Are you struggling for the 70-342 exam? Good news, GreatExam Microsoft technical experts have collected all the questions and answers which are updated to cover the knowledge points and enhance candidates’ abilities. We offer the latest 70-342 PDF and VCE dumps with new version VCE player for free download, and the new 70-342 practice test ensures your 70-342 exam 100% pass.
QUESTION 56
Drag and Drop Question
You have a server that has Exchange Server 2013 installed.
You plan to configure Unified Messaging (UM) to connect to an IP-PBX.
A telecommunications administrator configures the following numbers on the IP-PBX:
– First extension number: 12100
– Last extension number: 12499
– Help extension number: 12500
– Incoming pilot number: 12000
You need to configure UM to support the following requirements:
– Users must be able to use Outlook Voice Access.
– Users must be able to receive voice mail when callers connect to the users’ extension.
– Callers must be able to dial into an automated help system hosted by your company, which uses standard menus and speech-enabled menus.
Which numbers should you use for the UM configurations? To answer, drag the appropriate number to the correct UM object in the answer area. Each number may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
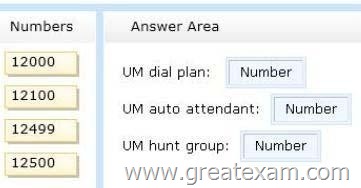
Answer: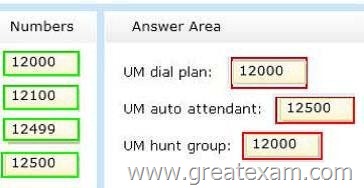
Explanation:
Box 1: 12000
Box 2: 12500
Box 3: 12000
Note:
* An Outlook Voice Access number lets a user who is enabled for Unified Messaging (UM) and voice mail access their mailbox using Outlook Voice Access. When you configure an Outlook Voice Access or subscriber access number on a dial plan, UM-enabled users can call in to the number, sign in to their mailbox, and access their email, voice mail, calendar, and personal contact information. By default, when you create a UM dial plan, an Outlook Voice Access number isn’t configured. To configure an Outlook Voice Access number, you first need to create the dial plan, and then configure an Outlook Voice Access number under the dial plan’s Outlook Voice Access option. Although an Outlook Voice Access number isn’t required, you need to configure at least one Outlook Voice Access number to enable a UM-enabled user to use Outlook Voice Access to access to their Exchange 2013 mailbox. You can configure multiple Outlook Voice Access numbers for a single dial plan.
* After you create a Unified Messaging (UM) auto attendant, incoming calls to an external telephone number that a human operator would ordinarily answer are answered by the auto attendant. Unlike with other Unified Messaging components, such as UM dial plans and UM IP gateways, you aren’t required to create UM auto attendants. However, auto attendants help internal and external callers locate users or departments that exist in an organization and transfer calls to them.
* Hunt group is a term used to describe a group of Private Branch eXchange (PBX) or IP PBX extension numbers that are shared by users. Hunt groups are used to efficiently distribute calls into or out of a specific business unit. Creating and defining a hunt group minimizes the chance that a caller who places an incoming call will receive a busy signal when the call is received. In a telephony network, a PBX or an IP PBX can be configured to have a single hunt group or multiple hunt groups. Each hunt group created on a PBX or IP PBX must have an associated pilot number. Using a pilot number helps to eliminate busy signals and to route incoming calls to the extension numbers that are available. The PBX or IP PBX uses the pilot number to locate the hunt group and in turn to locate the telephone extension number on which the incoming call was received and the extensions that are assigned to the hunt group. Without a defined pilot number, the PBX or IP PBX can’t locate where the incoming call was received.
Reference: Create a UM Auto Attendant
QUESTION 57
Drag and Drop Question
You are an administrator for a company named Contoso, Ltd. The company is an international reseller that has offices worldwide. One of the offices is located in France.
Each office contains several servers that have Exchange Server 2013 installed.
The Exchange Server organization is configured for Unified Messaging (UM).
Each office contains an IP-PBX device.
You need to ensure that callers to the France office can navigate the voice mail system menu in French.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.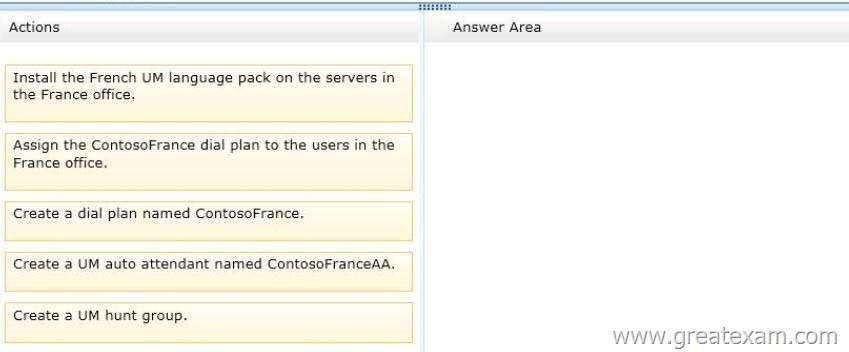
Answer: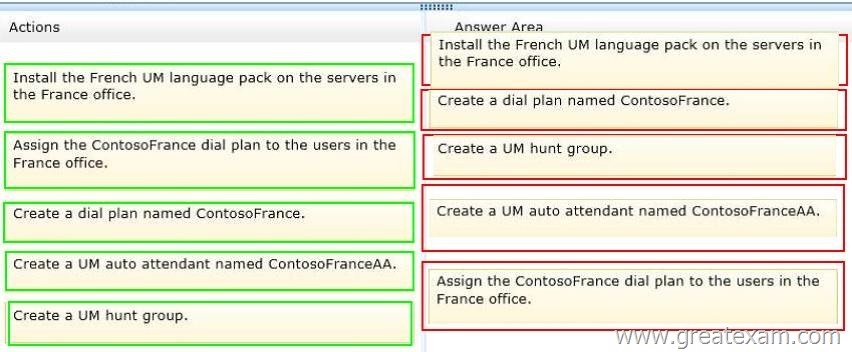
QUESTION 58
You have an Exchange Server 2013 organization.
You successfully migrate the public folders from a previous version of Exchange Server.
You discover that one of the public folder mailboxes almost reached its quota size.
You need to move some of the public folders in the public folder mailbox to another public folder mailbox.
What should you run?
A. Split-PublicFolderMailbox.ps1
B. Set-MailPublicFolder
C. Update-PublicFolderMailbox
D. Set-PublicFolderMailbox
Answer: A
Explanation:
You can either perform a publicfoldermoverequest, or run the splitpublicfoldermailbox.ps1 script.
* Split-PublicFolderMailbox.ps1
Splits the given public folder mailbox based on the size of the folders.
* If the content of a public folder mailbox begins to exceed your mailbox quotas, you may need to move public folders to a different public folder mailbox.
There are a couple ways to do this. To move one or more public folders that don’t contain subfolders, you can use the PublicFolderMoveRequest cmdlets.
Reference: Move a Public Folder to a Different Public Folder Mailbox
QUESTION 59
You have a hybrid deployment of Exchange Server 2013 and Microsoft Office 365. The network does not have Active Directory Federation Services (AD FS) 2.0 installed. A user named User1 reports that he cannot access his mailbox because his account is locked out.
You verify that the mailbox of User2 is hosted on Office 365.
You need to unlock the account of User1. Which cmdlet should you run?
A. Set-MailUser
B. Set-MSolUser
C. Set-Mailbox
D. Set-ADUser
Answer: B
Explanation:
Applies To: Office 365, Windows Azure, Windows Intune
The Set-MsolUser cmdlet is used to update a user object.
Parameters include:
-BlockCredential <Boolean>
When true, the user will not be able to sign in using their user ID.
Incorrect:
Not C: Set-Mailbox
Use the Set-Mailbox cmdlet to modify the settings of an existing mailbox.
Applies to: Exchange Server 2013, Exchange Online
http://blogs.inframon.com/post/2012/08/07/Office-365-User-Account-Lockout.aspx
QUESTION 60
You have a hybrid deployment of Exchange Server 2013 and Office 365. The mail flow between Office 365 and the on-premises Exchange Server environment is routed through an Exchange Server 2010 Edge Transport server.
Your company is assigned a new set of public IP addresses. A network administrator updates the external firewall address and all of the associated DNS records.
Office 365 users report that they cannot receive email messages from on-premises users.
You discover that outgoing email messages to Office 365 are in the Office 365 SMTP queue on an Edge server.
You need to ensure that the on-premises users can send email messages successfully to the
Office 365 users. Which tool should you use?
A. The Exchange Management Console
B. The Exchange Control Panel in Office 365
C. The Exchange Admin Center
D. The Exchange Remote Connectivity Analyzer
Answer: C
Explanation:
Note:
* The section describes the user interface elements that are common across the EAC (Exchange Admin Center).
QUESTION 61
Drag and Drop Question
You have an Exchange Server organization named adatum.com. The organization contains servers that have Exchange Server 2010 and Exchange Server 2013 installed.
The company executives require that all email messages remain stored for three years.
You create two retention tags named Ret1 and Ret2. Ret1 moves the email messages to an Archive mailbox after one year. Ret2 permanently deletes the email messages after three years.
You need to meet the company executives’ requirements.
The solution must ensure that all email messages that are older than two years are removed as quickly as possible.
Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)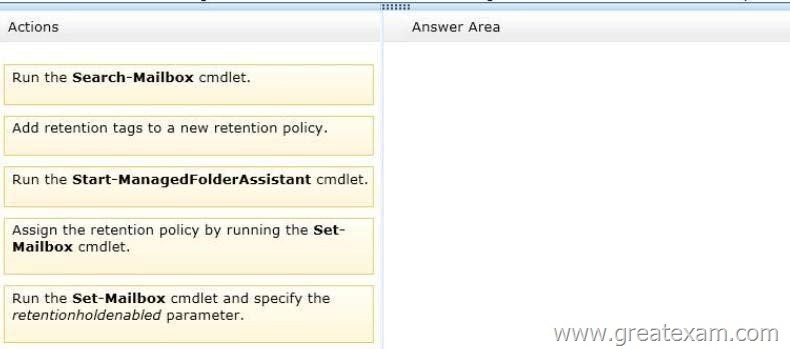
Answer: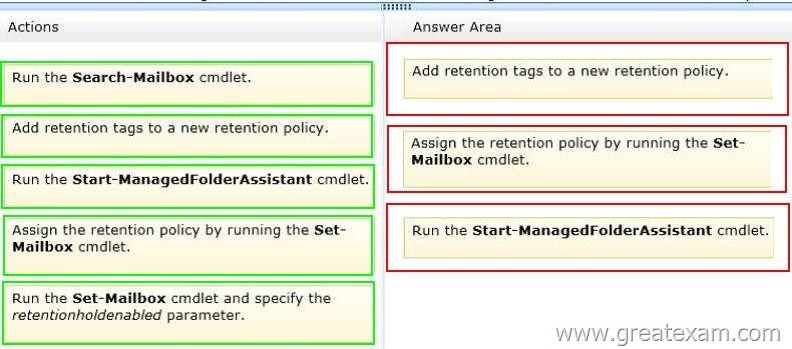
QUESTION 62
You have an Exchange Server 2013 organization named adatum.com.
The organization contains five Mailbox servers.
You need to prevent a user named User8 from permanently deleting an email message in his mailbox.
What should you do on the mailbox of User8?
A. Configure an in-place hold.
B. Create an Archive mailbox.
C. Configure a retention hold.
D. Create a Retention tag.
Answer: A
Explanation:
In Exchange 2013, you can use In-Place Hold to accomplish the following goals:
Place user mailboxes on hold and preserve mailbox items immutably Preserve mailbox items deleted by users or automatic deletion processes such as MRM Use query-based In-Place Hold to search for and retain items matching specified criteria Preserve items indefinitely or for a specific duration Place a user on multiple holds for different cases or investigations Keep In-Place Hold transparent from the user by not having to suspend MRM Enable In-Place eDiscovery searches of items placed on hold
Note:
When a reasonable expectation of litigation exists, organizations are required to preserve
electronically stored information (ESI), including email that’s relevant to the case.
This expectation often exists before the specifics of the case are known, and preservation is often broad. Organizations may need to preserve all email related to a specific topic or all email for certain individuals.
Failure to preserve email can expose an organization to legal and financial risks such as scrutiny of the organization’s records retention and discovery processes, adverse legal judgments,
sanctions, or fines.
http://technet.microsoft.com/en-us/library/ff637980%28v=exchg.150%29.aspx
QUESTION 63
You have an Exchange Server 2013 organization named adatum.com.
You have a database availability group (DAG) that contains four Exchange servers named Server1, Server2, Server3, and Server4. The file share witness is on a server named Share1.
The organization has two Send connectors.
The Send connectors are configured as shown in the following table.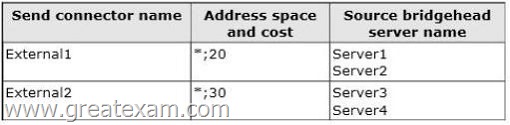
Users report that email sent to external recipients is not being received.
You discover that outbound email messages are queued on Server3 and Server4.
You need to ensure that all of the email messages queued on Server3 and Server4 are delivered to the Internet as quickly as possible.
What should you do?
A. Modify the cost of External.
B. Disable External1.
C. Modify the list of source bridgehead servers of External2.
D. Modify the cost of External1.
Answer: B
Explanation:
Note:
* In Microsoft Exchange Server 2013, a Send connector controls the flow of outbound messages to the receiving server.
* When a message is to be delivered to a remote delivery group, a routing path must be determined for the message. Exchange 2013 uses the same logic as Exchange 2010 to select the routing path for a message:
Calculate the least-cost routing path by adding the cost of the IP site links that must be traversed to reach the destination. If the destination is a connector, the cost assigned to the address space is added to the cost to reach the selected connector. If multiple routing paths are possible, the routing path with the lowest aggregate cost is used;
If more than one routing path has the same cost, the routing path with the least number of hops is used;
If more than one routing path is still available, the name assigned to the AD sites before the destination is considered. The routing path where the AD site nearest the destination is lowest in alphanumeric order is used. If the site nearest the destination is the same for all routing paths being evaluated, an earlier site name is considered.
http://social.technet.microsoft.com/Forums/exchange/en-US/3b89aecd-68c9-40d6-8573-eefb806e61f7/how-to-get-a-backup-send-connector-to-take-over?forum=exchange2010
QUESTION 64
You are a network administrator for a company named Humongous Insurance. Humongous Insurance has an Active Directory forest that contains two domains.
You install the Active Directory Rights Management Services server role on a server named ADRMS1. The Active Directory Rights Management Services (AD RMS) server uses an internal certification authority (CA) for all certificates.
You plan to provide users with the ability to use AD RMS to protect all of the email messages sent to a partner company named Contoso, Ltd.
Contoso does not have AD RMS deployed.
You need to identify which components from the Humongous Insurance network must be accessible to Contoso to ensure that the users at Contoso can open protected messages.
Which two components should you identify? (Each correct answer presents part of the solution. Choose two.)
A. the AD RMS cluster
B. the certificate revocation list (CRL)
C. the Active Directory domain controllers
D. the Client Access servers
E. the Mailbox servers
F. the Global Catalog servers
Answer: BC
Explanation:
B: The CRL is exactly what its name implies: a list of subscribers paired with digital certificate status. The list enumerates revoked certificates along with the reason(s) for revocation. The dates of certificate issue, and the entities that issued them, are also included. In addition, each list contains a proposed date for the next release. When a potential user attempts to access a server, the server allows or denies access based on the CRL entry for that particular user.
C: If federation cannot be implemented and the external organization cannot implement their own AD RMS infrastructure, hosting the user accounts can be the best option.
However, the cost of managing such accounts (for both the IT department and each user) must be considered. In this case, the users will need to be authenticated by a domain controller.
QUESTION 65
You have an Exchange Server organization that contains four servers.
The servers are configured as shown in the following table.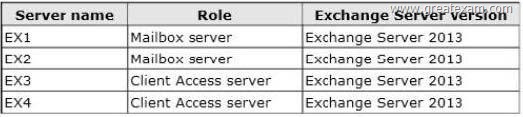
You are deploying Unified Messaging (UM).
You create a dial plan named UMPIan1 and a UM mailbox policy named UMPlan Mailbox Policy.
You need to ensure that all voice mail sent to the existing extension of a user is delivered to the user’s mailbox.
Which three actions should you perform? (Each correct answer presents part of the solution. Choose three.)
A. Create a UM hunt group
B. Create a UM IP gateway.
C. Configure the IP-PBX to route calls to EX3 and EX4
D. Configure the IP-PBX to route calls to EX1 and EX2.
E. Assign EX1 and EX2 to UMPIan1.
F. Assign EX3 and EX4 to UMPIan1.
Answer: ABC
Explanation:
Here are the basic steps for connecting VoIP gateways, IP PBXs, SIP-enabled PBXs, or SBCs to Client Access and Mailbox servers:
Step 1: Install the Client Access and Mailbox servers in your organization.
Step 2: Create and configure a Telephone Extension, SIP URI, or E.164 UM dial plan.
Step 3: Create and configure a UM IP gateway. You must create and configure a UM IP gateway for each VoIP gateway, IP PBX, SIP-enabled PBX, or SBC that will be accepting incoming calls and sending outgoing calls.
Step 4: Create a new UM hunt group if needed. If you create a UM IP gateway and don’t specify a UM dial plan, a UM hunt group will be automatically created.
QUESTION 66
Drag and Drop Question
You have an Exchange Server 2013 organization that contains two Mailbox servers and two Client Access servers.
You have an Active Directory Rights Management Services (AD RMS) cluster.
Information Rights Management (IRM) is enabled for the Exchange Server organization.
All company executives are in a security group named Execs. All of the executives use smartphones that are managed by using a mobile device mailbox policy. The executives frequently read IRM-protected email messages by using Microsoft Outlook.
You need to ensure that the executives can read the IRM-protected messages on their smartphone.
Which task should you perform in each environment? (To answer, drag the appropriate tasks to the correct environments. Each task may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)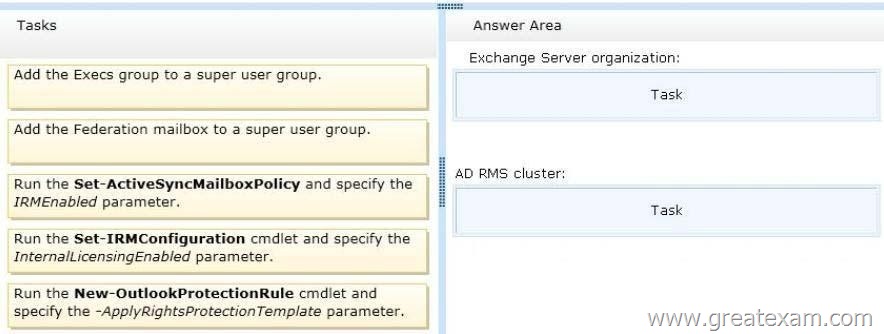
Answer: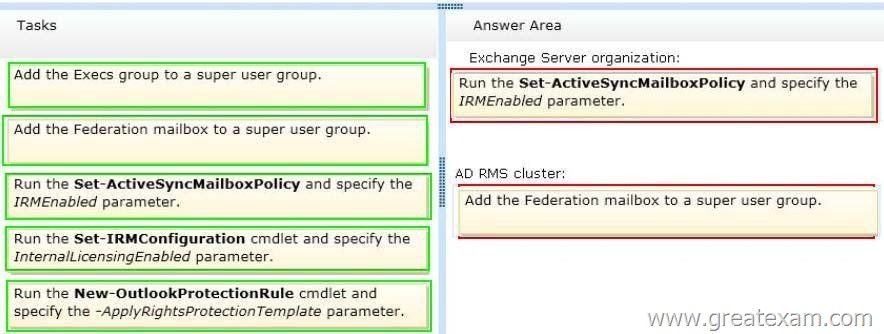
Explanation:
For the following Microsoft Exchange Server 2013 Information Rights Management (IRM) features to be enabled, you must add the Federation mailbox (a system mailbox created by Exchange 2013 Setup) to the super users group on your organization’s Active Directory Rights Management Services (AD RMS) cluster:
– IRM in Microsoft Office Outlook Web App
– IRM in Exchange ActiveSync
– Journal report decryption
– Transport decryption
The IrmEnabled parameter specifies whether Information Rights Management (IRM) is enabled for the mailbox policy.
QUESTION 67
Drag and Drop Question
Your company has two offices. Each office is configured as an Active Directory site.
The sites are named Site1 and Site2.
You have an Exchange Server 2013 organization that is configured as shown in the following exhibit. (Click the Exhibit button.)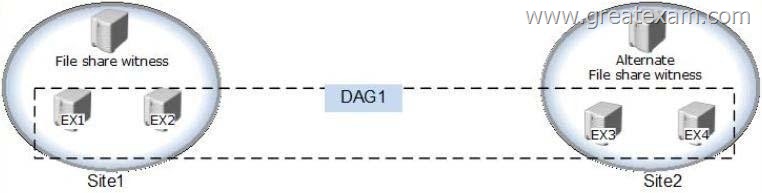
Datacenter Activation Coordination (DAC) mode is enabled on the database availability group (DAG) named DAG1.
You are testing a site failover by shutting down all of the servers in Site1.
You need to mount the databases in Site2.
Which three commands should you run in sequence? (To answer, move the appropriate three commands from the list of commands to the answer area and arrange them in the correct order.)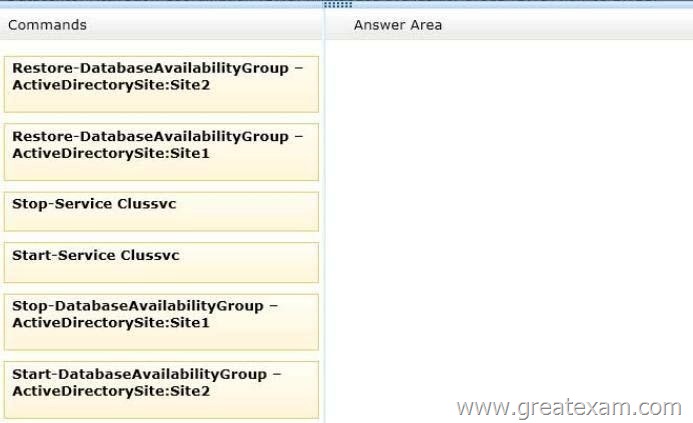
Answer: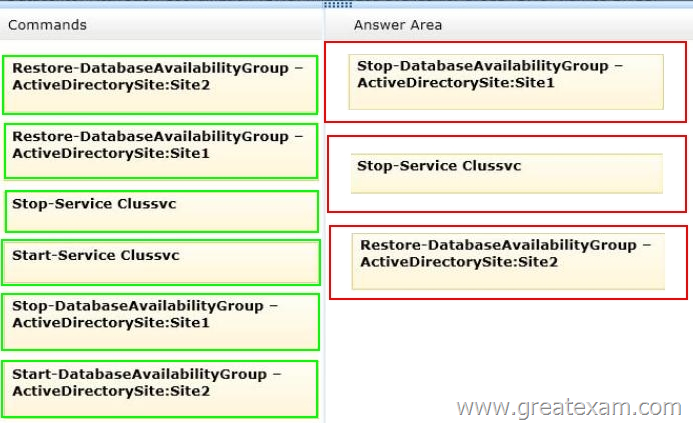
Explanation:
http://technet.microsoft.com/en-us/library/dd351049.aspx
QUESTION 68
Drag and Drop Question
You have an Exchange Server 2013 organization.
Your company identifies the following security requirements:
– Users must be able to send encrypted email messages that can only be decrypted by the intended recipient.
– All email messages sent by a user named User1 to an external recipient must be protected by using TLS.
– All SMTP sessions to a remote SMTP host named SMTP1 must be encrypted.
You need to recommend which technology must be used to meet each requirement.
Which technologies should you recommend? (To answer, drag the appropriate technologies to the requirements in the answer area. Each technology may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)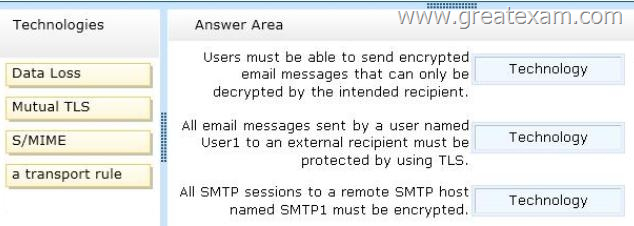
Answer: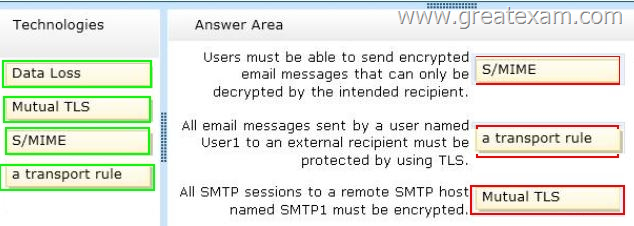
QUESTION 69
Hotspot Question
Your company has a main office and a disaster recovery site.
An Active Directory site named MainSite exists for the main office.
An Active Directory site named DRSite exists for the disaster recovery site.
The two sites connect to each other by using a WAN link. All users work in the main office.
You have an Exchange Server 2013 organization. The organization contains six servers.
The servers are configured as shown in the following table.
All of the Mailbox servers are members of a database availability group (DAG) named DAG1.
After a WAN link failure, you discover that all of the active mailbox database copies are located on MBX3, even though MBX1 and MBX2 are still running.
You need to prevent an automatic failover of DAG1 if the WAN link between the two sites fails but the servers in both sites are still running.
The solution must prevent two active copies of the same database.
What should you do? (To answer, select the appropriate options in the answer area.)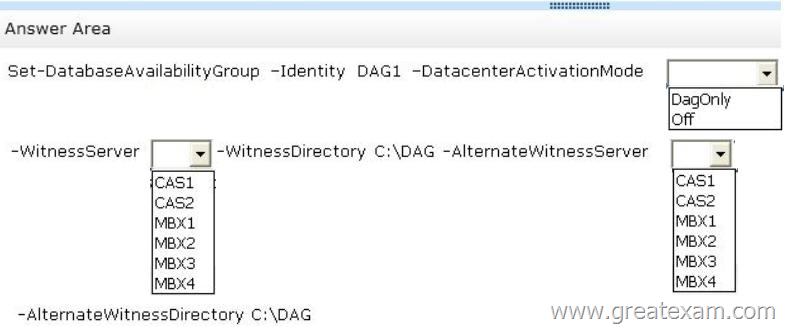
Answer: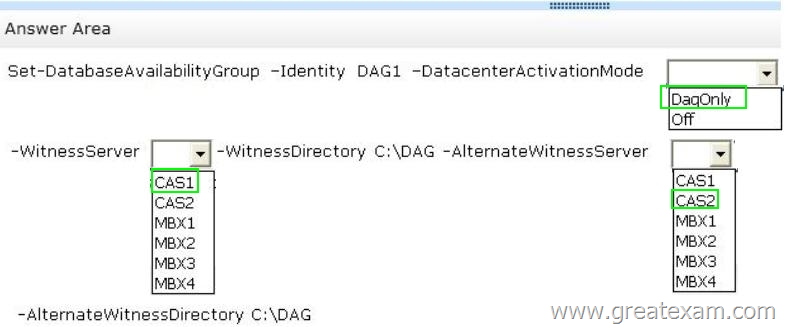
QUESTION 70
You have an Exchange Server 2010 organization that contains three servers.
The servers are configured as shown in the following table.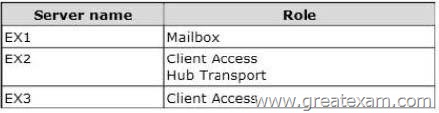
Microsoft Outlook is configured to connect to an FQDN of mail.adatum.com. Mail.adatum.com resolves to the IP address of a Layer 7 hardware load balancer.
The hardware load balancer is configured to send traffic to EX2 and EX3.
You deploy an Exchange Server 2013 Mailbox server and an Exchange Server 2013 Client Access server.
You plan to migrate all mailboxes to Exchange Server 2013.
You need to recommend a solution to ensure that users can access their mailbox on EX1 or EX4 during the migration.
What should you do?
A. Create a Client Access server array that contains EX1 and EX5.
B. Modify the autodiscover.contoso.com resource record to point to EX5.
C. Modify the properties of the hardware load balancer to point to EX5.
D. Create a DNS record named legacy.contoso.com in the internal DNS zone.
Answer: C
Explanation:
Note: So what is the Client Access server in Exchange 2013?
The Client Access server role is comprised of three components, client protocols, SMTP, and a UM Call Router. The CAS role is a thin, protocol session stateless server that is organized into a load balanced configuration. Unlike previous versions, session affinity is not required at the load balancer (but you still want a load balancer to handle connection management policies and health checking). This is because logic now exists in CAS to authenticate the request, and then route the request to the Mailbox server that hosts the active copy of the mailbox database.
The Mailbox server role now hosts all the components and/or protocols that process, render and store the data. No clients will ever connect directly to the Mailbox server role; all client connections are handled by the Client Access server role.
Reference: Exchange 2013 Server Role Architecture
We ensure our new version 70-342 PDF and VCE dumps are 100% valid for passing exam, because GreatExam is the top IT certification study training materials vendor. Many candidates have passed exam with the help of GreatExam’s VCE or PDF dumps. GreatExam will update the study materials timely to make them be consistent with the current exam. Download the free demo on GreatExam, you can pass the exam easily.