Microsoft 70-417 is often called the hardest of all Microsoft exams. GreatExam helps you kill the Microsoft 70-417 exam challenge and achieve the perfect passing score with its latest practice test, packed into the revolutionary interactive VCE. This is the best way to prepare and pass the 70-417 exam.
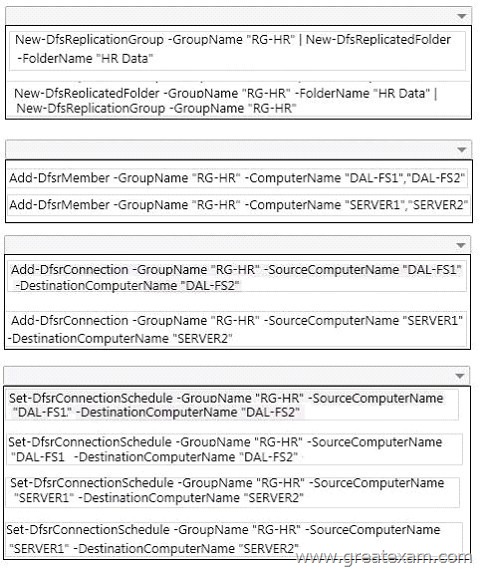
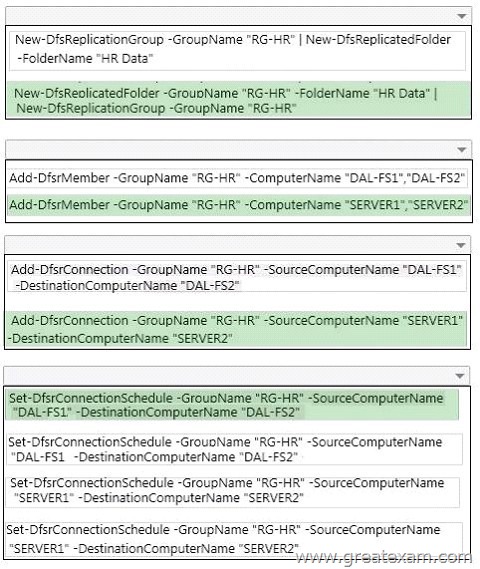
QUESTION 401
Hotspot Question
You need to create a script to deploy DFS replication.
Which Windows PowerShell commands should you add to the script? To answer, select the appropriate Windows PowerShell commands in each list in the answer area.
QUESTION 402
Note: This question is part of a series of questions that use the same or similar answer choices.
An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains one Active Directory domain named contoso.com.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01.
You have a domain controller named DC5 that has the Server Graphical Shell disabled.
You create an orgranizational unit (OU) named OU1.
From DC5, you you need to create 50 new users accounts in OU1.
What tool should you use?
A. the ntdsutil command.
B. the Set-ADDomain cmdlet.
C. the Install-ADDSDornain cmdlet.
D. the dsadd command.
E. the dsamain command.
F. the dsmgmt command.
G. the net user command.
H. the Set ADForest cmdle
Answer: D
QUESTION 403
Note: This question is part of a series of questions that use the same or similar answer choices.
An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains one Active Directory domain named contoso.com.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01.
The domain contains an administrator account named Admin1.
You need to prevent Admin1 from creating more than 100 objects in the domain partition.
Which tool should you use?
A. the ntdsutil command.
B. the Set-ADDomain cmdlet.
C. the Install-ADDSDornain cmdlet.
D. the dsadd command.
E. the dsamain command.
F. the dsmgmt command.
G. the net user command.
H. the Set ADForest cmdlet.
Answer: D
QUESTION 404
Note: This question is part of a series of questions that use the same or similar answer choices.
An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains one Active Directory domain named contoso.com.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01.
You plan to replace a domain controller named DC1.
DC1 has the schema operations master role.
You need to transfer the schema master role to another domain controller named DC10 before you remove Active Directory from DC1.
Which tool should you use?
A. the ntdsutil command.
B. the Set-ADDomain cmdlet.
C. the Install-ADDSDornain cmdlet.
D. the dsadd command.
E. the dsamain command.
F. the dsmgmt command.
G. the net user command.
H. the Set ADForest cmdlet.
Answer: A
QUESTION 405
Note: This question is part of a series of questions that use the same or similar answer choices.
An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains one Active Directory domain named contoso.com.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01.
You need to ensure that when administrators create users in contoso.com, the default user principal name (UPN) suffix is litwareinc.com.
Which cmdlet should you use?
A. the ntdsutil command.
B. the Set-ADDomain cmdlet.
C. the Install-ADDSDornain cmdlet.
D. the dsadd command.
E. the dsamain command.
F. the dsmgmt command.
G. the net user command.
H. the Set ADForest cmdlet.
Answer: H
Explanation:
https://technet.microsoft.com/en-us/library/ee617221.aspx
With this command, you modify UPN sufix for entire forest
QUESTION 406
Note: This question is part of a series of questions that use the same or similar answer choices.
An answer choice may be correct for more than one question in the series. Each question is independent of the other questions in this series. Information and details provided in a question apply only to that question.
Your network contains one Active Directory domain named contoso.com.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01.
You need to add an RODC to the domain by using the Install From Media (IFM) option.
Which tool should you use to create the media?
A. the ntdsutil command.
B. the Set-ADDomain cmdlet.
C. the Install-ADDSDornain cmdlet.
D. the dsadd command.
E. the dsamain command.
F. the dsmgmt command.
G. the net user command.
H. the Set ADForest cmdlet.
Answer: A
QUESTION 407
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1. Server1 runs Windows Server 2012 R2.
You need to create a 3-TB virtual hard disk (VHD) on Server1.
Which tool should you use?
A. Server Manager
B. Share and Storage Management
C. Computer Management
D. File Server Resource Manager (FSRM)
Answer: C
Explanation:
From Computer Management, click on Disk Management on left pane and wait for the list of drives to refresh. Once the list of drives appear in the middle pane, right click Disk Management and select Create VHD.
QUESTION 408
Your network contains one Active Directory domain named contoso.com.
The domain contains 2,000 client computers used by students.
You recently discover an increase in calls to the helpdesk that relate to security policy to meet the following requirement:
– Modify the UserName of the built-in account named Administrator
– Support a time mismatch between client computers and domain controllers of up to three minutes.
Which Two security settings should you modify?
A. Account Policies
B. Password Policy
C. Account Lockout Policy
D. Kerberos Policy
E. Local Policies
F. Audit Policy
G. User Rights Assignment
H. Security Options
Answer: DH
QUESTION 409
Your network contains an Active Directory domain named contoso.com.
You create a software restriction policy to allow an application named App1 by using a certificate rule.
You need to prevent the software restriction policy from applying to users that are members of the local Administrators group.
What should you do?
A. Modify the rule for App1
B. Modify the Enforcement Properties
C. Modify the Security Levels.
D. Modify the Trusted Publishers Properties
Answer: B
Explanation:
https://technet.microsoft.com/en-us/library/cc776536(v=ws.10).aspx
QUESTION 410
Your network contains one Active Directory domain named contoso.com.
The domain contains 20 member server and five domain controllers. All domain controllers run Windows Server 2012 R2. The domain contains 500 client computers.
You plan to deploy a domain controller for contoso.com in Microsoft Azure.
You need to prepare the enviroment for the planned deployment. The solution must ensure that the domain controller hosted in Azure always has the same IP address.
Which two actions should you perfomr? Each correct answer presents part of solution.
A. Deploy a site-to-site virtual private network (VPN).
B. From an Azure virtual machine, run the Set-NetIPAddress cmdlet.
C. From an Azure virtual machine, run the Set-AzureStaticVNetIP cmdlet.
D. From a domain controller, run the Set-NetIPAddress cmdlet.
E. From a domain controller, run adprep.exe.
Answer: AC
QUESTION 411
You have a server named Server1 that runs Windows Server 2012 R2.
You apply a secerity policy to Server1 by using the Security Configuration Wizard (SCW).
You plan to roll back the security policy.
You need to indentify the setting that are prevented from rolling back using the SCW.
Which setting shoulld you identify?
A. the outbound authentication methods
B. the system access control lists (SACLs)
C. the service startup mode
D. the network security rules
Answer: B
QUESTION 412
Hotspot Question
The domain contains an organizational unit (OU) named Groups that contains a universal security named Group1.
You run the following command from Windows PowerShell.
Get-ADGroup Group1 -properties managedby | New-ADGroup -name “Group2” -SamAccountName group2 -groupcategory distribution -groupscope global
You need to identify which properties of group1 will be copied to Group2.
What should you identify? To answer, select the appropriate options in the answer area.
The group type
Will be different from Group1
Will be the same as Group1
The group scope
Will be different from Group1
Will be the same as Group1
The managed by attribute
Will be different from Group1
Will be the same as Group1
The permission assigned to group1
Will be different from Group1
Will be the same as Group1
Answer:
The group type Will be different from Group1
The group scope Will be different from Group1
The managed by attribute Will be the same as Group1
The permission assigned to group1 — this is either a typo or a trick question the command would not change permissions on group 1 nor would it copy the permissions from group1 to group2.
QUESTION 413
You have a server named Server1 that Runs Windows Server 2012 R2.
You configure IPSec rules for connections to Server1.
On Server1, you plan to create an inbound firewall rule that contains the following settings:
– Allows inbound connections to an application named App1.exe
– Applies to the domain profile
– Overrides any block rules
You need to identify the minimum information required to create the rule.
Which two pieces of information should you identify? Each correct answer presents part of the solution.
A. the list of Active Directory users who are authorized to use the application.
B. the list of computers that are authorized to use the application.
C. the hash of the application.
D. the local path of the application.
E. the name at the IPSec policies that apply to Server1
Answer: BD
Explanation:
B: To overwritte deny rule, you need to specify the list of computers.
D: For NAMED application you need local path to the app, in other case you will specify all programs, in answer must be a match.
QUESTION 414
You have a server named Server1 that runs Windows Server 2012 R2.
You apply a security policy to server1 by using the Security Configuration Wizard (CWM).
You plan to roll back the security policy.
You need to identify the settings that are prevented from rolling back running the CWM
Witch settings should you identify.
A. The secure startup order
B. The outbound authentication methods
C. The network security rules
D. The system access control list (SAClist)
Answer: D
Explanation:
System Keeps Auditing After Rollback
In the auditing section of SCW there is an option to include the SCWAudit.inf template. If you do so, SCW configures System Access Control Lists (SACL) on a number of files. Without this template SCW will configure the system to perform object access auditing but since no files have SACLs on them by default, no file access will actually be audited.
If you apply a policy with this option turned on and you subsequently roll back the policy the SACLs will remain on the system. Consequently, if the system is configured to perform Object Access Auditing you will find auditing events in the Security Event Log. This is by design. SCW is not designed to roll back ACLs. To clear these SACLs you would need to manually restore any pre- existing SACLs. As long as these were defined in a security template doing so is a simple matter of re-applying that security template.
http://blog.netwrix.com/2015/06/19/configure-audit-policy-and-security-using-security-configuration-wizard/
QUESTION 415
Your network contains an active directory domain named contoso.com. The domain consists 20 member Servers and 5 domain controllers. All servers run Windows Server 2012 R2.
The domain contains 500 client computers.
You plan to deploy a domain controller for contoso.com in Microsoft Azure.
You need to prepare the conversation for planned deployment. The solution should ensure that the domain controller hosted in Azure always have the same IP address.
Which two actions should you perform? Each correct answer is a part of the solution.
A. From an Azure virtual machine run the Set-AzureStaticVNetIP cmdlet
B. Deploy a Side by side virtual private network (VPN)
C. From Azure virtual machine run the Set-NetIPAuthentication cmdlet
D. From an domain controller run the Set-NetIPAdresses cmdlet
E. From an domain controller run adprep.exe
Answer: AB
QUESTION 416
You have a Hyper-V host named Server1 that runs Windows Server 2012 R2. Server1 host 50 virtual machines that run Windows Server 2012 R2.
You enable and configure enhanced session mode on Server1.
you need to identify a new functionality available for the virtual machines hosted on Server1.
What should you identify?
A. Smart card authentication using virtual machine connections
B. Redirection of RemoteFX USB drivers by using reomte desktop connections
C. Redirection of RemoteFX USB drivers using virtual machine connections
D. Smar card authentication using the remote desktop client.
Answer: A
QUESTION 417
You have a DNS server named DNS1 that runs windows server 2012 R2.
DNS1 is used to resolve the names of internet resources by using several DNS forwarders.
You need to prevent DNS1 from performing iterative queries if the DNS forwarders are unable to reslove the queries.
Which cmdlet should you use?
A. Remove-DNSServerRootHint
B. Set-DNSServerPrimaryZone
C. Ser-DNSServerGlobalNameZone
D. Unregister-DNSserverDrirectoryPartition
Answer: A
QUESTION 418
Your network contains an Active Directory domain named contoso.com.
The domain contains a DHCP server named Server1 that runs Windows Server 2012 R2.
You create a DHCP scope named Scope1. The scope has a start address of 192.168.1.10. an end address of 192.168.1.50, and a subnet mask of 255.255.255.192.
You need to ensure that Scope1 has a subnet mask of 255.255.255.0.
What should you do first?
A. From the DHCP console, modify the properties of Scope1.
B. From the DHCP console, modify the Scope Options of Scope1.
C. From Windows PowerShell. run the Remove-DhcpServerv4Scope cmdlet.
D. From the DHCP console, reconcile Scope1.
Answer: C
QUESTION 419
RODC comes with a number of features that focus on heightened security with limited functionality to remote office users. Which of the following are features of RODC?
A. Filtered Attribute Sets
B. Read-Only DNS
C. Unidirectional Replication
D. All of these
Answer: D
QUESTION 420
Sometimes it’s important to remove an RODC from your forest or domain. However, it’s important that you follow a simple rule whilst removing RODC’s. What is this rule?
A. All RODC’s must be detached before removing a final writable domain controller
B. All writable domain controllers must be removed before RODC’s can be detached
C. Your forest must only consist of RODC’s if you want to remove them
D. There are no rules for removing RODC’s
Answer: A
GreatExam VCE dumps only include latest 70-417 exam questions, so you will know exactly what to expect on your real exam. GreatExam products are industry’s most reliable and convenient tool to prepare for the 70-417 exam.