Are you looking for a Microsoft 70-341 exam questions? Are you looking for Microsoft 70-341 exam sample questions to identify gaps in your knowledge that may hurt you on the exam? GreatExam is your best choice! We are committed on providing you with the latest and most accurate 70-341 exam preparation material.
QUESTION 36
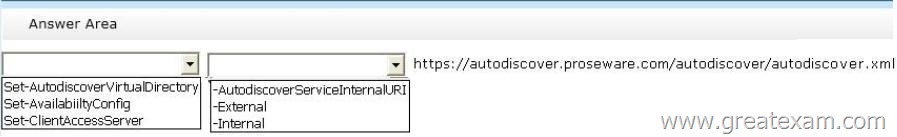
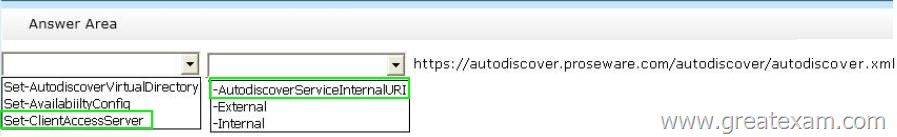
Hotspot Question
You need to recommend a solution to resolve the Autodiscover and the free/busy information issues.
Which command should you include in the recommendation? (To answer, configure the appropriate options in the answer area.)
QUESTION 37
You need to recommend a solution to resolve the issue of the human resources department manager.
What should you include in the recommendation?
A. Run Set-ADServerSettings -ConfigurationDomainController dcl.proseware.com on all of the Exchange servers in the London site.
B. Move the PDC emulator to the New York office.
C. Modify the replication interval on the Active Directory site link.
D. Schedule a task that runs the Update-AddressList command to run once per hour.
Answer: C
Explanation:
NOT A
Set-ADServerSettings
Use the Set-AdServerSettings cmdlet to manage the Active Directory Domain Services (AD DS) environment in the current Exchange Management Shell session.
The Set-AdServerSettings cmdlet replaces the AdminSessionADSettings session variable that was used in Microsoft Exchange Server 2007.
The ConfigurationDomainController parameter specifies the fully qualified domain name (FQDN) of the configuration domain controller to be used for reading Exchange configuration information in this session.
NOT B
Issue is related to AD Site replication
NOT D
Will not improve the site replication
You can use the Shell to update a global address list (GAL). A GAL is a directory that contains entries for every group, user, and contact within an organization’s implementation of Microsoft Exchange.
C
You must set the site link replication interval property to indicate how frequently you want replication to occur during the times when the schedule allows replication. For example, if the schedule allows replication between 02:00 hours and 04:00 hours, and the replication interval is set for 30 minutes, replication can occur up to four times during the scheduled time. The default replication interval is 180 minutes, or 3 hours.
Consider the following criteria to determine how often replication occurs within the schedule window:
A small interval decreases latency but increases the amount of WAN traffic.
To keep domain directory partitions up to date, low latency is preferred. http://technet.microsoft.com/en-us/library/cc738212(v=WS.10).aspx
QUESTION 38
You have an Exchange Server 2013 organization that contains two Client Access servers named SERVER1 and SERVER2 and two Mailbox servers named SERVER3 and SERVER4.
You have a firewall that controls all of the traffic between the internal network and the Internet. SERVER3 and SERVER4 are prevented from communicating with Internet hosts.
SERVER1 and SERVER3 are in a site named Main.
SERVER2 and SERVER4 are in a site named Main_2.
All outbound email is sent through SERVER1. Main fails.
You discover that email messages for the Internet are queued on SERVER4.
You create a new send connector in Main_2.
You discover that all of the outbound email is queued on SERVER4 and is not delivered to the Internet.
You verify that the client computers on the network can receive email messages from the Internet successfully.
You need to ensure that the email messages are delivered successfully to the Internet.
Which cmdlet should you run?
A. Set-SendConnector
B. Set-TransportService
C. Set-ExchangeServer
D. Set-ADSite
Answer: A
Explanation:
Mailbox Server
In an Exchange Server 2013 organization the Mailbox server role is responsible for sending outbound email via a Send Connector.
When this option is enabled outbound email that is being sent via a Send Connector does not go directly out from the Mailbox server, and instead is proxied through a Client Access server in the site. There is nothing complicated going on here, the Client Access server simply acts as a proxy for the connection so that the receiving host out on the internet sees the connection as coming from the Client Access server name and IP address rather than the Mailbox server.
IN THIS QUESTION THE CLIENT ACCESS SERVER (SERVER1) IS ACTING AS A PROXY SERVER FOR THE MAILBOX SERVERS.
NEED TO CHANGE THE SEND CONNECTOR SETTINGS IN ORDER FOR MAIL TO FLOW OUT FROM SERVER4 TO THE INTERNET.
Correct Answer A
Set-SendConnector
Use the Set-SendConnector cmdlet to modify a Send connector.
EXAMPLE 1
This example makes the following configuration changes to the Send connector named
Contoso.com Send
Connector:
Sets the maximum message size limit to 10 MB.
Changes the connection inactivity time-out to 15 minutes.
Set-SendConnector “Contoso.com Send Connector” -MaxMessageSize 10MB –
ConnectionInactivityTimeOut
00:15:00
Send Connector
In Microsoft Exchange Server 2013, a Send connector controls the flow of outbound messages to the receiving server.
They are configured on Mailbox servers running the Transport service. Most commonly, you configure a Send connector to send outbound email messages to a smart host or directly to their recipient, using DNS.
Exchange 2013 Mailbox servers running the Transport service require Send connectors to deliver messages to the next hop on the way to their destination.
Send connectors that are created on Mailbox servers are stored in Active Directory and are available to all Mailbox servers running the Transport service in the organization.
NOT B
Set-transportservice
Use the Set-TransportService cmdlet to set the transport configuration options for the Transport service on Mailbox servers or for Edge Transport servers. This example sets the
TransientFailureRetryCount parameter to 3 and sets the TransientFailureRetryInterval parameter to 30 seconds for the Transport service on a Mailbox server named Mailbox01.
Set-TransportService Mailbox01 -TransientFailureRetryCount 3 -TransientFailureRetryInterval
00:00:30
NOT C
Will not resolve the issue
Set-ExchangeServer
Use the Set-ExchangeServer cmdlet to set Exchange attributes in Active Directory for a specified server.
For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example disables error reporting on the specified server.
Set-ExchangeServer -Identity TestServer.Contoso.com -ErrorReportingEnabled: $false
NOT D
Will not resolve the issue
Set-ADSite
Use the Set-AdSite cmdlet to configure the Exchange settings of Active Directory sites.
EXAMPLE 1
This example configures the Active Directory site named Default-First-Site-Name as a hub site. Set-AdSite Default-First-Site-Name -HubSiteEnabled $true
http://technet.microsoft.com/en-us/library/aa998294(v=exchg.150).aspx
QUESTION 39
You have an Exchange Server 2013 organization named adatum.com.
The organization contains five Mailbox servers and two Client Access servers.
You need to ensure that an administrator named user1 receives a daily email message that contains a log of all the Exchange Server administrative actions.
Which cmdlet should you use in a scheduled task?
A. Search-AdminAuditLog
B. Set-Mailbox
C. New-AdminAuditLogSearch
D. Set-ExchangeServer
E. Set-AdminAuditLogConfig
Answer: C
Explanation:
NOT A
Use Search-AdminAuditLog for searching through the audit logs.
Search-AdminAuditLog
Use the Search-AdminAuditLog cmdlet to search the contents of the administrator audit log.
For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example finds all the administrator audit log entries that contain either the New-RoleGroup or the New-ManagementRoleAssignment cmdlet. Search-AdminAuditLog -Cmdlets New-RoleGroup, New-ManagementRoleAssignment
NOT B
Set-Mailbox
Use the Set-Mailbox cmdlet to modify the settings of an existing mailbox. You can use this cmdlet for one mailbox at a time.
To perform bulk management, you can pipeline the output of various Get-cmdlets (for example, the Get-Mailbox or Get-User cmdlets) and configure several mailboxes in a single-line command. You can also use the Set-Mailbox cmdlet in scripts.
For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example delivers John Woods’s email messages to John’s mailbox and also forwards them to Manuel Oliveira’s ([email protected]) mailbox.
Set-Mailbox -Identity John -DeliverToMailboxAndForward $true -ForwardingSMTPAddress [email protected]
NOT D
Set-ExchangeServer
Use the Set-ExchangeServer cmdlet to set Exchange attributes in Active Directory for a specified server.
For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example disables error reporting on the specified server.
Set-ExchangeServer -Identity TestServer.Contoso.com -ErrorReportingEnabled: $false
NOT E
NOT Set-AdminAuditLogConfig
Use the Set-AdminAuditLogConfig cmdlet to configure the administrator audit logging configuration settings.
EXAMPLE 1
This example enables administrator audit logging for every cmdlet and every parameter in the organization, with the exception of Get cmdlets.
Set-AdminAuditLogConfig -AdminAuditLogEnabled $true -AdminAuditLogCmdlets * -AdminAuditLogParameters *
C
New-AdminAuditLogSearch
Use the New-AdminAuditLogSearch cmdlet to search the contents of the administrator audit log and send the results to one or more mailboxes that you specify.
For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example finds all the administrator audit log entries that match the following criteria and sends the results to the [email protected] and [email protected] SMTP addresses:
Cmdlets Set-Mailbox Parameters UseDatabaseQuotaDefaults, ProhibitSendReceiveQuota, ProhibitSendQuota StartDate 01/24/2012 EndDate 02/12/2012
New-AdminAuditLogSearch -Name “Mailbox Quota Change Audit” -Cmdlets Set-Mailbox -Parameters
UseDatabaseQuotaDefaults, ProhibitSendReceiveQuota, ProhibitSendQuota -StartDate 01/24/2012 -EndDate
02/12/2012 -StatusMailRecipients [email protected], [email protected] New-AdminAuditLogSearch: Exchange 2013 Help
QUESTION 40
You have an Exchange Server 2013 organization.
You plan to deploy Exchange ActiveSync for mobile devices.
Each mobile device will be authenticated by using certificates issued by an internal certification authority (CA).
You need to configure the organization to authenticate the mobile devices by using the certificates.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From Internet Information Services (IIS) Manager on each Client Access server, configure the Microsoft-Server-ActiveSync virtual directory to require client certificates.
B. From Exchange Admin Center, configure the Microsoft-Server-ActiveSync virtual directory to require client certificates.
C. From Internet Information Services (IIS) Manager on each Client Access server, enable Active Directory Client Certificate Authentication.
D. From Internet Information Services (IIS) Manager on each Mailbox server, enable Active Directory Client Certificate Authentication.
Answer: BC
Explanation:
NOT A
Enable Active Directory Client Certificate Authentication within IIS but configure the Microsoft-Server-ActiveSync virtual directory to require client certificates is performed in Exchange Admin Center
NOT D
IIS is configured on the Client Access Server not the Mailbox Server
B
After you’ve installed the Exchange 2013 Client Access server, there are a variety of configuration tasks that you can perform.
Although the Client Access server in Exchange 2013 doesn’t handle processing for the client protocols, several settings need to be applied to the Client Access server, including virtual directory settings and certificate settings.
http://technet.microsoft.com/en-us/library/gg247612(v=exchg.150).aspx
Exchange Server 2013 automatically configures multiple Internet Information Services (IIS) virtual directories during installation.
This topic contains information about the default IIS authentication settings and default Secure Sockets Layer (SSL) settings for the Client Access and Mailbox servers.
The following table lists the default settings on a stand-alone Exchange 2013 Client Access server.
Default Client Access server IIS authentication and SSL settings
Virtual directory Authentication method SSL settings
Management method
Microsoft-Server-ActiveSync Basic authentication SSL required Requires 128-bit encryption
EAC or Shell
C
Configure certificate-based authentication for Exchange ActiveSync http://blogs.technet.com/b/exchange/archive/2012/11/28/configure-certificate-based-authentication-forexchange-
activesync.aspx
Client Access Server Configuration
To configure the Client Access server to enforce certificate based authentication :
1. Verify if Certificate Mapping Authentication is installed on the server. Right click on Computer in the start menu and choose Manage.
Expand Roles and click on Web Server (IIS)
Scroll down to the Role Services section. Under the Security section you should see Client Certificate Mapping
Authentication installed.
If you don’t see Client Certificate Mapping Authentication installed, click add Role Services
> (scroll) Security and select Client Certificate Mapping Authentication and then click Install.
Reboot your server.
QUESTION 41
You have an Exchange Server 2013 organization that contains two servers named EX1 and EX2. EX1 and EX2 are the members of a database availability group (DAG) named DAG1.
EX1 and EX2 each contain a copy of a mailbox database named DB1.
DB1 is configured to retain deleted items for 120 days.
At the end of each month, the mailbox databases on EX1 are backed up to tape.
The monthly backups are retained for two years.
A user named User1 has a mailbox in DB1.
User1 discovers that a mailbox folder that contained important email messages was deleted more than six months ago.
You need to recover the deleted mailbox folder without affecting any other users who have mailboxes in DB1.
Which three actions should you perform? (Each correct answer presents part of the solution.
Choose three.)
A. Run the New-MaiboxRestoreRequestcmdlet.
B. Run the New-MailboxDatabasecmdlet and specify the Recovery parameter.
C. Restore DB1 from the tape backup to an alternate location.
D. Restore DB1 from the tape backup to the database’s original location.
E. Run the New-Mailbox cmdlet and specify the Recovery parameter.
Answer: ABC
Explanation:
Recovery Database
A recovery database is a special kind of mailbox database that allows you to mount a restored mailbox database and extract data from the restored database as part of a recovery operation. You can use the New-MailboxRestoreRequest cmdlet to extract data from a recovery database. After extraction, the data can be exported to a folder or merged into an existing mailbox. Recovery databases enable you to recover data from a backup or copy of a database without disturbing user access to current data.
A
New-MaiboxRestoreRequestcmdlet
Use the New-MailboxRestoreRequest cmdlet to restore a soft-deleted or disconnected mailbox. This cmdlet starts the process of moving content from the soft-deleted mailbox, disabled mailbox, or any mailbox in a recovery database into a connected primary or archive mailbox.
For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
To create a restore request, you must provide the DisplayName, LegacyDN, or MailboxGUID for the softdeleted or disabled mailbox. This example uses the Get-MailboxStatistics cmdlet to return the DisplayName, LegacyDN, MailboxGUID, and DisconnectReason for all mailboxes on mailbox database MBD01 that have a disconnect reason of SoftDeleted or Disabled.
Get-MailboxStatistics -Database MBD01 | Where { $_.DisconnectReason -eq “SoftDeleted” -or $_.
DisconnectReason -eq “Disabled” } | Format-List LegacyDN, DisplayName, MailboxGUID, DisconnectReason
This example restores the source mailbox with the MailboxGUID 1d20855f-fd54-4681-98e6-e249f7326ddd on mailbox database MBD01 to the target mailbox with the alias Ayla. New-MailboxRestoreRequest -SourceDatabase “MBD01” -SourceStoreMailbox 1d20855f-fd54-4681-98e6-e249f7326ddd -TargetMailbox Ayla
B
Use the New-MailboxDatabase cmdlet to create a mailbox database object in the database container in Active Directory.
For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example creates the mailbox database MailboxDatabase01. This example also specifies where to create the .edb database file, which is different than the default location.
New-MailboxDatabase -Name “MailboxDatabase01” -EdbFilePath
D:\DatabaseFiles\MailboxDatabase01.edb
The Recovery parameter specifies that the new database is designated as a recovery database.
NOT D
Need to recover data from a backup or copy of a database without disturbing user access to current data.
Therefore restore to an alternate location.
NOT E
No recovery parameter exists for the New-Mailbox cmdlet.
Reference: Create a Recovery Database
Reference: Restore Data Using a Recovery Database
QUESTION 42
You have an Exchange Server 2010 organization.
All users connect to their mailbox by using Microsoft Outlook 2013 and Outlook Web App.
All client connections to Exchange Server use the name mail.contoso.com.
You deploy Exchange Server 2013 to the organization, you move all of the users to Exchange Server 2013, and then you decommission all of the Exchange Server 2010 servers.
The users report that when they open Outlook 2013, they receive a certificate warning message. The users do not receive a certificate error message or a certificate warning message when they open Outlook Web App.
You need to prevent the certificate warning message from occurring when the users open Outlook 2013.
Which cmdlet should you run?
A. Set-ClientAccessServer
B. New-ExchangeCertficiate
C. New-ClientAccessArray
D. Import-ExchangeCertificate
Answer: A
Explanation:
UNABLE TO ASSOCIATE SET-CLIENTACCESSSERVER WITH CERTIFICATE ERROR D LOOKS LIKE A BETTER RESPONSE.
IMPORT THE SSL CERTIFICATE AND THEN ASSIGN IT TO OUTLOOK 2013
Self-signed Certificate
When you install Exchange 2013, a self-signed certificate is automatically configured on the Mailbox servers. A self-signed certificate is signed by the application that created it. The subject and the name of the certificate match. The issuer and the subject are defined on the certificate. This self-signed certificate is used to encrypt communications between the Client Access server and the Mailbox server. The Client Access server trusts the self-signed certificate on the Mailbox server automatically, so no third-party certificate is needed on the Mailbox server. When you install Exchange 2013, a self-signed certificate is also created on the Client Access server.
This self-signed certificate will allow some client protocols to use SSL for their communications. Exchange ActiveSync and Outlook Web App can establish an SSL connection by using a self-signed certificate.
Outlook Anywhere won’t work with a self-signed certificate on the Client Access server. Self-signed certificates must be manually copied to the trusted root certificate store on the client computer or mobile device. When a client connects to a server over SSL and the server presents a self-signed certificate, the client will be prompted to verify that the certificate was issued by a trusted authority. The client must explicitly trust the issuing authority. If the client confirms the trust, then SSL communications can continue.
Note:
By default, the digital certificate installed on the Mailbox server or servers is a self-signed certificate. You don’t need to replace the self-signed certificate on the Mailbox servers in your organization with a trusted third-party certificate. The Client Access server automatically trusts the self-signed certificate on the Mailbox server and no other configuration is needed for certificates on the Mailbox server.
Outlook 2013
When connecting to an Exchange server using Outlook 2013 you may encounter an SSL trust error.
This error occurs when the Exchange server is configured with a self-signed SSL certificate.
Outlook makes connections to the Exchange server over HTTPS and therefore must trust the SSL certificate that is configured on the server, otherwise it will display those error messages to the end user.
To resolve the issue install a valid SSL certificate on the Exchange server from a trusted certificate authority.
See Exchange Server 2013 SSL certificates for more details on this as well as step by step instructions.
A
Set-ClientAccessServer
Use the Set-ClientAccessServer cmdlet to set properties on specified Client Access server objects.
For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example sets two properties on the Client Access server CAS-01.
Set-ClientAccessServer -Identity “CAS-01” -AutoDiscoverServiceInternalUri “https://cas01.contoso.com/autodiscover/autodiscover.xml” -AutoDiscoverSiteScope “Mail”
EXAMPLE 2
This example sets two properties on the Client Access server CASMail.
Set-ClientAccessServer -Identity “CASMail” -AutoDiscoverServiceInternalUri “https://casmail.contoso.com/autodiscover/autodiscover.xml” -AutoDiscoverSiteScope “Mail”
NOT B
New-ExchangeCertficiate
Not an Exchange 2013 command or any other Exchange version command
NOT C
Exchange 2010 command
Use the New-ClientAccessArray cmdlet to create an object that represents a load balanced array of Client Access servers within a single Active Directory site.
EXAMPLE 1
This example creates the Client Access server array server.contoso.com.
New-ClientAccessArray -Fqdn server.contoso.com -Site “Redmond” -Name
“server.contoso.com”
NOT D
Exchange 2013 command
Use the Import-ExchangeCertificate cmdlet to import a certificate or chain of certificates. For information about the parameter sets in the Syntax section below, see Syntax.
EXAMPLE 1
This example imports an existing certificate and private key from the PKCS #12 file ExportedCert.pfx.
Import-ExchangeCertificate -FileData ([Byte[]]$(Get-Content -Path
c:\certificates\ExportedCert.pfx -Encoding
byte -ReadCount 0)) -Password:(Get-Credential).password
QUESTION 43
Your network contains an Active Directory forest.
The forest contains two sites named Montreal and New York.
You have an Exchange Server 2013 organization that contains a Mailbox server and a Client Access server in each site.
The users in the New York site report that the offline address book (OAB) is not updated after an extended WAN outage between the sites.
The Montreal site contains the OAB generation server.
You need to ensure that the New York site users download the OAB from a server in the New York site.
Which two cmdlets should you run? (Each correct answer presents part of the solution. Choose two.)
A. Set-Mailbox
B. New-OfflineAddressBook
C. New-Mailbox
D. New-OabVirtualDirectory
E. Set-OfflineAddressBook
Answer: AC
Explanation:
A
Set-Mailbox
Use the Set-Mailbox cmdlet to modify the settings of an existing mailbox.
You can use this cmdlet for one mailbox at a time.
To perform bulk management, you can pipeline the output of various Get-cmdlets (for example, the Get-Mailbox or Get-User cmdlets) and configure several mailboxes in a single-line command. You can also use the Set-Mailbox cmdlet in scripts.
For information about the parameter sets in the Syntax section below, see Syntax.
Step2: Enable OABGen capability
Set-Mailbox -Arbitration oabs -OABGen $true
http://technet.microsoft.com/en-us/library/aa996345(v=exchg.150).aspx
Provision Recipients for Offline Address Book Downloads
To specify which OAB is downloaded by linking the OAB directly to a recipient’s mailbox, use the following syntax.
Set-Mailbox -Identity <MailboxIDParameter> -OfflineAddressBook <OfflineAddressBookIdParameter>
Better for this question (but the option is not covered:)
Use the Shell to specify the OAB that multiple recipients will download
This example specifies that all user mailboxes in the United States for Contoso will download the OAB Contoso United States.
Get-User -ResultSize Unlimited -Filter { Company -eq “Contoso” -and RecipientType -eq “UserMailbox” } | Where { $_.CountryOrRegion -eq “United States”} | Set-Mailbox -OfflineAddressBook “Contoso United States”
NOT B
New-OfflineAddressBook
Use the New-OfflineAddressBook cmdlet to create an offline address book (OAB).
EXAMPLE 1
This example uses two commands to create the OAB named OAB_AgencyB that includes all address lists where AgencyB is part of the name. With the settings shown, an OAB is generated by myserver.contoso.com on Mondays and Wednesdays from 01:00 (1:00 A.M.) to 02:00 (2:00 A.M.). The command also creates the default OAB for the organization.
$a = Get-AddressList | Where {$_.Name -Like “*AgencyB*”
New-OfflineAddressBook -Name “OAB_AgencyB” -Server myserver.contoso.com -AddressLists $a -Schedule “Mon.01:00-Mon.02:00, Wed.01:00-Wed.02:00”
C
New-Mailbox
Use the New-Mailbox cmdlet to create a user in Active Directory and mailbox-enable this new user.
Step1: Create a new arbitration mailbox
New-Mailbox -Arbitration -Name “OAB New York” -Database DB2NewYork -UserPrincipalName [email protected] –DisplayName “OAB Mailbox for New York”
EXAMPLE 1
This example creates a user Chris Ashton in Active Directory and creates a mailbox for the user. The mailbox is located on Mailbox Database 1. The password must be reset at the next logon. To set the initial value of the password, this example creates a variable ($password), prompts you to enter a password, and assigns that password to the variable as a SecureString object.
$password = Read-Host “Enter password” -AsSecureString
New-Mailbox -UserPrincipalName [email protected] -Alias chris -Database “Mailbox Database 1” -Name ChrisAshton -OrganizationalUnit Users -Password $password -FirstName Chris -LastName Ashton -DisplayName “Chris Ashton” -ResetPasswordOnNextLogon $true
NOT D
New-OabVirtualDirectory
Use the New-OABVirtualDirectory cmdlet to configure a server as a web distribution point for an offline address book (OAB).
EXAMPLE 1
This example creates an OAB virtual directory on CASServer01 and configures the distribution service to poll the generation server every two hours.
New-OABVirtualDirectory -Server CASServer01 -PollInterval 120
NOT E
Set-OfflineAddressBook
Use the Set-OfflineAddressBook cmdlet to modify offline address book (OAB) settings.
EXAMPLE 1
This example changes the name of the OAB.
Set-OfflineAddressBook -Identity “\Default Offline Address Book” -Name “My Offline Address Book”
QUESTION 44
Your network contains an Active Directory forest.
The forest contains one domain.
The domain contains two sites and three domain controllers.
The sites and domain controllers are configured as shown in the following table.
The sites connect to each other by using a WAN link.
You have an Exchange Server 2013 organization that contains two servers in the Main Office site.
In Branch1, you plan to deploy one server to the Exchange Server 2013 organization.
You need to ensure that all of the Exchange Server services in Branch1 are available if the WAN link fails after the planned deployment.
What should you do?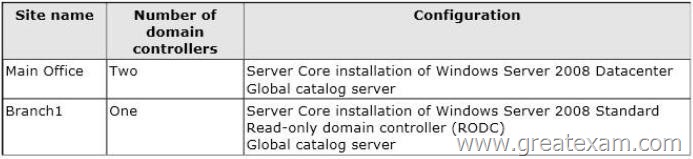
A. Create a site link bridge, and then configure Branch1 as a hub site.
B. Replace the domain controller in Branch1 with an RODC that runs Windows Server 2012.
C. Replace the domain controller in Branch1 with a writable domain controller that runs a Server Core installation of Windows Server 2008.
D. Create an additional site link, and then configure Branch1 as a hub site.
Answer: C
Explanation:
Site link bridge
A site link bridge connects two or more site links and enables transitivity between site links.
Each site link in a bridge must have a site in common with another site link in the bridge.
The Knowledge Consistency Checker (KCC) uses the information on each site link to compute the cost of replication between sites in one site link and sites in the other site links of the bridge.
Without the presence of a common site between site links, the KCC also cannot establish direct connections between domain controllers in the sites that are connected by the same site link bridge.
By default, all site links are transitive.
This figure illustrates an organization’s hub-and-spoke network topology, consisting of two hub sites (A and B) and six satellite sites (C through H).
The site links between all sites are named A-B, A-C, A-D, A-E, B-F, B-G, and B-H.
Hub Site
A hub site is based on having large numbers of outgoing links
NOT A B D
If you want to install or operate any Exchange 2013 server in a site, you must have a writable global catalog in the same AD site.
Be aware that no versions of Exchange Server will make use of RODC or the Global Catalog server on a RODC although Exchange will work in the presence of RODC as long as writable versions of domain controllers and GCs are available
C
If you want to install or operate any Exchange 2013 server in a site, you must have a writable global catalog in the same AD site.
The Global Catalog is the central repository of information about objects in a tree or forest but with a limited number of each objects attribute.
The domain controller that holds a copy of the Global Catalog is the Global Catalog Server. The global catalog server makes it possible to search the entire AD DS forest without referrals to the domain controller that stores the target of the search.
The global catalog server is also required for searching and processing domain logons in forests where universal groups is available Be aware that no versions of Exchange Server will make use of RODC or the Global Catalog server on a RODC although Exchange will work in the presence of RODC as long as writable versions of domain controllers and GCs are available
QUESTION 45
Your company has a main office site and a disaster recovery site.
The two sites connect to each other by using redundant WAN links.
Each site connects directly to the Internet. Each site contains one Exchange Server 2013 server that is accessible from the Internet.
The company uses the ©ontoso.com email address suffix.
The DNS records that can be resolved from the Internet are configured as shown in the following table.
When the Internet link at the main office site fails, the company cannot receive incoming email from the Internet.
You need to ensure that incoming email from the Internet is delivered to Server1.
Incoming email from the Internet must be delivered to Server2 if Server1 is unavailable.
What should you create?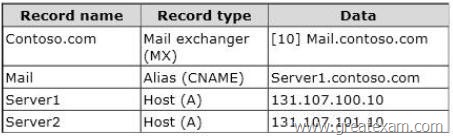
A. A CNAME record for the name mail.contoso.com that resolves to server2.contoso.com
B. An MX record that has a cost of 20 and resolves to mail.contoso.com
C. An MX record that has a cost of 20 and resolves to server2.contoso.com
D. An A record for the name mail.contoso.com that resolves to 131.107.101.1
Answer: C
Explanation:
CNAME record
A CNAME record is an abbreviation for Canonical Name record and is a type of resource record in the Domain Name System (DNS) that specifies that the domain name is an alias of another, canonical domain name. Here “canonical” usually means: a more generally accepted or standard name.
For example, if there is a DNS zone as follows:
NAME TYPE VALUE
————————————————–
bar.example.com. CNAME foo.example.com.
foo.example.com. A 192.0.2.23
MX record
A mail exchanger record (MX record) is a type of resource record in the Domain Name System that specifies a mail server responsible for accepting email messages on behalf of a recipient’s domain, and a preference value used to prioritize mail delivery if multiple mail servers are available. The set of MX records of a domain name specifies how email should be routed with the Simple Mail Transfer Protocol (SMTP).
A Record
An A (address) record is a DNS record that can be used to point your domain name and host names to a static IP address.
NOT A B D
Need to increase the cost associated with the MX record of Server2 so that Server1 is preferred over Server2 but Server2 will be used if Server1 is not available.
C
Need to increase the cost associated with the MX record of Server2 so that Server1 is preferred over Server2 but Server2 will be used if Server1 is not available. There is already a CNAME (Alias) associated with mail.contoso.com which points to Server1.contoso.com
Record Name Record Type Data
Contoso.com Mail Exchanger (MX) [20] mail2.contoso.com
Mail2 Alias CNAME Server2.contoso.com
QUESTION 46
Drag and Drop Question
You have an Exchange Server 2013 organization named adatum.com.
The organization contains a server named Server1.
Server1 is a member of a Database Availability Group (DAG) named DAG1.
You have a user named Sales1 in the Sales department.
You need to prevent Sales1 from submitting more than 75 email messages per minute to the Exchange Server organization by using Microsoft Outlook.
Which three commands should you run in sequence? (To answer, move the appropriate three commands from the list of commands to the answer area and arrange them in the correct order.)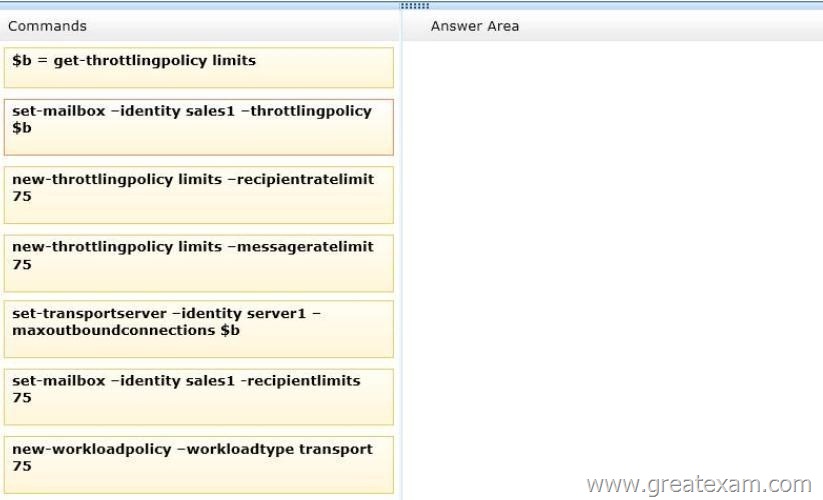
Answer: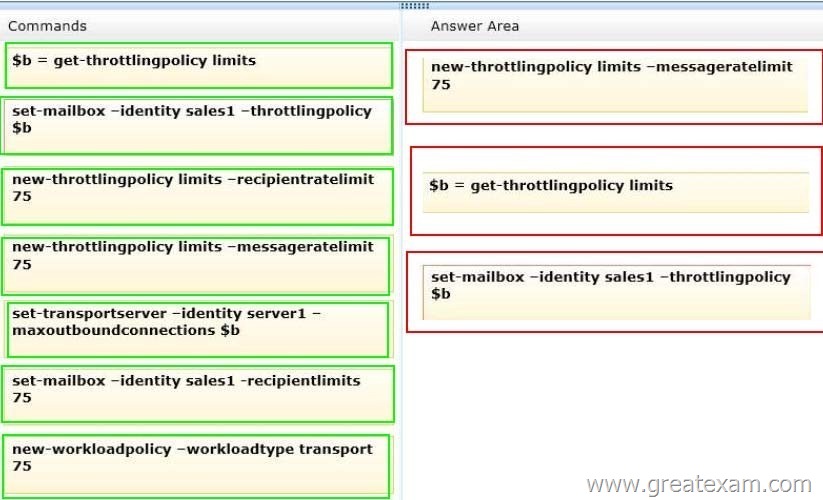
QUESTION 47
Drag and Drop Question
You have an Exchange Server organization that contains three servers.
The servers are configured as shown in the following table.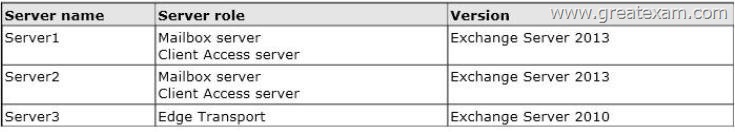
You need to create a new database availability group (DAG) that contains EX1 and EX2.
Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)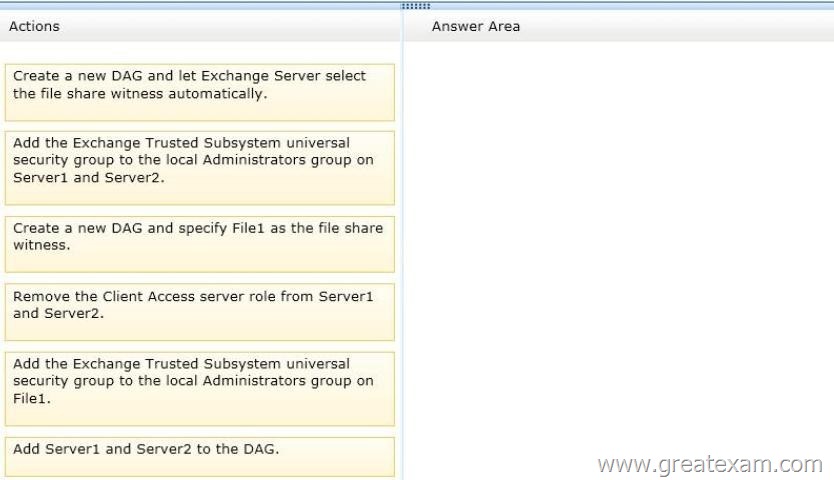
Answer: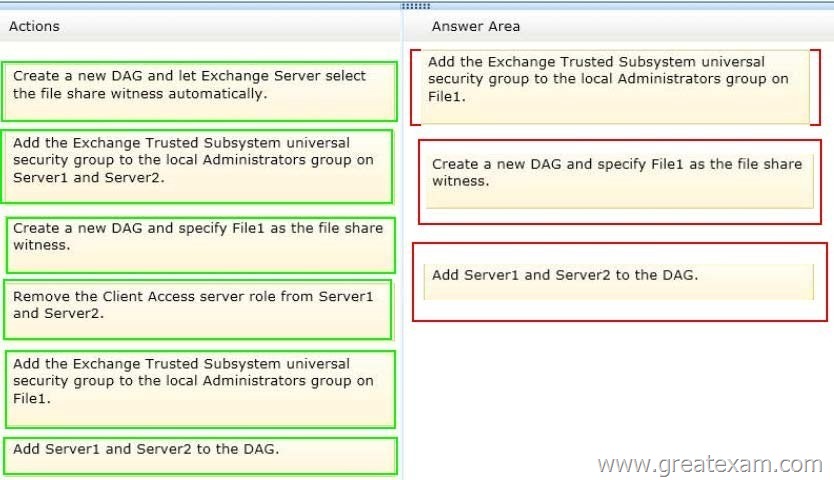
Explanation:
Box 1: Add the Exchange Trusted Subsystem universal security group to the local Administrators group on Server1.
Box 2: Create a new DAG and specify Server1 as the file share witness.
Box 3: Add EX1 and EX2 to the DAG.
Note:
– A database availability group (DAG) is a set of up to 16 Microsoft Exchange Server 2013 Mailbox servers that provide automatic database-level recovery from a database, server, or network failure. When a Mailbox server is added to a DAG, it works with the other servers in the DAG to provide automatic, database-level recovery from database, server, and network failures.
– You can specify a name for the DAG and the witness server that you want to use, and leave the Witness directory field empty. In this scenario, the task will create the default witness directory on the specified witness server.
– If the witness server you specify isn’t an Exchange 2013 or Exchange 2010 server, you must add the Exchange Trusted Subsystem universal security group to the local Administrators group on the witness server. These security permissions are necessary to ensure that Exchange can create a directory and share on the witness server as needed.
Reference: Exchange 2013, Create a Database Availability Group
QUESTION 48
You have an Exchange Server 2013 organization that contains two Mailbox servers named MBX1 and MBX2.
You create a database availability group (DAG) named DAG1. DAG1 is configured as shown in the exhibit.
You need to ensure that replication only occurs over the replication network.
Which two commands should you run? (Each correct answer presents part of the solution. Choose two.)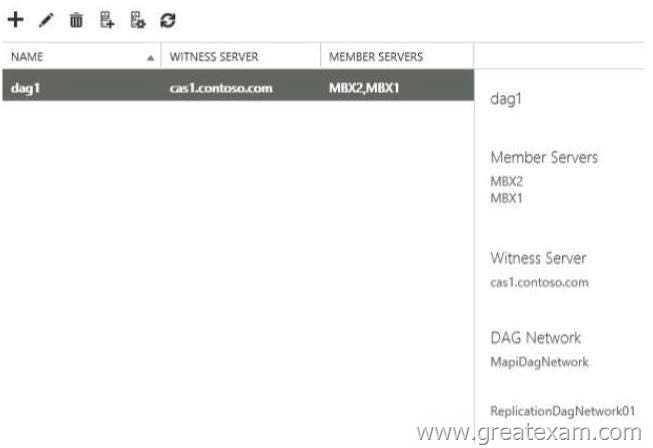
A. Set-DatabaseAvailabilityGroupNetwork ReplicationDagNetwork01 -ReplicationEnabled $true
B. Set-DatabaseAvailabilityGroupNetworkMapiDagNetwork -ReplicationEnabled $false
C. Set-DatabaseAvailabilityGroup Dag1 -ManualDagNetworkConfiguration $true
D. Set-DatabaseAvailabilityGroup Dag1 -ManualDagNetworkConfiguration $false
Answer: BC
Explanation:
You need to ensure that replication only occurs over the replication network.
If you would like to ‘force’ replication to only go over the Replication Network, then you definately would like to disable replication on the MAPI Network, but IF the NIC on the Replication Network goes down, it will start replicating over the MAPI NIC.
There is no way of blocking that behaviour and isn’t what you’d want anyway since DAGs actually cope quite fine with just 1 NIC.
DAG Networks
Each database availability group (DAG) network has several properties that you can configure, including the name of the DAG network, a description field for the DAG network, a list of subnets that are used by the DAG network, and whether the DAG network is enabled for replication.
You can configure a DAG network only when automatic network configuration has been disabled for a DAG.
There are specific networking requirements that must be met for each DAG and for each DAG member.
Each DAG must have a single MAPI network, which is used by a DAG member to communicate with other servers (for example, other Exchange 2013 servers or directory servers), and zero or more Replication networks, which are networks dedicated to log shipping and seeding.
Although a single network is supported, we recommend that each DAG have at least two networks: a single MAPI network and a single Replication network. This provides redundancy for the network and the network path, and enables the system to distinguish between a server failure and a network failure. Using a single network adapter prevents the system from distinguishing between these two types of failures.
MAPI
MAPI stands for Messaging Application Programming Interface, and it gives programs the ability to send email using your email program to do the actual sending.
Set-DatabaseAvailabilityGroup
The Set-DatabaseAvailabilityGroup cmdlet enables you to manage DAG properties that can’t be managed from the Exchange Administration Center (EAC), such as configuring network discovery, selecting the TCP port used for replication, and enabling datacenter activation coordination (DAC) mode.
Set-DatabaseAvailabilityGroupNetwork
Use the Set-DatabaseAvailabilityGroupNetwork cmdlet to configure a network for a database availability group (DAG).
You can configure a variety of network properties, such as the name for the network, a description of the network, a list of one or more subnets that comprise the network, and whether the network is enabled for replication (log shipping and seeding).
You need to be assigned permissions before you can run this cmdlet. Although all parameters for this cmdlet are listed in this topic, you may not have access to some parameters if they’re not included in the permissions assigned to you.
C
Ensures that you can configure a DAG network by turning the automatic configuration off.
The ManualDagNetworkConfiguration parameter
Specifies whether DAG networks should be automatically configured. If this parameter is set to False, DAG networks are automatically configured. If this parameter is set to True, you must manually configure DAG networks.
You can configure a DAG network only when automatic network configuration has been disabled for a DAG.
Need to manually configure the DAG NETWORK
NOT D
Need to turn the automatic DAG configuration off.
The ManualDagNetworkConfiguration parameter Specifies whether DAG networks should be automatically configured. If this parameter is set to False, DAG networks are automatically configured. If this parameter is set to True, you must manually configure DAG networks.
You can configure a DAG network only when automatic network configuration has been disabled for a DAG.
NOT A
Does not disable the replication over the MAPI network as required in this scenario
B
Disables replication over the MAPI network as required in this scenario
QUESTION 49
You have an Exchange Server 2013 organization that contains a server named Server1.
Server1 has an IP address of 10.1.100.16 and is configured to use a default gateway of 10.1.100.1.
You deploy a hardware load balancer that is configured to use the IP addresses of 192.168.101.31 and 10.1.100.31.
A user named User1 has a client computer that has an IP address of 102.168.101.201.
User1 reports that he cannot view his mailbox by using Outlook Web App.
When you review the IIS logs on Server1, you discover the following information:
You need to ensure that User1 can access his mailbox successfully from Outlook Web App.
What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.)
A. Configure the hardware load balancer to use the same certificate as the certificate used on Server1.
B. Configure the hardware load balancer to use source NAT (SNAT).
C. Configure the computer of User1 to ignore response headers.
D. Modify the default gateway of Server1.
Answer: BD
Explanation:
Source NAT
When using source NAT, the client IP address is not passed to the load balanced server.
The insertion of the Client IP address into the header allows the servers to see the IP that made the connection
They are then able to return the requested information correctly
B
Configuring the hardware load balancer to use source NAT (SNAT) will resolve the problem.
D
Changing the default gateway of Server1 to that of the hardware load balancer will ensure that the connection to Server1 will be returned via the network load balancer and out to User1
NOT A
Not a certificate problem
NOT C
NOT a http response header issue
HTTP response header
The information, in the form of a text record, that a Web server sends back to a client–s browser in response to receiving an HTTP request.
The response header contains the date, size and type of file that the server is sending back to the client and also data about the server itself.
The header is attached to the files being sent back to the client.
QUESTION 50
You have an Exchange Server 2013 organization that is configured to filter email messages for spam and malware.
You need to modify the schedule for applying updates to the anti-spam and the antimalware definitions.
Which command should you run?
A. Update-MalwareFilteringServer.ps1
B. Set-MalwareFilteringServer
C. Set-SenderFilterConfig
D. Update-SafeList
Answer: B
Explanation:
NOT A
Microsoft Exchange Server 2013 administrators can manually download anti-malware engine and definition (signature) updates.
Update-MalwareFilteringServer.ps1 used in manual updates not schedule updates.
NOT C
Not used for spam and malware updates.
Use the Set-SenderFilterConfig cmdlet to modify the Sender Filter agent configuration.
EXAMPLE 1
This example makes the following modifications to the Sender Filter agent configuration:
It enables blocking of blank senders.
It blocks messages from lucernepublishing.com and all subdomains. It adds [email protected] and [email protected] to the blocked senders list without affecting any existing entries.
Set-SenderFilterConfig -BlankSenderBlockingEnabled $true –
BlockedDomainsAndSubdomains
lucernepublishing.com -BlockedSenders
@{Add=”[email protected]”,”[email protected]”}
NOT D
Use the Update-SafeList cmdlet to update the safelist aggregation data in Active Directory.
Safelist aggregation data is used in the built-in anti-spam filtering in Microsoft Exchange.
EdgeSync replicates
safelist aggregation data to Edge Transport servers in the perimeter network.
EXAMPLE 1
This example updates Safe Senders List data for the single user [email protected].
Update-Safelist [email protected]
B
Set-MalwareFilteringServer
Use the Set-MalwareFilteringServer cmdlet to configure the Malware agent settings in the Transport service on a Mailbox server.
Example 1
This example sets the following Malware agent settings on the Mailbox server named Mailbox01:
Sets the update frequency interval to 2 hours
Sets the time to wait between resubmit attempts to 10 minutes
Set-MalwareFilteringServer Mailbox01 -UpdateFrequency 120 -DeferWaitTime 10
Our 70-341 dumps are rich in variety. We offer 70-341 PDF dumps, 70-341 practice test and 70-341 VCE dumps. We ensure you can pass the 70-341 easily. Welcome to GreatExam.com.