Are you worring about the 70-410 exam? With the complete collection of 70-410 exam questions and answers, GreatExam has assembled to take you through your 70-410 exam preparation. Each Q & A set will test your existing knowledge of 70-410 fundamentals, and offer you the latest training products that guarantee you passing 70-410 exam easily.
QUESTION 371
A company’s server deployment team needs to install fourteen Windows Server 2012 R2 to handle the expected increase in holiday traffic. The team would like the option of switching the servers between Server Core and Full GUI servers and do not want to be locked in to their first choice.
The server team would like four of the servers to include the Windows 8 Shell. Which installation option is required for these servers?
A. Server Core
B. Desktop Experience
C. Server with a GUI
D. Minimal Server Interface
Answer: B
Explanation:
The Desktop Experience installation option includes the Windows 8 Shell feature. This installation option also includes other features available for installation not found in the other three; such as Themes, Windows Store and support for Windows Store apps, and Windows Media Player.
Quick Tip: To completely remove a feature and the binary files from the disk, use the Windows PowerShell command Uninstall-WindowsFeature. For example, to remove Desktop Experience:
Uninstall-WindowsFeature Desktop-Experience -Remove
http://technet.microsoft.com/en-us/library/hh831786.aspx
http://mcpmag.com/articles/2013/01/22/70-410-win2012-install.aspx
QUESTION 372
A company’s network administrator needs to ensure a specific IP address is never assigned by a Windows Server 2012 R2 DHCP server to any device connecting to the network.
Which of the following should the administrator configure on the Windows Server 2012 R2 DHCP server?
A. Reservation
B. Scope options
C. NAP
D. Scope properties
Answer: A
Explanation:
Configuring an IP address as a reservation will restrict a DHCP server’s assignment of that address unless a specific MAC address makes a request for the address.
Exclusion is for not use the IP Address or range inside the Scope Pool, Filter is for not use theMAC Address or range.
Quick Tip: Policies can also be defined per scope or server. Policy based assignment (PBA) allows an administrator to group DHCP clients by specific attributes based on fields contained in the DHCP client request packet. This feature allows for targeted administration and greater control of configuration parameters delivered to network devices.
http://technet.microsoft.com/en-us/library/jj200226.aspx
http://mcpmag.com/articles/2013/02/12/70-410-dhcp.aspx
Another correct answer? Create a Exclusion Range? You decide… but that option is not at the options list at this question.
QUESTION 373
A company’s server virtualization team needs to provision a series of Hyper-V workloads to use existing network storage arrays. The team has chosen to use Fibre Channel ports within the guest operating systems.
Which of the following Windows Server versions can be used as guest operating systems when using Hyper-V Fibre Channel ports?
A. 2003 R2
B. 2008
C. 2003
D. 2012
Answer: BD
Explanation:
Windows Server 2008, 2008 R2, and 2012 R2 can be guest operating systems when using Hyper-V Fibre Channel host bus adaptors (HBAs). Updated HBA drivers are needed along with NPIV-enabled (N_Port ID Virtualization) SANs.
Quick Tip: Virtual Fibre Channel logical units cannot be used as boot media.
http://technet.microsoft.com/en-us/library/hh831413.aspx
http://mcpmag.com/articles/2013/02/05/70-410-win2012-fibre.aspx
QUESTION 374
A company’s server deployment team needs to introduce many new Windows Server 2012 R2 domain controllers throughout the network into a single Windows Server 2008 R2 domain.
The team has chosen to use Windows PowerShell.
Which Windows PowerShell module includes the command-line options for installing domain controllers?
A. AD DS Administration cmdlets
B. AD DS Deployment cmdlets
C. AD CS Deployment cmdlets
D. AD DS Administration cmdlets
Answer: B
Explanation:
First use the Import-Module ADDSDeployment command in PowerShell–it includes the cmdlets needed to add new domain controllers. Then run Install-ADDSDomainController along with the required arguments.
Quick Tip: DCPromo.exe has been deprecated but can still be used along with an answer file, and ADPrep.exe runs automatically when needed (but can be run with elevated rights for more control).
http://technet.microsoft.com/en-us/library/hh994618.aspx
http://mcpmag.com/articles/2013/02/19/70-410-win2012-ad.aspx
QUESTION 375
A company’s server administration team would like to take advantage of the newest file systems available with Windows Server 2012 R2. The team needs a file system capable of managing extremely large data drives that can auto-detect data corruption and automatically perform needed repairs without taking a volume offline.
Which file system should the server administration team choose?
A. NFS
B. DFS
C. NTFS
D. ReFS
Answer: D
Explanation:
The ReFS (Resilient File System) is capable of managing extremely large data drives (1 YB Yottabyte), can auto-detect data corruption, and automatically perform needed repairs without taking the volume offline.
Quick Tip: The command fsutil fsinfo volumeinfo x: will display the volume file system. ReFS is only intended for data drives and not compatible with all Windows Server 2012 R2 file system technologies, however it is compatible with the new Storage Spaces.
http://technet.microsoft.com/en-us/library/hh831724.aspx
http://mcpmag.com/articles/2013/01/29/70-410-win2012-file.aspx
QUESTION 376
A company’s server security team needs a solution that will prevent users from installing and using unauthorized applications on their Windows 8 desktop computers.
Which technology should the team choose?
A. Starter GPOs
B. Group Policy Objects
C. Software Restriction Policies
D. AppLocker
Answer: D
Explanation:
AppLocker (Application Locker) can help prevent malicious (malware) and unsupported applications from affecting computers. These include executable files, scripts, Windows Installer files, DLLs, Packaged apps and Packaged app installers.
Quick Tip: AppLocker is also supported by Windows Server 2008 R2 and Windows 7.
http://technet.microsoft.com/en-us/library/hh831440.aspx
http://mcpmag.com/articles/2013/02/26/controlling-applications.aspx ExamRef
QUESTION 376
You are attempting to delete a global security group in the Active Directory Users and Computers console, and the console will not let you complete the task. Which of the following could possibly be causes for the failure? (Choose all answers that are correct.)
A. There are still members in the group.
B. One of the group’s members has the group set as its primary group.
C. You do not have the proper permissions for the container in which the group is located.
D. You cannot delete global groups from the Active Directory Users and Computers console.
Answer: BC
Explanation:
A. Incorrect: It is possible to delete a group that has members.
B. Correct: If any member sets the group as its primary group, then the system does not permit the group to be deleted.
C. Correct: You must have the appropriate Active Directory permissions for the container in which the group is located to delete it.
D. Incorrect: It is possible to delete groups using the Active Directory Users and Groups console.
QUESTION 377
In a domain running at the Windows Server 2012 R2 domain functional level, which of the following security principals can members of a global group? (Choose all answers that are correct.)
A. Users
B. Computers
C. Universal groups
D. Global groups
Answer: ABD
Explanation:
A. Correct: Users can be security principals in a global group.
B. Correct: Computers can be security principals in a global group.
C. Incorrect: Universal groups cannot be security principals in a global group.
D. Correct: Global group can be security principals in a global group.
QUESTION 378
Which of the following group scope modifications are never permitted? (Choose all answers that are correct.)
A. Global to universal
B. Global to domain local
C. Universal to global
D. Domain local to universal
Answer: B
Explanation:
A. Incorrect: Global to universal group conversions are sometimes permitted.
B. Correct: Global to domain local group conversions are never permitted.
C. Incorrect: Universal to global group conversions are sometimes permitted.
D. Incorrect: Domain local to universal group conversions are sometimes permitted.
QUESTION 379
Which of the following is not a correct reason for creating an OU?
A. To create a permanent container that cannot be moved or renamed
B. To duplicate the divisions in your organization
C. To delegate administration tasks
D. To assign different Group Policy settings to a specific group of users or computers
Answer: A
Explanation:
A. Correct: The reasons for creating an OU include duplicating organizational divisions, assigning Group Policy settings, and delegating administration. You can easily move or rename an OU at will.
B. Incorrect: Duplicating organizational divisions is a viable reason for creating an OU.
C. Incorrect: Delegating administration tasks is a viable reason for creating an OU.
D. Incorrect: Assigning Group Policy settings is a viable reason for creating an OU.
QUESTION 380
Which of the following groups do you use to consolidate groups and accounts that either span multiple domains or the entire forest?
A. Global
B. Domain local
C. Built-in
D. Universal
Answer: D
Explanation:
A. Incorrect: Global groups cannot contain users from other domains.
B. Incorrect: Domain local groups cannot have permissions for resources in other domains.
C. Incorrect: Built-in groups have no inherent cross-domain qualities.
D. Correct: Universal groups, like global groups, are used to organize users according to their resource access needs. You can use them to organize users to facilitate access to any resource located in any domain in the forest through the use of domain local groups. Universal groups are used to consolidate groups and accounts that either span multiple domains or the entire forest.
QUESTION 381
Which of the following are the two built-in user accounts created automatically on a computer running Windows Server 2012 R2?
A. Network
B. Interactive
C. Administrator
D. Guest
Answer: CD
Explanation:
A. Incorrect: There is no Network account in Windows Server 2012 R2.
B. Incorrect: There is no Interactive account in Windows Server 2012 R2.
C. Correct: By default, the two built-in user accounts created on a computer running Windows Server 2012 are the Administrator account and the Guest account.
D. Correct: By default, the two built-in user accounts created on a computer running Windows Server 2012 are the Administrator account and the Guest account.
QUESTION 382
Which of the following is not a type of user account that can be configured in Windows Server 2012 R2?
A. local accounts
B. domain accounts
C. network accounts
D. built-in accounts
Answer: C
Explanation:
A. Incorrect: Local accounts can be created and configured in Windows Server 2012 R2.
B. Incorrect: Domain accounts can be created and configured in Windows Server 2012 R2.
C. Correct: Three types of user accounts can be created and configured in Windows Server 2012: local accounts, domain accounts, and built-in user accounts.
D. Incorrect: Built-in accounts can be created and configured in Windows Server 2012 R2.
QUESTION 383
Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2. Server1 and Server2 are part of a workgroup.
On Server1 and Server2, you create a local user account named Admin1. You add the account to the local Administrators group. On both servers, Admin1 has the same password.
You log on to Server1 as Admin1. You open Computer Management and you connect to Server2.
When you attempt to create a scheduled task, view the event logs, and manage the shared folders, you receive Access Denied messages.
You need to ensure that you can administer Server2 remotely from Server1 by using Computer Management.
What should you configure on Server2?
A. From Registry Editor, configure the LocalAccountTokenFilterPolicy registry value.
B. From Local Users and Groups, modify the membership of the Remote Management Users group.
C. From Server Manager, modify the Remote Management setting.
D. From Windows Firewall, modify the Windows Management Instrumentation (WMI) firewall rule.
Answer: A
Explanation:
The LocalAccountTokenFilterPolicy setting affects how administrator credentials are applied to remotely administer the computer.
http://support.microsoft.com/kb/942817
QUESTION 384
Your network contains an Active Directory domain named adatum.com.
The domain contains a server named Server1 that runs Windows Server 2012 R2.
On a server named Corel, you perform a Server Core Installation of Windows Server 2012 R2.
You join Corel to the adatum.com domain.
You need to ensure that you can use Event Viewer on Server1 to view the event logs on Core1.
What should you do on Core1?
A. Run the Disable NetFirewallRule cmdlet.
B. Install Remote Server Administration Tools (RSAT).
C. Install Windows Management Framework.
D. Enable NetFirewallRule cmdlet.
Answer: D
Explanation:
Information regarding IPsec policy changes, etc. can be found in the Event Viewer. Thus you need to enable the NetFirewallRule command. This will allow you to view the event logs.
QUESTION 385
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 runs Windows Server 2012 R2 and has the Hyper-V server role installed.
On Server1, you create and start a virtual machine named VM1.
VM1 is configured as shown in the following table.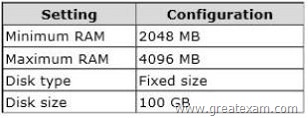
You need to recommend a solution to minimize the amount of disk space used for the snapshot of VM1.
What should you do before you create the snapshot?
A. Run the Stop-VM cmdlet.
B. Decrease the Minimum RAM.
C. Run the Convert-VHD cmdlet.
D. Convert diskl.vhd to a dynamically expanding disk.
Answer: A
Explanation:
Original answer is D.
But the correct answer is A.
The disk configuration (dynamic Vs. fixed) has little impact on the snapshot size.
However snapshotting a machine whilst it is running means a RAM dump is also saved to preserve the systems running state at that moment. That requires as much disk space as RAM being used at that time. This is avoided if the machine is shutdown first, reducing the snapshot size by a great deal.
QUESTION 386
You have a server named Serverl that runs Windows Server 2012 R2.
You try to install the Microsoft .NET Framework 3.5 Features feature on Serverl, but the installation fails repeatedly.
You need to ensure that the feature can be installed on Serverl.
What should you do?
A. Run the Add-AppxProvisionedPackage cmdlet.
B. Disable User Account Control (UAC).
C. Connect Serverl to the Internet.
D. Remove the .NET Framework 4.5 Features feature.
Answer: C
QUESTION 387
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has the Hyper-V server role installed.
An iSCSI SAN is available on the network.
Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4.
You create a LUN on the SAN to host the virtual hard drive files for the virtual machines.
You need to create a 3-TB virtual hard disk for VM1 on the LUN. The solution must prevent VM1 from being paused if the LUN runs out of disk space.
Which type of virtual hard disk should you create on the LUN?
A. Fixed-size VHDX
B. Dynamically expanding VHDX
C. Fixed-size VHD
D. Dynamically expanding VHD
Answer: A
QUESTION 388
Hotspot Question
You have a Hyper-V host named Hyperv1 that runs Windows Server 2012 R2. Hyperv1 hosts a virtual machine named Server1. Server1 uses a disk named Server1.vhdx that is stored locally on Hyperv1.
You stop Server1, and then you move Server1.vhdx to an iSCSI target that is located on another server.
You need to configure Server1 to meet the following requirements:
– Ensure that Server1 can start by using Server1.vhdx.
– Prevent Server1.vhdx from consuming more than 500 IOPS on the iSCSI target.
Which two objects should you configure?
To answer, select the appropriate two objects in the answer area.
Answer:
QUESTION 389
You have a Hyper-V host named Server1 that runs Windows Server 2012 R2. Server1 has the virtual switches listed in the following table.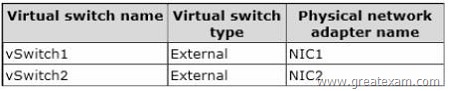
You create a virtual machine named VM1. VM1 has two network adapters. One network adapter connects to vSwitch1. The other network adapter connects to vSwitch2.
You configure NIC teaming on VM1.
You need to ensure that if a physical NIC fails on Server1, VM1 remains connected to the network.
What should you do on Server1?
A. Run the Set-VmNetworkAdapter cmdlet.
B. Create a new virtual switch on Server1.
C. Modify the properties of vSwitch1 and vSwitch2.
D. Add a new network adapter to VM1.
Answer: A
QUESTION 390
Your network contains an Active Directory domain named adatum.com. The domain contains a member server named Host1. Host1 runs Windows Server 2012 R2 and has the Hyper-V server role installed.
Host1 hosts two virtual machines named VMS and VM6. Both virtual machines connect to a virtual switch named Virtual 1.
On VM5, you install a network monitoring application named Monitor1.
You need to capture all of the inbound and outbound traffic to VM6 by using Monitor1.
Which two commands should you run from Windows PowerShell? (Each correct answer presents part of the solution. Choose two.)
A. Get-VM “VM6” | Set-VMNetworkAdapter-IovWeight 1
B. Get-VM “VM5” I Set-VMNetworkAdapter -IovWeight 0
C. Get-VM “VM5” | Set-VMNetworkAdapter -PortMirroring Source
D. Get-VM “VM6” | Set-VMNetworkAdapter -AllowTeaming On
E. Get-VM “VM6” | Set-VMNetworkAdapter -PortMirroring Destination
F. Get-VM “VM5” | Set-VMNetworkAdapter -AllowTeaming On
Answer: CE
Explanation:
-PortMirroring specifies the port mirroring mode for the network adapter. This can be set to None, Source, and Destination.
If set to Source, a copy of every network packet it sends or receives is forwarded to a virtual network adapter configured to receive the packets. If set to Destination, it receives copied packets from the source virtual network adapter.
In this scenario, VM5 is the destination which must receive a copy of the network packets from VM6, which s the source.
http://technet.microsoft.com/en-us/library/hh848457.aspx
At GreatExam, we are positive that our Microsoft 70-410 preparation material with questions and answers PDF provide most in-depth solutions for individuals that are preparing for the Microsoft 70-410 exam. Our updated 70-410 braindumps will allow you the opportunity to know exactly what to expect on the exam day and ensure that you can pass the exam beyond any doubt.