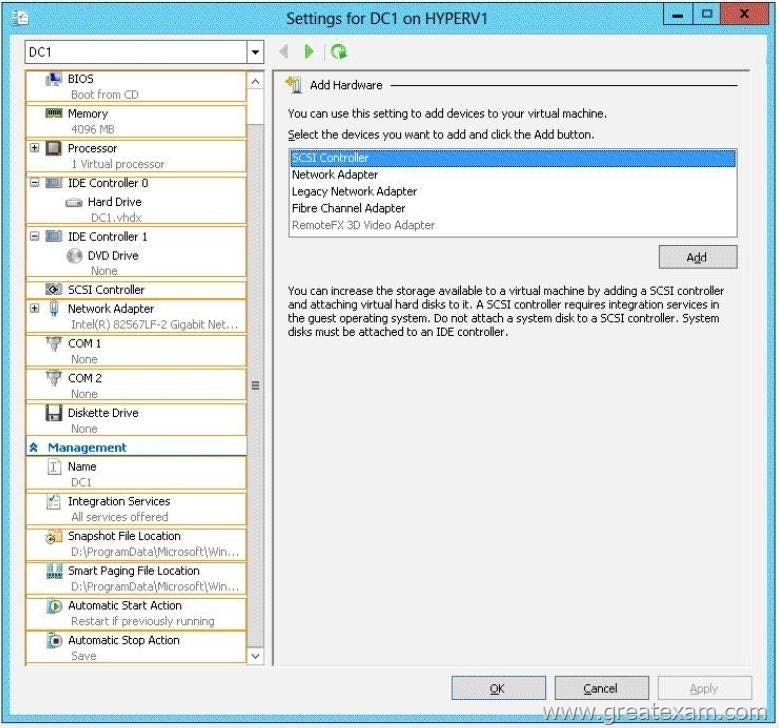
Answer: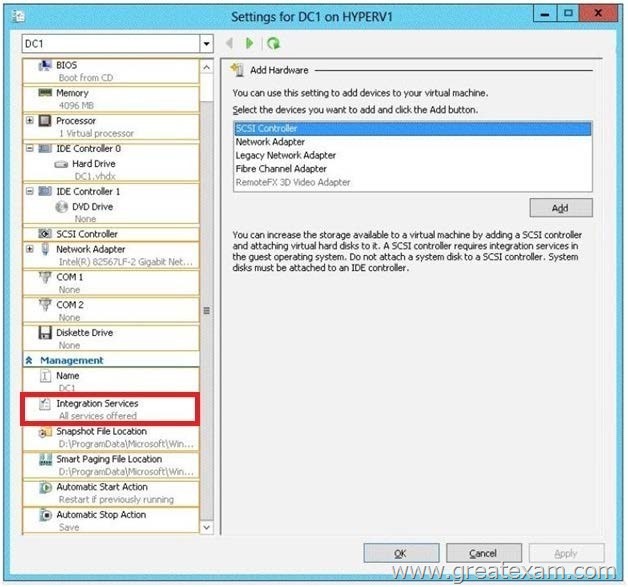
QUESTION 205
Hotspot Question
Your network contains a subnet named Subnet1. Subnet1 contains a DHCP server named Server1. You deploy a new subnet named Subnet2. On Subnet2, you deploy a new server named 5erver2 that runs Windows Server 2012 R2.
You need to configure Server2 to route DHCP broadcast from Subnet2 to Server1.
Which server role should you install on Server2? To answer, select the appropriate role in the answer area.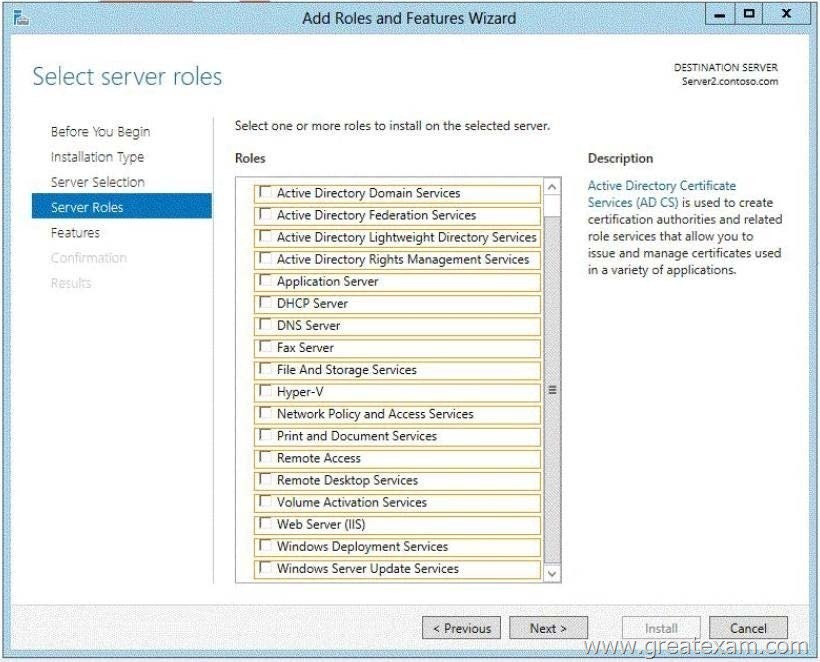
Answer:
QUESTION 206
Your network contains an Active Directory domain named contoso.com. The domain contains a user account named User1 that resides in an organizational unit (OU) named OU1. A Group Policy object (GPO) named GPO1 is linked to OU1. GPO1 is used to publish several applications to a user named User1. In the Users container, you create a new user named User2.
You need to ensure that the same applications are published to User2.
What should you do?
A. Modify the security of GPO1.
B. Modify the settings in GPO1.
C. Link a WMI filter to GPO1.
D. Move User2 to OU1.
Answer: D
Explanation:
The GPO is linked to OU1. By moving User2 to OU1 the GPO will be applied to this user.
QUESTION 207
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains a member server named Server1. Server1 runs Windows Server 2012 and has the File Server server role installed. On Server1, you create a share named Documents. The Share permission for the Documents share is configured as shown in the following table.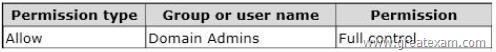
The NTFS permission for the Documents share is configured as shown in the following table.
You need to configure the Share and NTFS permissions for the Documents share.
The permissions must meet the following requirements:
– Ensure that the members of a group named Group1 can read files and run programs in – Documents. Ensure that the members of Group1 can modify the permissions on their own files in Documents.
– Ensure that the members of Group1 can create folders and files in Documents.
– Minimize the number of permissions assigned to users and groups.
How should you configure the permissions? To answer, drag the appropriate permission to the correct location. Each permission may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Answer: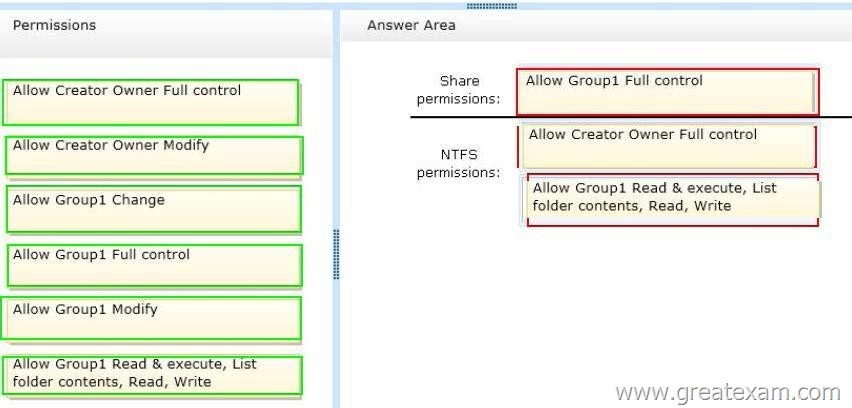
QUESTION 208
Hotspot Question
Your network contains an Active Directory forest. The forest contains two domains named Domain1 and Domain2. Domain1 contains a file server named Server1. Server1 has a shared folder named Share1. Domain2 contains 50 users who require access to Share1.
You need to create groups in each domain to meet the following requirements:
– In Domain1, create a group named Group1. Group1 must be granted access to Share1.
– In Domain2, create a group named Group2. Group2 must contain the user accounts of the 50 users.
– Permission to Share1 must only be assigned directly to Group1.
Which type of groups should you create and which group nesting strategy should you use? To answer, select the appropriate configuration in the answer area.
Answer:
Explanation:
Any group, whether it is a security group or a distribution group, is characterized by a scope that identifies the extent to which the group is applied in the domain tree or forest. The boundary, or reach, of a group scope is also determined by the domain functional level setting of the domain in which it resides. There are three group scopes:
universal, global, and domain local.
http://support.microsoft.com/default.aspx?scid=kb;EN-US;231273 http://technet.microsoft.com/en-us/library/cc772723%28WS.10%29.aspx http://technet.microsoft.com/pt-br/library/cc728188%28WS.10%29.aspx http://technet.microsoft.com/en-us/library/cc755692%28WS.10%29.aspx
QUESTION 209
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 installed.
L2P.com has a server, named L2P-SR07, which has the AD DS, DHCP, and DNS server roles installed. L2P.com also has a server, named L2P-SR08, which has the DHCP, and Remote Access server roles installed.
You have configured a server, which has the File and Storage Services server role installed, to automatically acquire an IP address. The server is named L2PSR09.
You then create a filter on L2P-SR07.
Which of the following is a reason for this configuration?
A. To make sure that L2P-SR07 issues L2P-SR09 an IP address.
B. To make sure that L2P-SR07 does not issue L2P-SR09 an IP address.
C. To make sure that L2P-SR09 acquires a constant IP address from L2P-SR08 only.
D. To make sure that L2P-SR09 is configured with a static IP address.
Answer: B
Explanation:
Enable and Configure MAC Address Filtering MAC address filtering (aka link-layer filtering) is a feature for IPv4 addresses that allows you to include or exclude computers and devices based on their MAC address.
Denying a Single MAC Address You can see from the first figure that we’ve got a system that this DHCP server has given an address lease. Just to demonstrate the simplest possible case of MAC filtering in DHCP, let’s block that system from ever getting an IP address from this DHCP server again. To deny MAC ADDRESS from getting an IP address, right-click the PC entry in the “Address Leases” folder, then choose Add to Filter / Deny, as you see in the following figure:
At this point, the “Deny” folder has a rule in it, as you can see by opening the Filters / Deny folder:
If you had more than one existing lease that you wanted to add to the “deny” filter (or, for that matter, the “allow” filter) then you could also multi-select or block-select any number of existing leases, right-click and then deny (or allow) them en masse.
You must enable Deny filter for it to work.
http://technet.microsoft.com/en-us/magazine/ff521761.aspx
http://blogs.technet.com/b/teamdhcp/archive/2012/11/10/dhcp-mac-address-filter-management-made- easy-with-dhcp-powershell.aspx
http://technet.microsoft.com/en-us/library/hh831825.aspx
http://technet.microsoft.com/en-us/library/jj200226.aspx
QUESTION 210
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1. Server1 runs Windows Server 2012 R2.
You need to create 3-TB virtual hard disk (VHD) on Server1.
Which tool should you use?
A. New-StorageSubsytemVirtualDisk
B. File Server Resource Manager (FSRM)
C. Server Manager
D. Computer Management
Answer: D
Explanation:
For other questions to create a VHD (file) you can use computer management.
– Share and storage management (2008 only)
– New-storagesubsystemVirtualDisk (this is a virtual disk, NOT a virtual hard disk)
– Server Manager (you would use this to create virtual disks, not virtual hard disks)
GreatExam guarantees your 70-410 exam success with our exam resources. Our 70-410 braindumps are the latest and developed by experienced IT certification professionals working in today’s prospering companies and data centers. All our 70-410 braindumps include 70-410 real exam questions which guarantee your 100% success of 70-410 exam in your first try.